As organizations become more reliant on technology to drive innovation and maintain a competitive edge, the roles of a Chief Information Security Officer (CISO) and a Chief Information Officer (CIO) have evolved significantly. No longer confined to isolated silos, these positions now require a broader, more collaborative approach to leadership, aligning technology, security, and business objectives.
Historically, CIOs managed IT systems and ensured uptime, while CISOs safeguarded those systems from cyber threats. Today, their responsibilities overlap as digital transformation blurs the boundaries between IT infrastructure and cybersecurity.
CIO Evolution: From Operations to Innovation
Being a CIO has expanded from ensuring the operational stability of their business’s IT systems to spearheading digital innovation. Today, CIOs are expected to:
- Drive Business Strategy: Align IT projects with overarching business goals, enabling growth and efficiency.
- Champion Cloud and AI Adoption: Implement cutting-edge technologies to create scalable, secure, and efficient IT ecosystems.
- Enhance Collaboration: Partner with other executives, including the CISO, to ensure that technology investments support both operational needs and security imperatives.
CISO Evolution: From Gatekeeper to Risk Manager
Similar to the CIO, CISOs are now seen as strategic advisors focusing on risk management. Their expanded scope includes:
- Building Cyber Resilience: Establishing a proactive security posture that incorporates incident response and recovery plans.
- Enabling Business Agility: Providing security solutions that support rather than hinder innovation and speed.
- Regulatory Expertise: Ensuring their organization stays in compliance with an increasing number of complex data protection and privacy laws.
Key Trends Shaping the CISO and CIO Roles
- Increased Collaboration
CISOs and CIOs must work closely to bridge the gap between innovation and security, ensuring initiatives like cloud migrations and connected device deployments don’t expose organizations to undue risk. - Data-Driven Decision Making
Leveraging analytics and real-time monitoring tools, CIOs and CISOs are expected to use data to guide their strategies. From predicting IT system performance to identifying potential vulnerabilities, actionable insights are key. - Emphasis on Cyber Insurance
CISOs are increasingly involved in discussions about cyber insurance. They work with CIOs to ensure the organization meets the stringent security requirements needed for favorable coverage terms.
The Future of the CIO and CISO Partnership
The most successful organizations will be those where the CIO and CISO form a dynamic duo, balancing innovation with security. Together, they must anticipate future challenges, such as:
- Quantum Computing: Preparing for a world where traditional encryption methods become obsolete.
- Global Threat Landscapes: Navigating geopolitical cyber threats and ensuring supply chain security.
- Sustainability in IT: Adopting eco-friendly technologies without compromising security or performance.
The roles of the CISO and CIO are no longer confined to separate domains. As the digital landscape grows more interconnected, their collaboration is critical to building resilient, innovative, and secure organizations. By aligning their strategies, these leaders can ensure technology serves as a powerful enabler, not a vulnerability. Contact Thrive today to learn more about the future of digital transformation.
Combining Cybersecurity and IT Disaster Recovery Solutions to Safeguard Canadian OrganizationsCanadian businesses and organizations need cybersecurity solutions in place along with robust backup and disaster recovery capabilities to ensure they’re resilient and protected against all threats and disruptions to their critical and everyday operations.
In today’s digital-first landscape, a growing number of Canadians rely on technology to drive their operations. However, with greater tech reliance comes heightened vulnerability to cyber threats. Organizations need to implement multi-layered cyber resiliency and disaster recovery solutions for effective prevention, detection, incident response, and recovery from downtime.
Under-estimating the requirements, likelihood, and consequences from cybersecurity attacks, data breaches, and malicious insider threats can result in potentially business-ending events.
Building a robust Business Continuity Plan (BCP) with IT disaster recovery strategies that are tailored to meet modern cybersecurity demands requires a blend of strategic foresight, advanced technology, and flexibility.
Understanding the Current Cyber Threat Landscape
Cyber threats continue to evolve at an alarming rate. Ransomware, phishing attacks, data breaches, and Distributed Denial of Service (DDoS) incidents are increasing daily, often targeting critical infrastructure. Specifically, Canadian businesses spent $1.2 billion recovering from cybersecurity incidents last year, double what was paid a couple of years earlier. Canadian organizations, particularly small to mid-sized businesses (SMBs), face challenges maintaining strong defenses due to limited resources and a lack of cybersecurity expertise. For example, RCMP’s cybercrime investigative teams experienced ongoing challenges in recruiting and retaining staff with the needed technical skills, resulting in a 30% position vacancy since January 2024, affecting their capacity to address cybercrime.
