E.R. Jahna Industries, a Florida-based sand mining company, needed to enhance its IT infrastructure and cybersecurity. With limited internal resources, it turned to
Thrive for a comprehensive IT and cybersecurity solution. Thrive delivered a multi-layered cybersecurity framework, migrated critical servers to its private Cloud, and implemented detection and response systems. This partnership allowed E.R. Jahna Industries to safeguard its operations, reduce risks, and free up internal resources.
The Challenge
E.R. Jahna Industries, a leader in sand mining, plays a crucial role in various industries across Florida and Southeast Georgia markets, including construction, manufacturing, and infrastructure. However, their Director of IT quickly realized they were falling behind in terms of security and technology. With a small internal team, E.R. Jahna Industries needed a trusted partner to elevate IT operations and protect assets. That’s where Thrive came in.
Why Thrive Was Chosen
After assessing their security posture and IT environment, E.R. Jahna Industries’ Director of IT, Thomas Single, knew that addressing cybersecurity was a priority. Thrive, with its reputation and existing relationship, was the ideal partner. But it wasn’t just about the technical capabilities but about trust and partnership.
Thrive was chosen not just because of the technology or cost. It was more about the relationship. I consider them partners, and I knew they could help us get where we needed to be,” Single explained.
Strategic Deployment of Advanced Security Measures
Thrive implemented a comprehensive solution that began with building an Active Directory domain, migrating servers to Thrive’s private Cloud, and enhancing detection and response systems. Their approach included multiple layers of security, addressing infrastructure weaknesses, and protecting E.R Jahna Industries’ operations from potential threats.
“We didn’t have an Active Directory domain in place, and everyone had too much access. Thrive stood up the domain, migrated all our PCs, and helped us every step of the way,” said Single. “They were with us through the entire process, ensuring we had the right tools and systems in place.”
Additionally, Thrive took over the management of cybersecurity training for E.R. Jahna Industries employees, relieving internal resources and providing better coverage with ongoing threat monitoring.
Thrive’s Impact
Since partnering with Thrive, E.R. Jahna Industries has significantly improved its IT security and operations. Enhanced detection systems quickly neutralize potential threats, giving the team a sense of calm and confidence. The migration of critical infrastructure to Thrive’s private Cloud has freed up internal resources, allowing the company to focus on core business activities.
“Since partnering with Thrive, we’ve not only enhanced our security posture, but we’ve also streamlined our IT operations. They’ve helped us prevent issues before they become real problems, which has had a measurable impact on the stability and efficiency of our business.”

“Thrive’s team is at the top of their game. The handoff between the project and support teams was seamless, and every resource we worked with was professional, knowledgeable, and easy to work with.” When I first joined the company and did the assessment, I did not sleep at night, thinking we would have a problem, and I was just waiting for that ticking time bomb. Since we put all the tools in place and engaged with Thrive, I sleep at night. I sleep very well at night.” ~ Thomas Single, IT Director, E.R. Jahna Industries
About Thrive
Thrive delivers global technology outsourcing for cybersecurity, Cloud, networking, and other complex IT requirements. Thrive’s NextGen platform enables customers to increase business efficiencies through standardization, scalability, and automation, delivering oversized technology returns on investment (ROI). They accomplish this with advisory services, vCISO, vCIO, consulting, project implementation, solution architects, and a best-in-class subscription-based technology platform. Thrive delivers exceptional high-touch service through its POD approach of subject matter experts and global 24x7x365 SOC, NOC, and centralized services teams. Learn more at www.thrivenextgen.com or follow us on LinkedIn.
Thrive Acquires Michigan-based Safety NetLeading Global MSP/MSSP Establishes Midwest Presence
Boston, MA, October 16, 2024 – Thrive, a global technology outsourcing provider for cybersecurity, Cloud, and IT managed services, today announced the acquisition of Safety Net, a leading Michigan-based IT services firm. With the acquisition, Thrive will expand its reach to the Midwest, enabling Safety Net’s customers to have access to Thrive’s industry-leading global Security Operation Center (SOC) & Hybrid Cloud solutions.
Thrive’s mission is to empower their customers to harness the promise of technology, achieving success by proactively utilizing IT, cybersecurity, and Cloud best practices to drive ROI and desired business outcomes for their valued clients. The union of Thrive and Safety Net will ensure that customers in Michigan will continue to enjoy the exceptional high-touch managed services they’ve come to love, along with newly enhanced 24x7x365 global SOC, cybersecurity, and hybrid cloud resources.
