RPO Basics
A Recovery Point Objective (RPO) is a metric used to determine how often data backups should run, and to evaluate what services and solutions match your business needs. The RPO is determined by understanding how much data loss your business can tolerate.
Some businesses and organizations may have mandated RPOs due to data privacy and compliance requirements, such as the financial and legal industries.
Why is this important? Data is dynamic and constantly changing over time, while backups only capture data at a specific point in time. The length of time between each scheduled backup is known as the backup interval. The wider the interval, the higher the likelihood that your data will change during that time, and the more risk you take as that data remains without a backup until the next backup. In the event of a data disaster, a higher backup frequency enables more recovery points to restore from and shrinks the interval between backups so that data has a better chance of being captured. Your RPO defines the maximum allowable amount of lost data measured in time from a failure occurrence to the last valid backup.
Meeting Your RPO
For example, an e-commerce business may conduct around-the-clock online transactions. They evaluate their systems and business model and determine that losing more than 15 minutes worth of data would be extremely detrimental to their operations, customer service, revenue, and reputation. They decide that their RPO and backup interval should never exceed 15 minutes. They then choose a solution that is capable of running a backup schedule at 15 minute intervals, such as at every quarter hour on the hour (0:00, 0:15, 0:30, and 0:45).
If a failure occurs, with successful backups every 15 minutes, they would always be able to recover without major threat to their business continuity. Here are two examples on how it would play out:
- If they experienced a system failure at 0:03, they’d only lose 3 minutes worth of data.
- If failure occurred at 0:52, they’d lose 7 minutes of data.
- For both scenarios, since the time between the last backup before failure and the data disruption are well below the 15 minute RPO (3 and 7 minutes respectively), both losses are survivable for the business.
Failing to Meet Your RPO
Conversely, if a business can only withstand an hour’s worth of data loss, yet has backups running every two hours, that business is not meeting their RPO and is at risk of losing critical data. The risk escalates the further in time the failure occurs from the last backup.
For example, if they run their backups every odd hour on the hour (1:00; 3:00; 5:00, et cetera):
- A failure at 1:40 is less damaging than one that occurs at 4:55.
- The first incurs 40 minutes of data loss, which is acceptable according to their RPO of 1 hour.
- The second incident incurs 1 hour 55 minutes of data loss, which definitely does not meet their RPO and may seriously damage their business.
For this business, without the appropriate 1 hour backup interval, meeting their RPO of 1 hour is a game of chance and does not meet their business needs. If a data disaster occurs such as a ransomware attack, user error, or natural disaster, they stand to suffer damage and potentially opening themselves up to liability, loss of business, and compliance risk.
RPO Services and Solutions
There are a range of services and solutions that enable backup intervals that support different RPOs. The chosen RPO can affect the price, configuration, and IT resources required. Working with a flexible, customer-centric backup and disaster recovery service provider can help you to determine the most cost-effective and responsive solution for your business.
Backup as a Service (BaaS)
Backup as a Service (BaaS) offers fully configurable online backup and recovery processes, supported by Thrive. These services are scaled for your organization so that you get the control you need with the support that you want.
Backups can be performed automatically according to flexible backup schedules, allowing for businesses of all sizes and needs to meet their specific RPOs. Communication is initiated by your systems, and your information is encrypted using AES (Advanced Encryption Standard), before being pushed via a secure SSL/TLS connection to Thrive’s datacenters. All of the backups are also incremental and only move new or changed data.
Thrive proactively monitors the data centers, operations, and customer data transfers to ensure optimal backup and recovery.
Disaster Recovery as a Service (DRaaS)
Disaster Recovery as a Service (DRaaS) enables your company to replicate data and deploy a Disaster Recovery (DR) environment without needing to construct a second physical data center. DRaaS replication ensures that your production site and DR site are in sync, allowing you to meet demanding Recovery Point Objectives (RPOs).
What About Restoring Backups?
BaaS allows both local and cloud restores from your backups based on your RPOs and the stored backup snapshots. DRaaS extends recovery capabilities to allow for full recovery directly into cloud infrastructure in just minutes, giving your organization the Recovery Time Objective (RTO) that you need for true business continuity.
Thrive to the Rescue
Your Backup and Disaster Recovery Experts
Thrive is a trusted global provider of comprehensive cloud, data protection and security services.