According to the Canadian Anti-Fraud Centre, there have been over 21,604 reports of fraud in Canada with over $284 million stolen since the start of 2024. The risk of downtime, data and monetary loss, and reputational damage makes having a robust business continuity plan essential.
The Role of Business Continuity Planning in Cyber Resilience
Business Continuity Planning involves creating systems of prevention and recovery to deal with potential threats to a company’s operations. For Canadian businesses, a well-crafted BCP ensures critical business functions continue operating during and after a disaster—whether it’s a natural event, cyberattack, IT system failure, or sudden disruption to your workforce or critical third-parties. Effective BCPs must now include comprehensive strategies for maintaining cybersecurity, data integrity, and IT infrastructure resilience.
Cyber resilience is a key component of BCPs because business disruptions are more likely to come from cyber incidents than physical ones, like a natural disaster. However, traditional approaches to BCP, which focused solely on backup systems and disaster recovery, are no longer sufficient. Organizations must focus on agile solutions that incorporate robust cybersecurity measures into their continuity planning.
Offering More Choices for Greater Cyber Resilience
The backbone of a strong IT continuity plan lies in offering businesses choices—choices that ensure they can tailor their strategies based on specific operational needs and risk profiles. Canadian businesses are looking for flexibility in the following key areas:
Cloud-Based vs. On-Premise Solutions: Different managed Cloud solutions provide Canadian businesses with greater resilience by diversifying their IT infrastructure. Cloud-based backups, for instance, ensure that businesses can recover critical data even if local systems are compromised during a cyberattack. Offering options to choose between Cloud-only, or on-premise allows businesses to implement a tailored approach that best suits their needs and budget.
Managed Services for Cybersecurity: Managed Security Service Providers (MSSPs) offer businesses the ability to offload critical cybersecurity functions to experts. By partnering with an MSSP, businesses gain access to advanced threat detection, incident response, and compliance management. MSSPs also ensure that companies stay current with the latest security patches and updates, further strengthening BCP. Advanced MSSPs like Thrive, which provide next-generation cybersecurity solutions, are key to ensuring cyber resilience. Thrive’s integrated approach to cybersecurity management helps organizations defend against advanced threats, mitigate risks, and recover from attacks quickly.
Autonomous Penetration Testing: Autonomous penetration testing is a cutting-edge service that Canadian businesses can leverage to strengthen their cyber resilience. By continuously identifying and addressing vulnerabilities in IT systems, businesses can ensure that their BCP remains aligned with current cyber risks. This proactive approach helps organizations to stay ahead of potential attacks, giving them more control over their cybersecurity posture.
Managed Detection and Response: MDR services are a human-led approach to cybersecurity aimed at detecting and mitigating threats to networks, cloud infrastructure, servers, and SaaS applications in real time. Thrive combines cutting-edge technology with the expertise of skilled cybersecurity professionals to provide frontline protection from costly cyber threats such as ransomware, phishing, and crypto-jacking.
Endpoint Detection and Response: Specifically designed as a proactive security solution for workstations and servers, EDR reduces security risk by detecting malicious activity, preventing malware infection, and disabling potential threats. EDR can be difficult to implement and utilize to its full potential without experienced IT support resources who can quickly respond to threats to endpoints when they happen.
Scalable Disaster Recovery Solutions: Not all businesses require the same level of disaster recovery preparedness. Small businesses may need basic backup and recovery solutions, while larger enterprises might require more robust systems that ensure minimal downtime. Scalable managed disaster recovery services allow companies to pay only for the resources they need, with the flexibility to scale as their business grows.
Scalability also extends to cybersecurity solutions such as real-time network monitoring, automated vulnerability scanning, and penetration testing, which can be adapted as companies’ needs evolve.
Strengthening Business Continuity Through Collaboration
Canadian businesses are also realizing the importance of collaboration when it comes to continuity planning. Cyber resilience is not achieved in isolation; it requires coordination across teams, departments, and external partners. For example, partnering with third-party cybersecurity firms and MSSPs, like Thrive, ensures that companies have access to the latest security tools and expertise. Thrive has deep experience in applying NIST and CIS frameworks and best practices for businesses and organizations of all sizes and industries.
Moreover, the collaborative efforts between the private sector and the Canadian government, through initiatives such as the CyberSecure Canada certification, help SMBs implement recognized cybersecurity standards. This certification helps businesses strengthen their cybersecurity posture while providing assurance to their customers and partners.