“Safety Net’s similar business philosophies and company culture are a perfect fit as our Midwest regional platform,” said Rob Stephenson, CEO of Thrive. “Their product and service sophistication, client first mentality, and dedicated team of talented engineers will allow Thrive to grow in Michigan, as well as expand deeper into other Midwest markets with their strong leadership team.”
This latest acquisition comes at a time of strong growth for Thrive, having completed eleven previous acquisitions over the past two years, most recently acquiring The Longleaf Network. In addition to geographic expansion, Thrive continues to grow its service offerings to meet the growing needs of its customers, including Thrive Incident Response & Remediation, Managed Detection and Response, and Dark Web Monitoring.
“With over two decades of providing strategic IT solutions to Michigan businesses, our team is excited to accept the challenge of accelerating our growth to become the premier managed services provider in the Midwest,” said Tim Cerny, CEO of Safety Net. “Our mission seamlessly aligns with Thrive’s commitment to deliver the best technology outcomes for customers. With their partnership, we look forward to elevating our technology capabilities to fulfill the rapidly emerging IT complexity that our clients face.”
To learn more about Thrive and its offerings, visit the website.
About Thrive
Thrive delivers global technology outsourcing for cybersecurity, Cloud, networking, and other complex IT requirements. Thrive’s NextGen platform enables customers to increase business efficiencies through standardization, scalability, and automation, delivering oversized technology returns on investment (ROI). They accomplish this with advisory services, vCISO, vCIO, consulting, project implementation, solution architects, and a best-in-class subscription-based technology platform. Thrive delivers exceptional high-touch service through its POD approach of subject matter experts and global 24x7x365 SOC, NOC, and centralized services teams. Learn more at www.thrivenextgen.com or follow us on LinkedIn.
Contacts
Amanda Maguire
Digital Divide: UK’s Cyber Security Stronger, but Are Businesses Still Fragile?
Should we relax? It’s official: Britain has made significant recent progress regarding its resilience against cyber-attacks. In the July King’s Speech, a new bill was outlined to further protect the critical infrastructure and digital services that Brits rely on daily.
This is a significant step in addressing the rapidly growing number of relentless attacks that devastate our health services, government departments, educational and democratic institutions, and even smaller local authorities. Yet, the urgency of the situation is clear, as we have increasing evidence of the fragility of the UK’s cyber infrastructure – and the aggressive threats the country is facing.
What will this bill do?
The crucial updates made to the existing framework will expand its remit, protecting more UK digital services and supply chains. Regulators will also reportedly be put on a ‘strong footing’ to guarantee the implementation of safety measures, including cost recovery mechanisms and additional powers that facilitate vulnerability investigation.
This legislation is a beacon of hope, as it mandates increased incident reporting to give government teams more accurate data on cyber threats. This includes where a business has been a ransom victim, improving their understanding of current threats and highlighting potential further ones by widening the net regarding the nature of incidents that entities are to report.
This bill will extend UK-wide and is fully endorsed by the NCSC. Its CEO, Felicity Oswald, warned that the UK’s essential service providers cannot afford to ignore these threats.
Why the new legislation?
Two government reviews found that the original frameworks had a positive impact, but progress needed to be made faster to keep up with the rapidly evolving threats to the nation. Over 50% of essential service operators have updated their processes and policies since the creation of the cyber regulations in 2018, hardly enough to match the required pace.
In June, cybercriminals struck the NHS, postponing critical appointments and procedures at some of London’s most significant hospitals, such as Guy’s, St Thomas’, and King’s College. Last year, we saw Sefton, a village in Merseyside, fight off 30,000 cyber-attacks on its council infrastructure per month, with the BBC reporting last month that councils remain at the mercy of criminal hackers. These attacks are not just statistics, they are real and they are affecting businesses and services that we rely on.
This reform is well-needed, with countless examples of attacks like these affecting millions of Brits. However, despite these recent changes, businesses remain fragile throughout the country.
New vulnerabilities
In 2023, the UK led the list of global data breaches. The country was shaken by the largest cyberattack in 2023, as cyber protection firm DarkBeam failed to protect 3.8 billion records. The leak was uncovered by the CEO of SecurityDiscovery, Bob Diachenko, who informed the company of its leak. They promptly addressed and fixed the leak. According to Diachenko, this type of data leak is usually caused by human error, such as forgetting to encrypt data following maintenance.