Since 2001, Thrive has provided these robust and secure managed cloud and disaster recovery solutions from a scalable multi-tenant infrastructure, supported by our first-class in-house technical team. Thrive delivers highly flexible and responsive solutions with outstanding value and service, using state-of-the-art technology to offer ultimate protection and peace of mind.
We are driven to be your trusted partner and to ensure that we deliver a Thrive Experience that meets your business requirements with the reliability, scalability, and support that your business demands.
Contact us today to learn more about how Thrive can help you meet your operational demands while protecting and recovering your most valuable asset – your data.
Let’s be honest, nearly all of us have been victims of a friendly April Fool’s prank at some point. The day (and month!) is full of (mostly) harmless pranks and jokes by friends and family. But let’s not forget that getting targeted by hackers and cybercriminals is also very much a reality. Pranksters love to play jokes on businesses and unsuspecting individuals, but cybercriminals like to take advantage of this time to cause serious security incidents with unforeseen costs.
April Fools’ Day is not the only day these cybercriminals use to take advantage of people’s naivety and lack of awareness, the frequency of these cybercrimes has been growing for a while. With a reported 150% rise in ransomware attacks between April 2020 and July 2021, it is becoming increasingly essential for people, especially employees to learn more about how they can protect themselves as well as their organizations from hackers and different types of cyber criminals.
This April Fool’s Day, Thrive would like to raise awareness around cyber-attacks, share with you some common examples of the tactics used by cybercriminals, and discuss how you can identify scams and protect yourself, your businesses, your employees, and your customers.
Let’s get right into it. Here are some of the most famous internet and telephone scams that you must have heard of:
The CRA Scam:
This is a very common scam in Canada, especially during tax season. You might receive calls or emails that may seem to be from the Canada Revenue Agency (CRA). You might be told that you owe taxes or that you are in trouble with the tax department and that you must make payments or give out your credit card or banking information. Sometimes they might even send you links to fake websites that might look exactly like the real CRA website. It is best to just hang up on the call or delete these emails. The real CRA will never call, email, or text you asking for this kind of information.
The Prize / Lottery Scams:
In these types of scams, you might get a phone call or email saying that you have won a prize, such as cash, a car, an iPhone or a vacation. The scammer will tell you that you need to make a payment to collect your prize, and they might ask for your credit card or banking information. You obviously won’t receive the prize that you were promised but now the scammer can make charges on your credit card, or worse drain your bank account. Once you lose the money, you probably will not get it back.
The Nigerian Prince / Emergency / “Grandparent” Scams:
In these types of scams, the scammers pretend to be close friends or relatives in trouble. A very common one is when the scammer pretends to be a long-lost relative who is a Nigerian prince who needs your help to save his life or to move large sums of money internationally. This scam is so popular and successful at reeling in victims that it’s earned the name, ‘cat fishing.’ They might ask you to send money because of an accident, an injury, an arrest, or a robbery. And just like with all the other scams, this is likely just a way for scammers to get access to your bank account. They often target seniors but anyone of any age can be the victim of these kind of scams.
Other examples include phishing, social media account hacking, fake cryptocurrency, fake charities, fake lotteries, fake surveys, fake kidnapping, fake tech support, fake free stuff, identity theft, and the list goes on and on!
Now that we’ve talked about how hackers commonly target individuals and employees, let’s discuss what you could do to prevent yourself from falling for their tactics. Here are some ways you can ensure that you, your data, and your systems are protected:
1. Adopt a strong Password Management strategy:
It is always advised to use strong, unique, and difficult-to-guess passwords for all your accounts and devices to ensure your data is protected across all different systems. We understand that it can be hard to remember numerous unique alphanumeric combinations (which aren’t a combination of your dog’s name and your birth date) for different accounts and devices, that’s why we recommend using a reliable password manager service. A secure password manager can automate the process of creating, encrypting, and storing individual passwords so that you don’t have to remember dozens of them at all times. Also, don’t forget to keep updating these passwords now and then as another precautionary measure.
2. Utilize Multi-factor Authentication features:
Using a multi-step verification/ authentication process while logging into your accounts and devices adds another layer of security to your data protection strategy. Using a reliable authenticator app or using built-in application-based unique one-time-passwords (OTP) through email, text messages or calls are very helpful in this process. They are used to add another layer of protection to prevent access in case hackers somehow gain access to your passwords.