By adopting flexible, scalable, and collaborative approaches, businesses can not only survive a cyber incident but also thrive in an increasingly complex threat landscape. With the right mix of tools and strategies, Canadian businesses can ensure that their IT infrastructure remains robust, responsive, and ready for whatever challenges lie ahead. Contact Thrive today to learn more about how our Canada-based managed services can help your organization stay resilient against ongoing cyber threats.
Enhance Business Productivity and Ensure Peace of Mind with Gartner’s Hype Cycle for Security OperationsGartner’s Hype Cycle for Security Operations provides a strategic view of how various security technologies and practices evolve, mature, and are adopted by businesses. Leveraging this framework allows organizations to understand which tools and approaches are on the rise, at their peak, or mature enough to offer them a significant ROI.
Understanding the Hype Cycle Stages for Better Decision-Making
The Hype Cycle is comprised of five stages:
- Innovation Trigger
- Peak of Inflated Expectations
- Trough of Disillusionment
- Slope of Enlightenment
- Plateau of Productivity
By understanding these stages, organizations can time their adoption of security technologies to maximize productivity and prevent wasted resources.
Enhance Productivity Through Informed Security Investments
With the Hype Cycle as a guide, organizations can identify which emerging security technologies are worth pursuing early and which may yield better results once they mature.
Early Adoption for High-Impact Solutions: Tools that reach the Slope of Enlightenment are often at a maturity level where organizations can realize their benefits without the risks associated with early adoption. For example, if Managed Detection and Response (MDR) services are at this stage, companies can adopt them to improve incident detection and response capabilities, enhancing productivity by reducing downtime and improving security outcomes.
Avoid the Trough of Disillusionment: Security tools or trends that are in the Trough of Disillusionment can indicate a high potential for over-promising and under-delivering. Gartner’s framework helps organizations avoid these pitfalls by showing which tools may not be living up to the initial hype. Security leaders need to decide whether these tools will ever mature to a point where they contribute directly to productivity.
Foster Peace of Mind with a Clear Security Roadmap
With security threats constantly evolving, peace of mind for organizations hinges on proactive, forward-looking security strategies.
Strategic Adoption for Enhanced Security Posture: The Hype Cycle clarifies where certain technologies stand in terms of reliability and effectiveness. For instance, solutions such as Endpoint Detection and Response (EDR) reach the Plateau of Productivity after several iterations, offering proactive, real-time security with orchestrated incident response. When adopted, these mature tools provide peace of mind as they have been validated by other users and experts alike.
Reduce Risk Through Timely Adoption: Following Gartner’s roadmap helps organizations prevent adopting tools that may increase risk or strain their limited IT resources. By prioritizing mature, effective technologies, companies avoid common missteps associated with adopting unproven tools, thereby maintaining robust protection without disrupting operations.
Use the Hype Cycle as Part of a Security Strategy
For organizations, the Hype Cycle offers a strategic map that aligns well with productivity and risk management goals.
Continual Adaptation to New Threats: As new threats emerge, the Hype Cycle can help identify promising innovations and determine if their adoption is practical based on current resources and risk. Security leaders can continuously adapt their strategy without overwhelming their teams or overextending budgets.
Build a Security Roadmap Based on Realistic Expectations: Organizations can use the Hype Cycle to plan for gradual adoption of new technologies, allowing them to prioritize solutions that align with both their immediate needs and long-term security objectives. This staged approach leads to more manageable, sustainable security transformations and fosters confidence at all organizational levels.
The Gartner Hype Cycle for Security Operations is more than a list of tech trends; it’s a critical tool that helps organizations build a forward-thinking security strategy. By using this framework to guide their investments, organizations can enhance productivity, align technology with risk tolerance, and ensure peace of mind. With a clear path toward strategic adoption, organizations can not only stay secure but also support a streamlined, productive IT environment.
Contact Thrive to learn more about implementing a robust security strategy to help your organization reach its business goals. The Thrive team is comprised of industry and technical subject matter experts dedicated to ensuring that customers optimize their business performance through the strategic implementation of their IT infrastructure.
Reduce Your Cyber Risk: How Autonomous Penetration Testing Can HelpToday, businesses face an increasing volume and sophistication of cyber attacks. To protect sensitive data and systems, organizations often rely on penetration testing to identify system weaknesses and vulnerabilities before bad actors exploit them. However, many organizations still conduct manual penetration tests, a method that, while effective, presents several challenges.