We also have witnessed a spike in attacks on a new sector: the construction industry. A new report by risk advisory firm Kroll has indicated that cyber-attacks on construction companies doubled in the first quarter of 2024 compared to last year. Kroll advised this increase was most probably down to the ‘sophistication of business email compromise for either financial gain or as a pivot into downstream attacks.’
The company confirmed that the construction sector had seen steady growth in email compromise from 2023 to 2024. According to Construction News5, on-the-go work culture is the culprit behind doubling the frequency of these attacks. Kroll warned: ‘An employee may be more likely to fall for a phishing lure if they are receiving the email on the road, making them potentially less vigilant about the signs of fraud.’
SMS and voice-based tactics have been reported, which raises concern surrounding the potential use of deep fakes and other AIs to further streamline phishing attacks. An insider threat case examined by Kroll earlier this year saw an employee impersonated, a method AI could efficiently utilise.
Arup, a British multinational firm headquartered in London providing services across the building sector, confirmed in May of this year that it was the victim of a £20 million deep fake fraud attack after an employee was manipulated into sending over the sum via an AI- generated video call. The attackers posed as ‘senior officers of the company’ to dupe their way to the money. Arup’s global CIO, Rob Greig, stated that the company had been the victim of a barrage of attacks, increasing both in potency and frequency, in the months leading up to the large-scale attack.
Greig’s quote to Building.co.uk illustrates the ordeal: ‘This is an industry, business, and social issue, and I hope our experience can help raise awareness of the increasing sophistication and evolving techniques of bad actors.’
Police in Hong Kong, where the attack occurred, have made no arrests thus far, and the cyber-criminals are still at large.
As a chilling final example, officials have confirmed that the British critical national infrastructure (CNI) ‘could be left dangerously exposed’ if managers do not appropriately address the increasing cyber-attack threat caused by tension between Britain, China, Russia and Iran.
How fragile is the UK’s critical national infrastructure?
The BBC reported a ‘hack’ in May of this year, resulting in a ‘significant data breach’ of payroll data from the MoD. The then Defence Secretary, Grant Shapps, warned that state involvement could not be ruled out. In the days and hours following, at least two additional cyber-attacks hit the Scottish NHS and the UK Border Force.
NHS Dumfries and Galloway revealed that children’s mental health data had been published, and Border Force e-passport gates ceased to work at Britain’s major airports. Considering simmering tensions with other states and escalating wars in Ukraine and Palestine, infrastructure providers are left concerned about potential future attacks.
The lines between political interference and targeted cyber attacks are starting to blur. Considering this, coupled with more and more sectors finding themselves the new victim in the crosshairs of increasingly sophisticated and ruthless attacks, do not let your company be next.
If you are targeted by a bad actor, do you have a well-rehearsed incident response plan in place? Contact Thrive to learn how we can help fortify your digital approach and keep you and your team safe from an ever-evolving threat landscape. We specialise in helping medium sized businesses fortify their critical cyber infrastructure.
Thrive Spotlight: Wendy Davis – Corporate Accounting SupervisorWelcome back to another installment of our “Thrive Spotlight” blog series.
Our featured employee is Wendy Davis, Corporate Accounting Supervisor. Wendy is responsible for month end closing and assisting with the accounts payable processing as well as maintaining and submitting Government and FCC compliance reporting.
Wendy lives in Lakeland, Florida and works out of our Lakeland office. When Wendy is not working, she loves spending time with her family and friends. She also loves traveling any chance she gets.
Hi Wendy! Can you tell us about your background and how you came to Thrive?
I worked as the Controller at DSM Technology Consultants for 8 years. When DSM was acquired by Thrive nearly 2 years ago, I came on board to the finance department at Thrive.
Where did you go to school or get training?
I attended Webber International University in Florida.
What do you most enjoy about working for Thrive?
I enjoy the team I get to work with and all the new knowledge I’ve gained.
Are there any recent exciting projects at Thrive you can tell us about?
We are working on becoming more automated and less manual.
Are you interested in learning more about Thrive? Click here!
Don’t forget to follow us on Twitter and LinkedIn for the latest news, and continue checking our blog for more in our “Thrive Employee Spotlight” series. Until next time…
UK’s AI Ambitions: A Double-Edged Sword?As the UK strives to establish itself as a global AI superpower, a robust cybersecurity stance is paramount. A recent Mission Critical report by Microsoft revealed that a mere 13% of companies are resilient to cyberattacks. This report is a wake-up call to understand the gravity of the UK’s cybersecurity situation.