3. Do NOT click on links or attachments from unknown email addresses:
It only takes ONE wrong click to download viruses or give hackers access to your entire computer system. So, if you receive suspicious emails with links or attachments, don’t click on them unless you’re sure they are from reliable sources.
Thrive provides superior protection against ransomware, viruses, malware, spear phishing, email DDOS and undesirable emails. Our Fully Managed Anti-Virus and Anti-Spam Services are just what you need to strengthen your multi-platform threat prevention strategy.
4. Look for the ‘S’ in https:
Continuing with the above-listed point, another good indicator of a potential problem is if you receive a URL in an email without the ‘S’ after the http in the link. The ‘S’ literally stands for ‘secure’ and indicates that the website has an SSL (Secure Socket Layer) certificate. You should always hover your mouse over any link to see its true destination and if you can’t see the ‘S’, you definitely should NOT click on the URL.
5. Invest in Cybersecurity Awareness Training programs:
The National Security Agency reports that over 90% of cyber-attacks are preventable with basic Cybersecurity Awareness Training. So, by just taking a cybersecurity awareness course and keeping in mind all the points listed in this article, you might already be a few steps ahead of those cyber-criminals and save yourself from serious issues and huge losses!
No matter how large or small a business is, it’s a target for cybercriminals. That’s because it can only take a single unwitting click on a phishing link to grant criminals access to everything on a given network and, in some cases, beyond. It’s also why security awareness training and phishing simulations are essential for organizations who want to transform end users from the weakest link in the security chain, into a truly resilient first line of cyber defense.
Thrive’s Cybersecurity Awareness Training provides the continuous, relevant, and measurable testing and education that businesses need to minimize risky user behaviors and resulting security incidents.
6. Schedule regular Data Backups:
Thrive’s Backup as a Service (BaaS) solutions provide Complete Data Protection for VMware, Hyper-V and Physical Systems among other things.
World Backup Day falls on March 31st every year, the day before April Fools Day, which is perfect timing to make sure all your regular data backups are scheduled are running properly across all devices and platforms. The “I’ll do it tomorrow” approach on World Backup Day could land you in some serious trouble in case you get fooled the very next day on April Fools’ Day!
7. Have a Disaster Recovery Plan ready:
No matter the size, location, or industry, organizations need to take the time to put together a well-thought-out and practical strategy for implementing DR best practices and scheduled maintenance.
Organizations should have an easy-to-understand step-by-step guide on what to do in a data emergency so that employees, partners, and vendors understand their roles, responsibilities, and the resources available to them before, during and after crisis strikes.
We hope you can now better understand how common and dangerous cyber threats, hacking, viruses, malware, ransomware and other cyber attacks are. However, more than 90% of these incidents are preventable with the right kind of Cybersecurity Awareness Training.
If you spend some time learning more about how these cyber-attacks work, how hackers and scammers approach people, what kind of tactics they use, and how you can deal with them, you can prevent cyber attacks and protect yourself from becoming one of their victims.
The World Wide Web is an incredible source of information, innovation, and entertainment! Have fun with it, and keep learning new things, all while staying vigilant and safe on the internet!
Have any questions? Contact Us to learn more about all our services!
Happy April Fools’ Day! We promise we won’t fool you though!
Understanding the SEC’s Proposed Cybersecurity StandardsCybersecurity represents an ongoing challenge for alternative investment firms and the financial industry. And this challenge continues to grow in scope, complexity, and cost. According to IBM and the Ponemon Institute, the 2021 average cost of a data breach in the financial sector was $5.72 million.
In response, the U.S. Securities and Exchange Commission (SEC) has recently proposed new standards for cybersecurity management. According to the SEC’s February 2022 press release, “the proposed rules and amendments are designed to enhance cybersecurity preparedness and could improve investor confidence in the resiliency of advisers and funds against cybersecurity threats and attacks.”
While greeted favorably among cybersecurity professionals and the financial community, the news represents a significant course change for the SEC. To date, there have been no SEC rules or regulations that require financial firms to implement cybersecurity programs. However, the wide-ranging SEC proposal addresses advisor and fund cybersecurity risk, establishes new required elements of policies and procedures for advisors and funds (including disclosure of risks and reporting of cybersecurity incidents), and concludes with a detailed economic analysis.