The State of Manual Penetration Testing
Traditional pen testing involves cybersecurity professionals simulating an attack to identify weak points in an organization’s network. These tests, often conducted quarterly or annually as part of an overarching vulnerability management plan, provide a snapshot of a company’s system weaknesses and identify vulnerabilities at a specific moment. However, as cyber threats evolve rapidly and become more sophisticated, these infrequent tests can leave businesses exposed between test cycles. Additionally, manual pen testing requires significant company resources, both in terms of time and expertise.
Challenges with Manual Penetration Testing:
- Infrequent Testing: Cyber threats are constantly evolving, and manual tests are often conducted too infrequently to keep up. This leaves gaps where newly discovered weak points and vulnerabilities could go undetected until the next scheduled test.
- Time-Consuming: A traditional pentest can take days or even weeks to complete, depending on the size and complexity of the system. This delay can slow down the remediation process, leaving businesses vulnerable for longer.
- Resource Intensive: Skilled cybersecurity experts are essential for effective manual penetration testing, and the process often diverts internal resources. These professionals must be well-versed in the latest attack vectors and testing methodologies, which can make the tests costly and difficult to scale.
- Human Error: Despite their expertise, penetration testers are still human and can make mistakes or overlook system weaknesses, especially when dealing with large, complex systems and the myriad of security tools companies already utilize
Thrive’s Autonomous Penetration Testing: A Smarter Solution
Thrive’s autonomous penetration testing service offers a modern, scalable alternative to traditional manual tests. Using advanced algorithms and automation, Thrive’s black box solution continuously simulates attacks on your network, identifying weaknesses and vulnerabilities in real-time, while ensuring that no gaps go unchecked between testing cycles.
How Autonomous Penetration Testing Works:
Autonomous penetration testing (pen testing) is designed to provide organizations an affordable, unbiased, and thorough view of their system. Highlights include:
Regular Testing: Unlike manual tests that happen periodically, autonomous penetration testing operations can be run more frequently, providing up-to-date insights into your security posture. As new weaknesses emerge or your system changes, they’re identified immediately, allowing for a proactive approach to risk management.
- Faster Results: Automation significantly reduces the time it takes to conduct a penetration test. What could take a manual tester days or weeks to uncover, Thrive’s pen testing can detect in hours. This speed translates into faster remediation, minimizing the window of opportunity for attackers.
- Cost-Effective: By leveraging automation, Thrive’s service is more scalable and cost-effective than manual penetration testing. Organizations can run more frequent tests without needing to allocate additional internal resources or hire expensive external experts.
- Reduced Human Error: Thrive’s pen testing eliminates the risk of human error. With sophisticated machine learning algorithms and a comprehensive approach to testing, every potential vulnerability is thoroughly examined and flagged for remediation.
Actionable Remediation Insights
The true value of penetration testing isn’t just in identifying system weaknesses but also in providing a clear path to remediation. Thrive’s autonomous penetration testing service delivers detailed remediation guidance that outlines the vulnerabilities found, along with actionable recommendations to address each issue.
The test results dashboard gives you a digestible way to review prioritized vulnerabilities based on the level of risk they pose to your business, ensuring that the most critical issues are addressed first. It also shows the attack path in which a real-world cyber criminal can take to get into your system, giving you a high-level view of how seemingly small weak points can lead to catastrophic breaches. With clear guidance, businesses can take the necessary steps to patch vulnerabilities and weak points of entry, improve security configurations, and reduce their overall risk.
Boost Your Security Posture with Thrive
The cyber threat landscape is constantly changing, and businesses need a solution that evolves just as quickly. Thrive’s autonomous penetration testing service offers a proactive, cost-effective way to uncover weaknesses in your system and provide clear, actionable steps to mitigate risk. By adopting this automated approach, businesses can strengthen their security posture, stay ahead of emerging threats, and ultimately reduce the likelihood of a successful cyberattack. Download our definitive guide to autonomous penetration testing today!
Don’t wait for the next manual penetration test to uncover hidden vulnerabilities. Contact Thrive today to learn more about how our autonomous penetration testing service can help your business stay secure and stay ahead of threats.
Don’t Be at Risk: Migrate from Legacy On-Prem Servers to the CloudAs digital transformation sweeps across industries, organizations that still rely on legacy on-premise servers face growing risks, including increased operational costs, and cybersecurity vulnerabilities. While cloud computing has evolved into a secure and scalable alternative, the potential business performance and business risk gaps between legacy on-prem systems and the cloud can no longer be ignored.