Microsoft tested company resilience with members of Goldsmiths University London using a model created by Chris Brauer (Director of Innovation at its Institute of Management Studies). The study revealed that 48% of UK businesses are vulnerable to attacks.
The report also shows that the UK is currently in a position to be the global leader in cybersecurity. Still, it’s missing out on a £52 billion dividend by not using these tactics, cutting the annual cost of cyber-attacks from £87 billion a year.
Paul Kelly, the director of Microsoft UK’s security business group, highlights AI’s potential to bolster cybersecurity. He states, “AI has the power not only to enhance the security of your business and data but also to significantly mitigate the impact of a cyber-attack on your bottom line.” This potential of AI to strengthen security should instil a sense of confidence in UK businesses.
As reported by the NCSC, the main risks with AI are likely to be from two types of attacks. The first is prompt injection attacks, one of the most widely reported weaknesses in large language models (LLMs).
The attack occurs through fabricated instructions inserted by a cyber attacker designed to make the AI model behave unintendedly. This includes revealing confidential information, generating offensive content, or triggering unethical actions in a system that accepts unchecked input.
The second attack the NCSC warns of is a data poisoning attack, which occurs when a criminal tampers with the training data of an AI model to carry out an attack – affecting security and bias.
As LLMs become increasingly familiar with passing data to third-party applications and services, the risks from these attacks will grow, requiring an appropriate response. So, what response does the NCSC recommend?
The Guidelines for Secure AI System Development, published by the NCSC and developed with the US’s Cybersecurity and Infrastructure Security Agency (CISA) and agencies across 17 other nations, advise on how medium-sized businesses can manage AI in a way that ensures everyone reaps its benefits and doesn’t fall victim to its many dangers. Executives must understand the potential impact on their organisation if an AI system’s security is breached, affecting its reliability, accessibility, or data privacy.
Businesses must have a well-prepared response strategy in place for potential cyber incidents. Ensuring compliance with relevant laws and industry standards when managing AI-related data is essential. Three key questions to consider regarding your organisation’s AI safety are:
- How would you respond to a severe security incident involving an AI tool?
- Is everyone involved in AI deployment (including senior executives and board members) familiar enough with AI systems to assess the potential dangers? This understanding is beneficial and crucial in the current cybersecurity landscape. What’s the worst-case scenario (regarding reputation and operations) if an AI tool in your company encounters an issue?
Until recently, most cybercriminals needed to carry out attacks themselves, but rapidly evolving access to generative AI enables automatic attack research and execution. This presents a new and growing threat to your business.
One of its primary capabilities is ‘data scraping’ when information from public sources (social media and company websites) is collected and analysed. This approach dangerously invents hyper-personalised, timely and relevant messages that form the basis of phishing attacks and any attack that employs social engineering techniques.
Another notable trait of AI algorithms is that they gather intel and adapt in real time. This has positive outcomes, such as providing more precise information for corporate users. But it’s also a double-edged sword, as it aids cybercriminals enormously in refining the efficacy of their techniques to avoid detection and steal as much data as possible.
AI can swiftly pinpoint high-value individuals within an organisation. These could include members with access to sensitive staff or client data, limited technological expertise, broad or unrestricted system access, or valuable relationships that could be exploited to reach other critical targets.
The latter is expected, with AI-driven social engineering attacks leveraging AI algorithms to manipulate human behaviour to obtain sensitive data, money or high-value items or access to a system, database, or device. These attacks can be highly sophisticated, using AI to develop a persona to communicate effectively with a target in realistic and plausible situations that would leverage contacts, complete with false audio or video, to engage them.
Since two-thirds of security leaders expect offensive AI to be the norm for cyberattacks within a year, let’s look at some examples from close to home.
The British government has declared its intention to fund AI safety research with £8.5m to tackle online threats, including deepfakes. The declaration prompted a dire warning from the NCSC in January 2024, noting that malicious AI will “almost certainly” lead to increased cyber-attack volume and impact over the next two years, particularly those featuring ransomware. 30% of security professionals surveyed in the compliance specialist ISMS’s new research claimed to have experienced a deepfake-related incident in the past year.
Protect your business from evolving AI-driven cyber threats with Thrive’s cutting-edge security solutions. Our expert team, equipped with cutting-edge technology, is experienced in working alongside companies to safeguard data, ensure compliance and keep you ahead of the curve. Don’t wait for an attack to expose vulnerabilities – let’s fortify your defences. Download our AI policy template to get started today.