Read more: How CXOs View Cybersecurity
Breaking Down the Proposed SEC Cybersecurity Compliance Requirements
The recommendations of the SEC compliance proposal can be divided into five areas:
- User security and access
- Information protection
- Incident response and recovery for cybersecurity
- Threat and vulnerability management
- Risk assessment for cybersecurity
Here is a brief description of each area and how the prescribed changes could impact your organization:
User Security, Access & Information Protection. Pandemic-driven remote working and the resulting extended security perimeter have driven significant changes to security requirements, including an increase in multi-factor authentication use. The SEC’s recommendations will require organizations to employ updated security technology and vulnerability management capabilities. These include additional controls for data loss prevention and known registered devices. Many financial organizations have already begun adopting these measures.
Incident Response & Recovery. The SEC’s proposal will require the reporting of threats and other security events (like a vendor breach or a cyber incident). These are similar to GDPR privacy breach reporting requirements but go further. The SEC will also require an activity paper trail and detailed record-keeping around cybersecurity due diligence. If adopted, the SEC proposal will mandate advisors and fund owners to publicly disclose cybersecurity risks and incidents that have occurred in the last two fiscal years.
Vulnerability Management & Risk Assessment. According to the SEC, “Advisers and funds of every type and size rely on technology systems and networks and face increasing cybersecurity risks. The rules would therefore require all of these advisers and funds to consider and mitigate cybersecurity risk.” The SEC’s proposal mandates the categorization, documentation, and prioritization of cybersecurity risks based on a comprehensive information systems inventory.
Read more: Why CISSP Cybersecurity Certification Is Strategic
Effective and Flexible — Striking the Appropriate Balance
The proposed rules and amendments seek to deliver short-term effectiveness while acknowledging the need for flexibility as requirements and capabilities evolve. “The balance is achieved in recognition of the speed of technology change,” explains Ian Bowell, EMEA Information Security Manager. “Being too specific or restrictive and referring to a particular technology standard would be like requiring 4G, and not permitting 5G.”
In short, the SEC is working hard to avoid getting tied up in regulations that could quickly become outdated. Changes in cyber threats and the discovery of new vulnerabilities must also be addressed promptly, and even for the most prepared organizations, continuous change will require ongoing improvements and adjustments.
As a leading Managed Service Provider for the alternative investment industry (including hedge funds, private equity, and family offices), Thrive is well-versed in the industry’s demanding cybersecurity requirements. Thrive’s capabilities, existing framework, and certifications (like NIST and ISO 27001) will help simplify and expedite your firm’s adoption and compliance with the new SEC standards.
Contact us to learn how Thrive can help you meet the SEC’s proposed cybersecurity standards.
Boost Your Collaboration with Microsoft 365’s Real-Time Co-AuthoringBy Christian Wilmot, Client Technical Manager – EMEA
Effective collaboration is critical for organizations pursuing digital transformation. Gartner estimates that almost 80% of workers used collaboration tools in 2021, up from just over half in 2019 — a 44% increase.
COVID-19 and the subsequent shift to a remote workforce have accelerated this adoption. According to Christopher Trueman, principal research analyst at Gartner, “a long-term hybrid workforce model, cloud-based, personal and team productivity technologies, along with collaboration tools, will form the core of a series of new work hubs that meet the requirements of various remote and hybrid workers.”
Microsoft has responded by enhancing the collaboration capabilities of Microsoft 365. The ubiquitous cloud-based service (formerly Office 365) now allows users to share and edit the same documents together — all in real-time.
Real-Time Co-Authoring
Many users have experienced a common roadblock when editing a document in Microsoft 365: “The document is locked for editing by another user.” This automatic message, a Windows file server version of control restraint, appears when multiple team members simultaneously require access or editing rights to the same documents.
With real-time co-authoring in Microsoft 365, once documents are in SharePoint Online or OneDrive, multiple team members can work on the same document at any time without affecting each other’s changes. All edits are automatically saved to the cloud.
Real-time co-authoring addresses many of the issues associated with server-based document collaboration. For example, it helps eliminate multiple document versions by reducing attachment sharing.