The Hidden Risks of Legacy On-Prem Servers
Security Vulnerabilities
Legacy on-prem servers are vulnerable to a range of threats including outdated software, end-of-life operating systems, and unpatched vulnerabilities. Many businesses struggle to keep up with security patches and updates, leaving their sensitive data exposed for cyber criminals. Hackers often target these security weaknesses, leading to data breaches, ransomware attacks, or complete system failures.
In contrast, cloud providers, like Thrive, implement advanced security mechanisms such as continuous patch management, AI-driven threat detection, and encryption at rest and in transit. Cloud environments are also maintained by teams of security experts who ensure compliance with stringent industry regulations such as DORA, SOC 2, ISO 27001, and GDPR.
High Operational Costs
On-premises infrastructure can be very costly to maintain. The upfront investment is significant, and the ongoing maintenance costs quickly add up too. Organizations also have to allocate resources to IT staff for routine tasks such as updates, troubleshooting, and backups. Plus, mainframe expertise is harder and more expensive to come by because skilled workers are reaching retirement age with no replacements on deck.
Cloud solutions, however, offer better scalability, and there’s no need to invest in hardware or worry about lifecycle management. With cloud-based infrastructure, businesses can focus on innovation and reaching their business goals rather than maintenance.
The Benefits of Migrating to the Cloud
- Enhanced Security Measures: One of the biggest advantages of cloud migration is an improved security posture. Cloud providers continually invest in cutting-edge cybersecurity technologies, offering real-time monitoring, automatic updates, and advanced encryption standards for customers. Most cloud platforms also feature dedicated security tools like firewalls, intrusion detection systems (IDS), and security information and event management (SIEM). Migrating to the cloud also significantly reduces the risk of breaches, due to regular patching and updates.
- Long-Term Cost Savings: The shift to the cloud can lead to substantial cost savings for businesses. Moving away from legacy hardware eliminates the need for expensive hardware upgrades, space for servers, energy, and cooling costs associated with maintaining an on-prem server room. Using the cloud reduces maintenance, fewer IT staff for routine updates, and less frequent downtime, leading to lower operational costs.
- Increased Agility: Modern businesses require agility to adapt to fast-changing market conditions. Utilizing the cloud provides businesses with the ability to quickly deploy new services, scale infrastructure quickly, and respond rapidly to ever-changing customer demands.
Migrating Your Legacy Servers to the Cloud
Moving from a legacy infrastructure to the cloud requires a well-planned approach to ensure minimal disruption and maximize long-term benefits. Below are some key steps to help your business migrate to the cloud successfully:
- Assess Your IT Infrastructure: Before starting your cloud migration, assess your current IT stack to understand what applications, services, and data need to be moved. Evaluate which workloads are cloud-ready, which may need modification, and if any should remain on-prem for specific reasons (such as compliance).
- Choose the Right Cloud Model For Your Business: Determine which cloud deployment model fits your business’s needs: public, private, hybrid, or multi-cloud. Public cloud solutions like Microsoft Azure are cost-effective and highly scalable. Private cloud options offer greater control over data and may be more suitable for regulated industries. No matter your choice, Thrive’s team of expert Cloud engineers can help design, build, and support the Cloud solution that best meets your business needs.
- Plan for Migrating Your Data: Data migration can be one of the most challenging aspects of the move to cloud. Businesses must ensure that their data is securely transferred to the cloud without any loss or corruption.
- Implement Strong Security Controls: Security should be a priority during and after cloud migration. Leveraging cloud-native security features such as identity and access management (IAM), data encryption, and multi-factor authentication (MFA) can ensure your data stays safe. Continuous monitoring and regular audits should also be a part of your post-migration plan to maintain a strong security posture.
How Thrive Can Help
Migrating to the cloud can dramatically improve security, reduce costs, and unlock new opportunities for growth and innovation. With Thrive, you have access to a secure hybrid cloud solution that can help keep your data secure, scale with your business, and help you meet your business goals. Don’t wait until it’s too late— contact Thrive today and embrace the cloud and mitigate the risks of outdated infrastructure.
How to Optimize Your Microsoft 365 Storage and Save with ThriveIf your organization is using Microsoft 365 for digital collaboration, you may face challenges with managing your SharePoint storage and its associated costs. As your organization grows and generates more content, you may find yourself running out of storage space or paying more for overage fees. You may also have a lot of redundant, obsolete, or trivial (ROT) data that is cluttering your SharePoint sites, making it harder to find what you need.