Cybersecurity Awareness Month: PhishingThe main element behind successful phishing attacks is taking advantage of normal human behavior. This issue shows that just one mistake in the cyber equation can result in a major breach, and the advancement of generative AI has made phishing messages more sophisticated, increasing the overall risk. Third-party email filtering solutions and regular security awareness training are the most effective ways to mitigate phishing attacks. Regular training, along with phishing tests and targeted retraining, are proven methods to reduce user credential leaks from this very common attack method.
Learn how Thrive’s Proactive Cybersecurity Response Team Prevents Ransomware AttackRansomware has become a constant threat in today’s world of emerging technologies. Threat actors are increasingly using this attack method to cripple corporate infrastructures, extract large sums of money as payment, and damage their reputation.
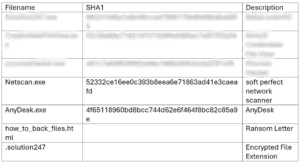
Thrive’s Cybersecurity Incident Response Team (CIRT) recently prevented a threat actor from accomplishing those goals. A client who had not invested in Endpoint Detection and Response (EDR) solutions, was attacked. Despite the lack of endpoint tooling and customer documentation, Thrive’ s CIRT quickly responded to the developing incident, gathered crucial forensic artifacts, and launched an in-depth investigation. Thanks to CIRT’s methodical investigation it was determined a threat actor had encrypted numerous files, appending the extension .solution247 to each file.
Additionally, every file directory contained a file named how_to_back_files.html, which included an extortion message from the attackers, detailing their ransom demands and instructions for potentially recovering the encrypted data.
Further analysis revealed that Remote Desktop Protocol (RDP) connections to the impacted server came from VPN during the period of compromise. A review of the firewall logs indicated that the user account used to authenticate to the VPN was compromised through a distributed brute-force attack.
Using the low privilege VPN credentials, the adversaries were able to gain access to a domain controller and file server. Once they obtained access to these systems, they quickly installed AnyDesk, a commercially available remote access tool, likely used to establish persistent access. Shortly after, they executed tools such as CredentialFileView, SoftPerfect Network Scanner, and Process Hacker.
The SoftPerfect Network Scanner was found to have accessed a file at the following location: C:\Users\Redacted\Documents\anetscan (6)\anetscan (5)\anetscan (4)\automim\!logs\Passwords.txt. This file was part of an automated process for scanning and attempting authentication on other network resources. Evidence of access attempts to the NTDS.dit, a “crown jewel” asset for an attacker, was also discovered during this period. Subsequently, the threat actors successfully gained access to several administrator accounts
A file named Solution247.exe was downloaded to C:\Users\Redacted\Documents\. Solution247.exe—was identified as the BabyLockerKZ ransomware variant—was extracted. Prior to the file encryption, there was evidence of exfiltration from the compromised server to an IP address associated with the internet service provider 59telecom.ru over port 21 (FTP). Upon execution, Solution247.exe added itself to the current user’s Run key to maintain persistence with the following command:
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v sm /t REG_SZ /d “C:\Windows\System32\ Solution247.exe” /f
The ransomware then forcefully terminated critical processes essential for system operation and security, including SQL Server, Windows Defender, user login processes, and print services:
cmd.exe /c taskkill /F /IM sqlservr.exe /T
taskkill /F /IM msmpeng.exe /T
taskkill /F /IM winlogon.exe /T
taskkill /F /IM spoolsv.exe /T
Next, Solution247.exe disabled key services using net stop commands, disrupting crucial system operations, including antivirus and backup systems:
net stop “Windows Defender Antivirus”
net stop “SQL Server (MSSQLSERVER)”
net stop “Windows Backup”
After disabling these defenses, Solution247.exe began encrypting files across multiple drives using cipher.exe commands:
cipher /e /s:C:\
cipher /e /s:D:\
To further hinder recovery efforts, it deleted volume shadow copies with.
vssadmin delete shadows /all /quiet
Despite the threat actors’ efforts to hinder recovery, the client had invested in Thrive’s Veeam backup solution. After receiving a detailed timeline of the intrusion, they were able to confidently restore their data and ensure the integrity of the impacted servers.
Indicators of compromise:
Would you like to learn more about the indicators of compromise we found? Reach out today and we will provide the full list to you.
Today’s complex cyber threats require a multi-solution approach combined with advanced skill sets and real-time, 24/7 monitoring. Thrive’s leading security platform integrates best in breed technologies, analyzing attack data with AI and certified security analysts to prevent the impacts from threats allowing you to focus on critical business outcomes.