Microsoft’s co-authoring capabilities also provide a streamlined user experience. Users simply open and edit a document from Sharepoint; if another user also has the document open, both can edit it simultaneously.
When a document is saved, other users receive a notification that there are new edits and can view those changes immediately. SharePoint Server’s versioning and tracking tools allow authors to protect document integrity by rolling back any unwanted changes.
Instant Notifications With The @mention Feature
Microsoft 365’s @mention is another powerful collaboration feature. Users commenting on a document or presentation can add the ‘@‘ sign with another person’s name, and that user will then receive an email notification with a link to the document. This enables multiple stakeholders to comment or work on the document in real-time.
Reaping The Benefits of Real-Time Collaboration
Even though much of the workforce continues to work remotely (or in hybrid models), organizations are still seeing significant benefits from real-time collaboration. These include:
Enhanced Productivity. By collaborating on a single shared cloud-resident document, users can eliminate the confusion and needless communication associated with managing multiple document versions.
Improved Knowledge Sharing. Simplified collaboration allows teams to capture the knowledge and feedback from all team members, regardless of location. Broader collaboration creates more team ‘buy-in’ and typically yields more effective results.
Increased Job Satisfaction. Real-time collaboration supports a culture of inclusivity, especially for remote workers who may feel isolated from their teams.
Cost Reductions. Legacy collaboration methods often require physical infrastructure (equipment and office facilities) or travel. Virtual collaboration eliminates much of the cost and logistics associated with traditional teamwork.
Extended Reach. Digital collaboration tools allow users to easily collaborate with other teams, even outside their organization. This extended collaboration could include contractors, vendors, and customers.
Optimizing Your Microsoft 365 Collaboration
While Microsoft 365 provides powerful tools to increase your collaboration and productivity, proper setup, configuration, and user training are critical to getting the most out of the platform.
At Thrive, our team is uniquely qualified to help you optimize your Microsoft 365 environment. As a Direct Reseller of Office 365 products and Global IT leader, our team of experts can advise you on the products and services to generate efficiency and improve performance in your organization. Our tailored solutions and deep-domain expertise make Thrive an industry-leading, award-winning MSP to the alternative investment industry.
To learn more about optimizing Microsoft 365’s enhanced team collaboration, check out Mastering Microsoft Teams or contact us here.
How CXOs View the Risks and Rewards of CybersecurityMost CEOs and CFOs in the financial industry will tell you that cybersecurity isn’t cheap. And it’s true — a recent study by Deloitte found that, on average, financial services companies spend 10% of their IT budgets on cybersecurity. A commonly held view among executives is that cybersecurity spending is an expensive precaution. The challenge for IT professionals is to help reframe that discussion with their C-level team and position cybersecurity as an investment, not an expense.
Balancing the Rewards and the Risks
The first question many C-level executives ask when allocating budgets is ‘how will this help grow the business?’ For example, CFOs will invest in increasing production, acquiring new customers, or bringing new products to market faster. At the same time, they’ll seek to contain costs in areas that don’t directly contribute to the revenue line.
A second and equally important consideration is risk. CXOs will ask, ‘what are the circumstances that could prevent us from achieving our business goals, and how do we minimize or eliminate them?’
There are many nuances to the risk discussion. What is the nature of the risk? Security risks can run the gamut from vulnerabilities in cloud platforms, web applications and email services to bad actors exploiting your environment from within. Next, how likely are risk events to occur? What are the financial and operational impacts? What will it cost to address them? Finally, do the benefits of mitigating the risks outweigh the costs?
IT professionals should be prepared to have fact-based discussions with their executive team when reviewing cybersecurity requirements. Industry-specific data, such as the frequency and impact of cyberattacks or the cost of downtime, is always helpful.
Assessing Cybersecurity Risks for Alternative Asset Providers
Here are four industry-specific facts that will help position the security risk discussion with your executive team:
Financial services firms are 300 times as likely as other companies to be targeted by a cyberattack. This finding from the Boston Consulting Group is echoed by the 2021 IBM X-Force Intelligence Report, which states, “Financial institutions experienced 23% of all attacks we analyzed in 2020, up from the 17% of attacks the sector experienced in 2019.”
The probability of a cyberattack is very high for financial services companies. A survey of the UK financial sector found that 70% of financial companies have experienced a cyber security incident in the past year.