These issues have many small and mid-market companies like yours wondering how to optimize your SharePoint storage and save costs while ensuring compliance and governance. At Thrive, we have the team and the tools to solve your Microsoft 365 storage challenges.
47% of digital workers struggle to find information or data needed to effectively perform their jobs – Gartner
What Is Thrive’s Microsoft 365 Platform Services Team?
Thrive’s Microsoft 365 Platform Services team consists of experts specializing in Microsoft 365 solutions, with specialists in strategy and governance, end-user training, development services, and support. They are dedicated to helping clients regain control of their data, from assessments to remediation and managed services.
Our Approach to Control Storage Costs
Our team of experts will work with you to optimize your storage and your budget. Here’s how:
- Microsoft 365 Storage Optimization Assessment: We will conduct an assessment of your SharePoint storage using our Storage Optimization System and provide you with a detailed report on your ROT and inactive data and the potential cost savings you can achieve by optimizing your storage.
- ROT & Inactive Data Reduction: We will help you configure and execute storage optimization policies and provide you with a summary of the changes and the impact on your SharePoint storage.
- SharePoint Retention Consultation: We will help you design and deploy retention policies for your SharePoint data and provide you with a summary of the compliance and governance outcomes.
- Storage Optimization Policies: We will help you implement tailored retention policies to declutter your Microsoft 365 workspaces and establish a clean baseline, including monthly reports and consultations on your storage optimization progress and best practices.
Thrive will work with you to understand your business goals and needs and tailor our services to fit your specific requirements and budget. We will also provide you with ongoing support and guidance to ensure that you get the most out of the Storage Optimization System.
With our storage optimization services, you can benefit from the following outcomes:
- Reduce your SharePoint storage costs by up to 50% by archiving or deleting ROT and inactive data to cheaper storage or the recycle bin.
- Improve your SharePoint performance and user experience by decluttering your sites and making it easier to find relevant and updated information.
- Enhance your compliance and governance by applying retention policies to your SharePoint data and ensuring that it is disposed of according to your legal and regulatory obligations.
- Align your information management strategy with your business goals and needs by using our Storage Optimization System and recommendations to make informed decisions about your SharePoint storage optimization.
Ensuring Compliance and Governance
By helping clients apply accurate classification and disposal policies to their content, Thrive ensures that SharePoint data is managed in accordance with legal and regulatory requirements, facilitating compliance for your organization.
Get Started With Thrive
If you are interested in taming your Microsoft 365 storage costs and enabling robust information management, contact us today to schedule a free consultation. We will discuss your current storage situation, challenges, and goals, and how we can help you through our services.
Know Your Business Risk: A Definitive Guide to Autonomous Penetration TestingThe Importance of Conducting Penetration Testing in Today’s Cybersecurity Landscape
As cyber adversaries become more advanced, the need for proactive and continuous security measures is crucial for organizations. Autonomous penetration testing has emerged as a cutting-edge solution to this pressing challenge, providing businesses with a robust and efficient means to identify vulnerabilities and system weaknesses before they can be exploited.
Download our definitive guide to autonomous penetration testing that dives into the importance of why businesses need to adopt autonomous penetration testing as part of their cybersecurity plan, implementing a penetration testing plan for your business, what to do with your testing results, and more.

Extend Endpoint Protection and Get to Know DNS Filtering for Your Business
As organizations continue to embrace remote work and the use of mobile devices as work aids, securing these endpoints requires robust solutions like DNS filtering, which protects users regardless of their location.
Download our DNS: The New Perimeter Guide to better understand the different types of DNS filtering, how it can help protect your business, and make your workplace a more productive environment.

Being vigilant about your cybersecurity posture is more important than ever. With the increased ease of cyber attacks, such as phishing schemes, ransomware, and data breaches, businesses need to protect their digital assets and have a plan in place should a breach occur. The rise in cyber attacks has led businesses to tap into their cyber insurance policies or seek out coverage for the first time. But the increase in potential payouts has led to stricter cyber insurance requirements for companies to meet. Lack of compliance could lead to being denied a policy, or being denied benefits when already insured.
What is Cyber Insurance?