Our security team combines the power of automation for rapid response and remediation with the expertise of our staff to address complex issues intelligently. We are ready to help.
G. Modiano Secures Global Operations with Thrive’s Advanced IT and Security Solutions Download Now
G. Modiano, one of Europe’s largest wool manufacturers, needed to modernise its IT systems without disrupting daily operations. To help tackle this, they partnered with Thrive. Thrive stepped in to secure and streamline its cybersecurity posture, ensuring G. Modiano stayed ahead in a rapidly changing digital world while keeping its global operations running smoothly.
G. Modiano is a major player in the wool manufacturing industry, with operations spanning multiple countries. As a company deeply rooted in industrial production, its IT infrastructure supports both corporate operations and factory machinery across jurisdictions. Over the past couple of years, Thrive has been an instrumental partner, ensuring G. Modiano’s security framework remains robust, scalable, and ready to meet the demands of modern business operations.
Why Thrive Was Chosen
When Perry Willis, IT Director of G. Modiano, joined the company seven years ago, he recognised the need to modernise the company’s IT infrastructure. While the existing systems were functional, they were fragmented and outdated. “The infrastructure wasn’t broken, but it hadn’t moved forward with the times,” Perry explained. The company needed a forward-looking cybersecurity approach that could integrate its systems while maintaining seamless operations.
After evaluating several providers, Perry selected Thrive for their ability to deliver reliable, repeatable security solutions with minimal complexity. Thrive’s reputation, strengthened by its acquisition of the UK-based ONI, and their proactive, customer-focused approach made them the clear choice for G. Modiano’s evolving needs.
Strategic Deployment of Advanced Security Measures
Thrive began its partnership with G. Modiano by conducting penetration testing to identify vulnerabilities within the company’s IT infrastructure. Unlike previous providers, Thrive’s approach stood out due to their transparent and straightforward project management. Perry appreciated the clear feedback, stating, “The project management was really good, very honest…refreshing, really.” Thrive delivered detailed reports with actionable insights, without the unnecessary complexity often seen in cybersecurity evaluations, providing G. Modiano with the tools to strengthen its security posture.
One of the key challenges G. Modiano faced was managing compliance across multiple jurisdictions, given its operations in Europe and beyond. With data centres in the UK and infrastructure spread globally, ensuring adherence to regional regulations was critical. Thrive played a pivotal role in navigating these complexities, helping G. Modiano maintain compliance with regulatory requirements while securing its diverse IT infrastructure. Thrive adapted and provided solutions that ensured both security and regulatory compliance across all operational areas.
Thrive’s Impact
Beyond technical results, Thrive’s people have played a crucial role in the partnership’s success. Its project management team, particularly the dedicated account manager, has gone above and beyond to ensure G. Modiano’s unique needs were met. Thrive’s combination of cutting-edge technology and personal commitment to customer success has reinforced G. Modiano’s trust in the partnership.
Thrive didn’t just offer a one-size-fits-all service; they actively listened, responded quickly, and ensured every detail was addressed. The team’s open communication and straightforward approach made G. Modiano feel supported at every stage of the partnership.
Thrive’s success with G. Modiano goes beyond just technical results—it’s the people behind the solutions that have truly made a difference. Despite G. Modiano being a smaller business in terms of its corporate headcount, Thrive understood the complexity of its IT infrastructure and handled it with precision. Thrive’s solutions allowed Perry and his team to focus on the core business without being bogged down by the technical intricacies. “Thrive delivered exactly what they promised, on time, and without any fluff,” Perry said. That straightforward reliability is what solidified G. Modiano’s trust in Thrive. Thrive team members didn’t just deliver technology—they provided peace of mind, making G. Modiano feel confident and secure about the future

“The business outcome with Thrive wasn’t just about security; it was about having a partner who delivered consistently, streamlined our processes, and gave us full transparency into every step. We’re confident in our infrastructure now, knowing it’s well-managed and future proofed.” ~ Perry Willis, IT Director, G. Modiano
About Thrive
Thrive delivers global technology outsourcing for cybersecurity, Cloud, networking, and other complex IT requirements. Thrive’s NextGen platform enables customers to increase business efficiencies through standardization, scalability, and automation, delivering oversized technology returns on investment (ROI). They accomplish this with advisory services, vCISO, vCIO, consulting, project implementation, solution architects, and a best-in-class subscription-based technology platform. Thrive delivers exceptional high-touch service through its POD approach of subject matter experts and global 24x7x365 SOC, NOC, and centralized services teams. Learn more at www.thrivenextgen.com or follow us on LinkedIn.