The threat is escalating. Attacks targeted at the financial sector increased by 238% between February and April 2020, and ransomware attacks on the financial industry increased ninefold.
The costs are unbearably high. According to IBM, financial services cyberattacks in 2020 due to data breaches cost organizations an average of $3.86 million and took an average of 207 days to identify. Accenture projects that cyberattack on banks in 2020 and beyond will result in banks losing $347 billion, and capital markets will lose $47 billion by 2024.
Cybersecurity as an Investment
While the impact of cyberattacks is all too apparent for the financial industry, articulating the business benefits of cybersecurity can help C-level executives justify budget and resource allocations. These potential benefits include:
Reduced downtime. Ransomware attacks almost always result in downtime or service interruptions. A recent Ransomware Marketplace report found that the average ransomware incident lasts 16.2 days. Every organization calculates downtime costs differently, but for perspective, the Gartner Group estimates average downtime costs at over $300,000 per hour.
Brand Protection. No financial services company wants to be in the news for a services outage or significant data breach. A robust cybersecurity infrastructure can minimize the frequency and impact of attacks and help protect and elevate the organization’s brand.
Customer Retention. Effective cybersecurity protects a company’s greatest asset — its data. Customers are less likely to do business with an organization that has been compromised, and the reverse is true. If your company has an excellent cybersecurity track record, you’re more likely to retain and even grow your customer base.
Taking a Long-Term Approach
Aligning cybersecurity requirements with business objectives is only the first step in establishing an effective security infrastructure. Cyber threats are rapidly evolving, and external events can create new paradigms that impact security requirements. Who would have thought two years ago that today, much of the financial workforce would be working from home?
It is essential to regularly assess your security strategy, priorities, and alignment with business objectives. Ongoing engagement with your executive team is critical, as is a proactive approach. Once a severe cyberattack impacts your organization, it’s too late.
Another proactive option for addressing risk is cyber security insurance. Also called cyber liability insurance, this is a policy that offers businesses a range of options to cover the expenses associated with data breaches and other cyber attacks. These can include costs for: recovering compromised data, lost income, notifying impacted customers, and restoring affected systems.
While cyber security insurance is not a solution that makes you whole, it will reduce potential expenses. Many cyber insurance plans also provide for pre-claim expenses to help mitigate a risk before it becomes an incident.
Partnering with a Trusted MSP
With the exception of larger funds greater than $8B AUM, most alternative investment firms operate without a CTO or CIO, and most funds under $30B AUM do not employ a CISO. Even those that do may not have the necessary in-house resources and expertise to develop and support a strong security infrastructure.
An experienced managed security provider (MSP) can offer services that you may not have the capability to carry out alone. For example, vulnerability assessments can systematically review your environment for security weaknesses. Penetration tests will evaluate your infrastructure by safely exploiting threats. And risk remediation analysis (RRA) can reduce your susceptibility to a cyber attack from a range of tactics, techniques, and procedures (TTPs).
A valued MSP like Thrive NextGen is also well-versed in investor needs and concerns. We help firms anticipate and respond to investor questions about cybersecurity and data protection requirements. Our experienced team has deep domain expertise in the alternative asset industry and can assist in aligning your security requirements with your business strategy and objectives.
With every decision, your C-level team must recognize and prioritize risk before you can reap the benefits. This is particularly true when assessing cybersecurity requirements. That’s why many leading alternative asset companies choose Thrive to help align business and cybersecurity requirements and keep their organizations secure.
Thrive offers the most effective, purpose-built solution for the alternative investment industry. Contact Thrive for a free consultation about your cybersecurity strategy or to learn more about our CyberSuite offering.
Risky Business: Purchasing Grey Market Equipment Can Leave You ExposedFor many companies, 2021 has been a challenging year to procure networking and infrastructure hardware. Transforming networks to accommodate remote workers has stretched already thin IT budgets, and global chip shortages continue to impact product availability and lead times. As early as April, industry leader Cisco predicted that chip shortages would disrupt equipment production at least until the end of the year — guidance echoed by other manufacturers like HP, Dell, and Lenovo.
In this environment, some business leaders are tempted to explore other hardware procurement options, including the grey market. While the promise of lower hardware costs and apparent supply is appealing, the risks to security, network performance, and manufacturer support are considerable.