Cyber insurance, also known as cyber liability insurance, is a specialty insurance that aims to cover the financial losses that organizations have as a result of ransomware attacks, data breaches, and other cyber incidents. Having cyber insurance can lessen the financial impact of a breach, which costs organizations an average of US$4.35 million per breach, according to IBM’s Cost of a Data Breach report. Due to the rise in payouts from security breaches, insurers have increased their cybersecurity requirements for companies before they can get coverage. Having cyber insurance can protect organizations with the following coverage:
- Financial loss due to business disruption
- Incident response, system repairs, forensic investigations and other services after an attack
- Legal expenses
- Cost of notifying customers of hacks where personally identifiable information (PII) has been compromised
- Ransom payments
- Public Relations to deal with reputational management post-breach
How Businesses Can Meet Cyber Insurance Requirements
There are many ways in which companies can improve their cybersecurity posture and meet more rigorous insurance requirements at the same time. Having a solid IT framework can help prevent attacks before they happen, and also make your organization a low risk insurance candidate.
For companies trying to match up to potential cyber insurance requirements, Thrive recommends following the CIS 18 Critical Security Controls which provides a roadmap for establishing basic cyber hygiene and then the steps to mature your approach. Of course, you will also want to understand the specific needs of your insurer and ensure you’re meeting those, but the CIS controls are a great starting point for insurance as well as complying with other regulations and standards as part of a cybersecurity compliance program.
To first understand your cybersecurity posture, conducting a cybersecurity risk assessment can help you understand potential gaps and weaknesses. A comprehensive risk assessment can also help prioritize areas that need immediate attention and align your security measures with the specific risks your business faces.
Other ways to improve your cybersecurity posture include:
- Patch Management and Vulnerability Remediation
- Advanced Threat Detection and Response
- Data Encryption and Secure Communication
- Employee Training and Awareness
- Compliance with Industry Standards
- Regular Data Backups
How Thrive Can Help
Working with a managed service provider, like Thrive, provides organizations with the specialized knowledge and tools needed to enhance their cybersecurity program and meet insurance requirements.
Thrive provides comprehensive, 24x7x365 services to help get your organization’s cybersecurity stack prepared for any attacks or breaches that may try to compromise your systems. Thrive offers Managed Detection and Response (MDR) services that aim to proactively detect and mitigate threats in real time. Additionally, Thrive provides patching and vulnerability management services to ensure that your systems are up-to-date and best protected.
Strengthening your cybersecurity program is a multifaceted process that requires a combination of technical controls, employee training, and compliance with industry standards. By implementing these best practices, businesses can not only reduce their risk of cyber incidents but also meet the increasingly stringent requirements set by cyber insurance providers. In today’s threat landscape, a proactive approach to cybersecurity is essential for safeguarding your business and ensuring that you are fully covered in the event of an incident.
Contact Thrive today to learn more about how an MSP can help you boost your security posture and get you cyber insurance ready.
How Managed Services Can Help Your Security OperationsMidsize enterprises (MSEs) face a unique set of challenges in maintaining a robust cybersecurity posture. One of the most pressing issues is the lack of cybersecurity full-time equivalents (FTE). This shortage can leave MSEs vulnerable to cyber threats, as they often lack the resources to hire and retain a full-fledged internal cybersecurity team. The ideal team consists of members across three different role types:
- CIO/CISO
- Infrastructure and Operations
- MSSP/MDR/EDR
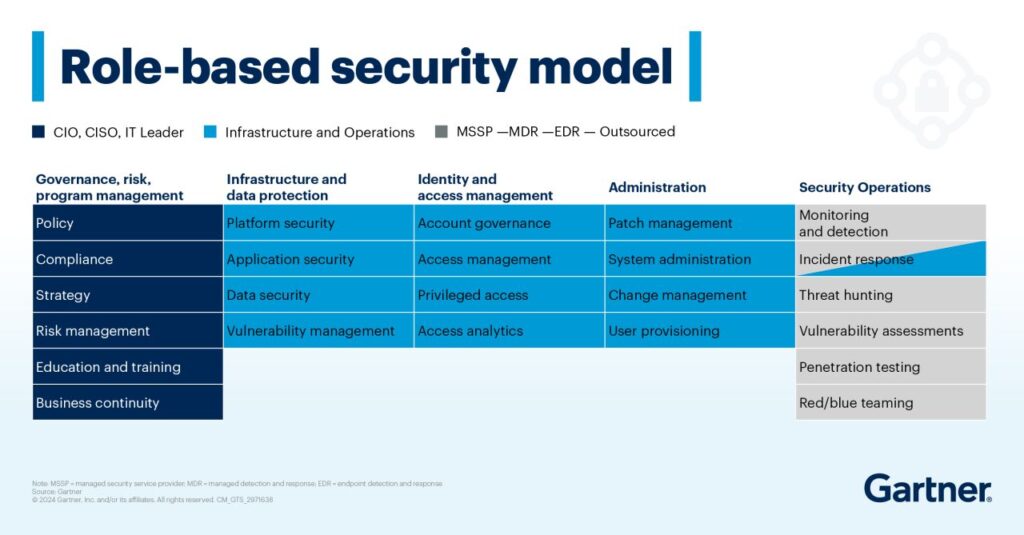
According to the Gartner report, How Midsize Enterprise CIOs Create an Effective Cybersecurity Operations Strategy, Managed Service Providers (MSPs) offer a strategic solution to this problem by providing outsourced IT professionals with specialized expertise, ensuring that MSEs can protect their IT infrastructure effectively.