Transforming Communications: mhs homes’ Transition to Thrive’s Cloud-Hosted SIP Solution Download Now
mhs homes, a leading housing association in the U.K., partnered with Thrive to upgrade from an on-premise telephony system to a Cloud-hosted SIP solution, seeking greater resilience, simpler management, and scalability. Thrive’s solution, featuring a Cisco Unified Communications Manager and an integrated contact center, ensured seamless continuity. Thrive’s responsiveness and understanding of mhs homes’ mission made the transition smooth and impactful.
mhs homes, managing over 10,000 affordable housing units in North Kent, needed to modernise its aging telephony system. Focused on providing housing solutions, they required a resilient, scalable system to meet growing needs. Thrive was chosen to implement a Cloud-hosted SIP solution to modernise communications while aligning with mhs homes’ mission of delivering value for money.
Why Thrive Was Chosen
mhs homes chose Thrive because of its ability to integrate the existing on-premise infrastructure with a new Cloud-hosted SIP solution. Thrive’s industry expertise, particularly through its acquisition of ONI, a previous partner of mhs homes, solidified the decision to continue the collaboration.
Amanda Hodge, IT Manager, explained, “Thrive stood out because of its understanding of our focus on value for money. They seamlessly combined our current technology with their Cloud solution, making the transition cost-effective and efficient.”
Strategic Deployment of Advanced Security Measures
Thrive implemented Cisco Unified Communications Manager, integrated call recording, and a contact center express to meet mhs homes’ communication needs. The redundancy allowed mhs homes to maintain full functionality, even during network outages or power disruptions.
“Moving to the Cloud relieved us of managing an on-premise infrastructure,” said Hodge. “We kept the handsets on-site, but everything else, from call management to reporting, was migrated to the Cloud. Thrive provided a resilient solution that ensured business continuity, even during challenges like the COVID-19 pandemic.”
Thrive’s Impact
The transition to a Cloud-hosted telephony solution profoundly impacted mhs homes, improving operational efficiency and system resilience.
“The biggest benefit for us has been the reduced management overhead,” Hodge shared. “With Thrive managing the system, we no longer have to worry about upgrades or outages. Even when we’ve experienced issues on our end, our telephony system has stayed up and running, allowing us to maintain communication with our tenants.”
Thrive’s ability to customise solutions and provide responsive support further strengthened the partnership, ensuring that mhs homes could focus on its core mission of providing housing to those in need.
“Thrive’s team has been great to work with. They understand our charitable goals and have tailored the solution to meet our unique requirements, ensuring we can deliver excellent service to our tenants,” Hodge concluded.

“Thrive provided us with a Cloud solution that not only modernised our telephony system but also gave us the resilience and flexibility we needed to keep serving our tenants without disruption. Their ability to customise the solution to our specific needs and mission has been invaluable.” ~ Amanda Hodge, IT Manager, mhs homes
About Thrive
Thrive delivers global technology outsourcing for cybersecurity, Cloud, networking, and other complex IT requirements. Thrive’s NextGen platform enables customers to increase business efficiencies through standardization, scalability, and automation, delivering oversized technology returns on investment (ROI). They accomplish this with advisory services, vCISO, vCIO, consulting, project implementation, solution architects, and a best-in-class subscription-based technology platform. Thrive delivers exceptional high-touch service through its POD approach of subject matter experts and global 24x7x365 SOC, NOC, and centralized services teams. Learn more at www.thrivenextgen.com or follow us on LinkedIn.
Caught in China’s Cyber Crosshairs: How Your Business Might Be ExposedFor mid-size British businesses, the cyber threat landscape has become a minefield in recent years. We have already reported on state-sponsored threats to private companies and public services. This year’s massive cyber attack on London National Health Service (NHS) hospitals by a Russian ransomware group has caused hundreds of operations to be cancelled, the need for emergency blood supplies to be found, and IT systems suspended, leading to the manual processing of patients because of a hack into the NHS supply chain.
While criminal hackers and financially motivated cybercrime groups have long plagued companies from known sources, a new and even more alarming threat has emerged: state-sponsored hacking operations backed by the Chinese government.
Recent developments have shed light on the sophisticated and persistent efforts by Chinese hackers to compromise systems, steal data, and even interfere with democratic processes across the UK and its allies. No business is immune, no matter its size or sector, so in this article, we’ll explain how you can protect your business from this imminent threat.