What Is the Grey Market?
‘Grey market’ products are new devices sold legally but not through a manufacturer’s authorized distribution channels. These products are often sold at low prices through discount websites, and typically sellers will have no local office or representatives. Used or refurbished equipment is sold similarly, sometimes by the same grey market sellers.
Both carry the same risks for prospective buyers.
Why ‘Buying Grey’ Can Be Bad for Your Business
While the initial purchase price of grey or secondary market equipment may be very attractive, customers should fully understand the business risks.
Here are some of the most common pitfalls encountered when purchasing gear from non-authorized sources:
Hardware has questionable origins. Grey market equipment may be counterfeit, stolen, illegally imported, or have damaged or substandard components. Questionable hardware may not perform as expected and can result in significant downtime for unsuspecting customers.
Invalid software licenses. Companies that buy from the grey or secondary market may not be purchasing valid software licensing for their equipment. As a result, they may not have access to manufacturer software updates or security patches. Maintaining updated security software is essential to protecting networks and sensitive data.
No manufacturer warranty or support. Manufacturers track hardware by serial number and often will not provide support or hardware replacement for equipment they determine hasn’t been procured through authorized channels. For example, a manufacturer may delay or even decline support for an end-to-end network issue if edge devices originate from the grey or secondary market.
Expensive inspection and licensing fees. Some manufacturers will provide hardware and software support for grey market equipment, but the process can be lengthy and costly. It often involves the physical inspection of equipment — a challenge if devices are deployed in multiple regional or branch offices. Customers may also have to purchase an authorized software license to gain support. The cost of inspection and licensing fees can run very high.
How Your Managed Service Provider Can Help
Procuring hardware through your Managed Service Provider (MSP) offers a wide range of benefits, including:
Pricing and lead times. Through established relationships with industry leaders like Cisco, HP, and Dell, your MSP can ensure you’re receiving competitive pricing (including any manufacturer incentives) and the best available delivery times.
Configuration and integration. Your MSP will help customize and integrate your equipment to perform optimally in your environment and in compliance with your firm’s security policies.
Flexible support options. MSP support options can be more comprehensive than manufacturer warranty and support. For example, hardware vendor support has specific deliverables (e.g., parts and labor) and may not cover device configuration or the integration of replacement devices. Many MSPs offer flexible, holistic service options that support your whole environment, not just individual manufacturer products.
Warranty, Licensing, and End-of-Life Support. Managing the warranty and support status of all devices in your network can be an administrative burden. Your MSP has the tools to track each device and report on warranty and support status. Your MSP can also alert you when devices require software upgrades or are approaching end-of-support or end-of-life and help build a plan for network additions or refreshes.
Plan Ahead to Tackle Long Lead Times
While ordering equipment through authorized channels will minimize the risk to your business, equipment shortages and shipping delays may be with us for some time. In response, companies should work with their MSPs to understand their device status (especially end-of-support and end-of-life dates), create a migration or upgrade plan, and place equipment orders well in advance of proposed installation dates. In some cases, your MSP may recommend you order equipment as early as year-end to ensure Q2 delivery.
At Thrive, our Procurement team works with manufacturers and distributors to deliver enterprise-level equipment. Our expert Engineering team can review your environment and equipment status and help manage your equipment refresh as needed.
Contact Thrive to find out more about how we can help manage your infrastructure.
Supporting & Securing The Evolving NetworkThe network has become the critical infrastructure of every business. It is the veins that push the new digital lifeblood around the organisation, connecting your people, connecting users to business-critical applications and providing key services to customers.
It is not just important that this network is available, it also needs to perform, be secure and have the agility to adopt to ever-changing business needs.
The criticality of your wired, wireless and wide-area networks is driving the IT team to look closely at how they manage this, the tools they use and the managed services partner they work with.
It All Starts With Visibility
Not only are today’s networks complex, they also serve a wide variety of needs and there is often a chasm between what they were originally designed for and how they are used right now.
Truly understanding your network and how it is being used is essential and this is why organisations are investing heavily in tools to monitor and analyse their network. The aim is to understand what is traversing their network, those heavy bandwidth consumers, rogue applications and also potential security vulnerabilities.