The Cybersecurity Challenge for MSEs
MSEs often operate with constrained budgets and limited staff, making it difficult to allocate sufficient resources to cybersecurity. The demand for skilled cybersecurity professionals far exceeds the supply, driving up salaries and making it even harder for MSEs to compete with larger organizations for top talent.
47% of MSE CIOs and the most senior IT leaders use external managed services to handle skills gaps in both cyber and information security -2023 Gartner MSE Baseline survey
A small internal IT team without satisfactory support and resources can lead organizations to have many business-halting cybersecurity issues, such as:
- Lack of security measures across the organization, such as access controls, threat detection, and multi-factor authentication (MFA) setups
- Increased vulnerabilities due to lack of scheduled assessments regular updates, like OS and 3rd-party application patching
- Risk of not meeting regulatory requirements, which are constantly changing and require an agile approach to cybersecurity
How Managed Service Providers Bridge the Gap
Managed Service Providers (MSPs) and Managed Detection & Response (MDR) can offer a more comprehensive solution to these security challenges by providing outsourced IT professionals who bring specialized cybersecurity expertise to the table, across all industries. According to Gartner, by 2026, 70% of midsize enterprises’ security portfolios will be outsourced, up from the 40% of outsourced security portfolios today. Here’s how MSPs can help MSEs maintain a robust IT stack:
- Access to Expertise: MSPs allow access to cybersecurity experts who stay up-to-date with the latest threats and security technologies. Partnering with an MSP allows MSEs to tap into a wealth of knowledge without the overhead costs associated with hiring full-time staff.
- 24x7x365 Monitoring and Support: MSPs offer round-the-clock monitoring and support, ensuring that any suspicious activity is detected and addressed promptly, so that businesses can operate as usual. 24x7x365 vigilance is critical in mitigating the impact of potential breaches.
- Scalable Solutions: As MSEs grow their businesses, their cybersecurity needs may evolve. MSPs provide scalable solutions that can be tailored to meet changing requirements and can adapt to the needs of their clients.
- Regulatory Compliance: MSPs have extensive experience in helping businesses comply with industry regulations. They can assist in implementing the necessary controls and documentation required to meet compliance standards, reducing the risk of costly penalties and reputational damage.
- Cost-Effective: Hiring a full-time cybersecurity team can be expensive for MSEs. MSPs offer a cost-effective alternative by providing access to top-tier cybersecurity talent on a subscription basis. This allows MSEs to benefit from expert services without the financial burden of maintaining an in-house team.
How Thrive Can Help
Hiring an MSP, like Thrive, can be the answer for many MSEs looking to build out their IT infrastructure, without having to hire FTEs. Unlike security vendors that only focus on MDR, Thrive can provide companies with IT outsourcing that taps into experts in all three roles: CIO/CISO; Infrastructure and Operations; and MSSP/MDR/EDR. With Thrive, MSEs have access to first-in-class solutions that will allow them to feel confident in their security framework so they can focus on meeting their business goals. With Thrive, organizations have access to:
- vCISO: Thrive’s virtual CISO offering aims to design, develop, and maintain a customized Information Security Program that complements your business’s overall strategy and risk tolerance
- Infrastructure and Operations: Thrive works with you to tailor a cybersecurity and cloud infrastructure plan to help meet your business goals. Thrive’s team of experts work round the clock to help bolster your IT operations with solutions, such as vulnerability management.
- Managed Detection and Response (MDR): Thrive’s MDR solution continuously monitors your network, endpoints, and other critical assets for signs of suspicious activity or security breaches
- Endpoint Detection and Response (EDR): Thrive’s 24x7x365 support from our Security Operations Center (SOC), ensures that after the EDR solution identifies gaps in your IT stack, our experts move in to remedy the issues, ensuring business continuity
Contact Thrive today to learn more about how our managed IT services can help your organization better round out your IT stack.