Investigated by the NCSC
In March 2024, the UK government took the bold step of publicly calling out China for two major cyber campaigns targeting British democratic institutions and Members of Parliament. As revealed by the National Cyber Security Centre (NCSC), a Chinese state-affiliated group gained widespread access to the systems of the Electoral Commission between 2021-2022, potentially exposing data on a whopping 40 million Britons on the electoral register. In a separate campaign in 2021, the same Chinese hacking group carried out reconnaissance against British members of parliament, particularly those outspokenly critical of Chinese government policies.
These were by no means isolated cases but rather represent, according to the Foreign Office, a “part of a large-scale espionage campaign” by China. These revelations were supported by allies like the United States, who announced criminal charges against Chinese hackers and partners across Europe and the Indo-Pacific, condemning Beijing’s malicious cyber activity.
Newly discovered malware
One particularly sly tactic Chinese threat groups use is exploiting the trusted relationships and supply chains of the targeted organisations. Crowdstrike’s Global Threat Report assessed that Chinese threat actors known as “Jackpot Panda” and “Cascade Panda” “consistently exploited trusted relationships through supply chain compromises and actor-on-the-side or actor-in-the-middle attacks.” These groups can quickly gain clandestine access and deploy malware inside a victim’s network by hijacking software updates or compromising close third-party vendors.
For example, Jackpot Panda was found to have “trojanised” installers for legitimate Chinese software to deploy their malware. Similarly, Cascade Panda intercepted update traffic from commonly used software utilities to install its WinDealer remote access tool on systems belonging to Chinese-speaking targets. Even little-known groups potentially linked to Beijing pulled off supply chain attacks, such as compromising an Indian (among other) critical infrastructures with a cybersecurity vendor, I-Soon, distributing malware via its software updates across multiple sectors, affecting users across the globe.
Three ways your company could find itself in the firing line
While the Chinese government’s motivations may usually be centred on gathering intelligence (mainly for monitoring dissidents), UK companies could easily get caught in the crosshairs. Firstly, they represent a treasure trove of intellectual property, research, customer data, and other sensitive information crucial to Beijing’s strategic interests and economic leverage. The Chinese military policy of “civil-military fusion” blurs any remaining lines between the private sector and state assets.
Secondly, British firms are deeply embedded in the same supply chains, software ecosystems, and trusted vendor relationships, actively being exploited as vectors for initial access by Chinese hackers. After all, a company’s cybersecurity posture is only as strong as its weakest link in such an interconnected business environment. Threat actors have demonstrated a keen ability to methodically map out these interdependencies and pounce when the opportunity presents itself.
Finally, UK businesses like yours should be prepared for the potential collateral damage and interruptions caused by Chinese cyber operations, even when not directly targeted against them. The data thieves’ campaigns highlighted above directly interfered with the IT systems of government bodies responsible for administering elections and democratic processes in Britain. So, any company’s operations could halt if its technologies or data flow intersects with compromised systems.
How can you shield your business?
In the face of this daunting threat from a competent nation-state adversary, mid-size UK businesses must boost their cyber defences and resilience. A proactive, comprehensive cybersecurity strategy centred around advanced threat detection capabilities is essential. Implementing strong access controls such as multiple-factor authentication, tight identity management, encryption, and vetting the cybersecurity practices of third-party vendors can all reduce risk exposure.
However, even the most robust technical controls have limits against skilled, determined, and infinitely meticulous nation-state attackers like China’s hacker groups. Businesses require professional cybersecurity monitoring services, threat-hunting experts, and incident response capabilities to identify and neutralise intrusion attempts quickly. For this reason, continuous security awareness training to educate employees on the latest tactics, like supply chain compromises, is also critical.
Take protective steps now
As the UK government has demonstrated with its recent actions, exposing and holding malicious Chinese cyber criminals accountable is a priority for preserving our national security and democratic values. Businesses must follow suit and implement comprehensive defences against this looming threat. Unfortunately, failing to do so risks surrendering your organisation’s most valuable data, suffering crippling interruptions, or unwittingly aiding and abetting Beijing’s authoritarian projects. Now is the time to get ahead of those jeopardising UK companies – before a rocky cyber stance becomes a devastating crisis for your company.
Don’t hesitate to contact Thrive today to learn more about nation-state threat detection and mitigation strategies tailored to mid-market UK businesses. Protecting your organisation from state-backed cyber campaigns demands the vigilance and expertise that our experienced team can provide you with every step of the way.