This is not a one-off exercise but a continuous process and one that fits perfectly with a managed service provider. Providing you with powerful insights, benchmarks, flagging priority areas and predicting future capacity requirements.
Embracing SDN & Continual Optimisation
With visibility you are then able to make more informed decisions about embracing SDN and how this can deliver value to every part of your network. For example, understanding the source and destination of your WAN traffic enables you to understand the most optimum route for this traffic and leverage SD-WAN to handle traffic destined to central systems or the internet differently.
SDN redefines how you support and manage your network; many of the manual configuration tasks are taken away with automation and you need less router experts and more assistance in defining the rules and policies. Support of your network becomes less about break-fix and more about a partner that can help you put in place the best practices to monitor and optimise performance.
Securing A Boundary-Less Network
The network is now truly boundary-less; your end-users need access from any location utilising their device of choice, and the systems they access often reside in clouds and on infrastructure that you do not own.
With a significantly increased attack surface area, it is no longer sufficient to simply protect the perimeter, but tools are required for policy-based access, secure end-user devices and to protect people from inadvertently accessing malicious websites or content.
The network is key to this, not only creating a zero-trust environment across your extended infrastructure but acting as a critical sensor, monitoring traffic and behaviour and alerting to abnormalities taking place.
This again changes how we think about support and managed services for our network. The worlds of network management and security are combining, and you need to ensure you are thinking secure network management.
Partnering For The New Era
All of these factors are redefining the role of the Managed Service Provider. Their expertise needs to extend beyond the network and embrace both security and hybrid cloud environments. Their focus can no longer be solely on availability, but the emphasis needs to be around meticulous monitoring and creating the insights that enable you to move your network forward.
The pace at which technology is advancing combined with the growing need for businesses to be more agile is driving organisations to look closely at the partnerships they have in place and ensuring that these partnerships are capable of taking the business where it needs to be.
At Thrive we are very proud of our expertise, tools and capabilities that help our clients to continually optimise and maximise their networks. We would love to talk to you about your specific challenges and explore ways that Thrive can augment your team in delivering a holistic managed service. Please do not hesitate to contact us on 01582 211530 or through our Contact Us page.
Run Flows Directly from SharePoint List/Library Using JSON Column FormattingGood ol’ SharePoint and Power Automate. Two fantastic tools that power users and citizen developers use every day and seldom let us down. They have set the bar for Company Intranets and Business Enterprise Platforms. Continuously adding new features and enhancements. Ensuring all licensees are in the best of hands. As powerful as each is on its own, they are even more powerful together.
This post will cover triggering a flow directly from a SharePoint list or library, for selected items. This can be done using the default OOB Power Automate integration, or by adding custom JSON formatting to create buttons for specific items. I will cover both methods below:
First things first, create a flow with one of the following triggers:
For libraries:

For lists:

Pass in the following trigger parameters:
- Site Address
- List or Library Name
Using the OOB integration:
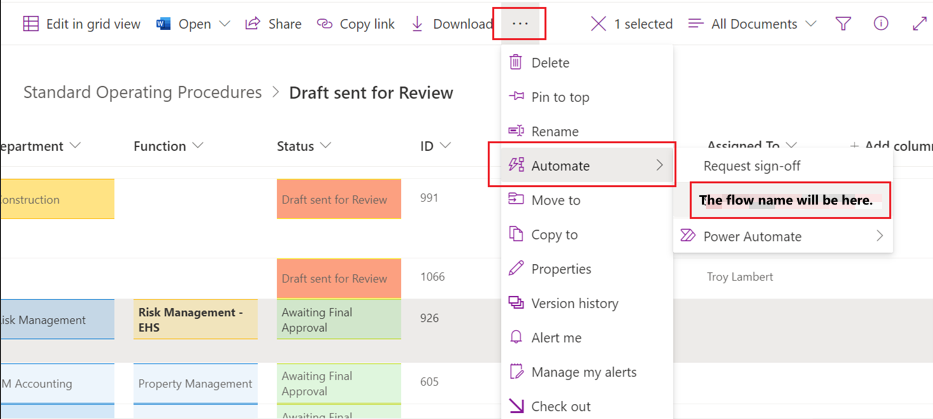
The list or library you entered in the flow trigger will automatically be displayed in the ribbon. To run it, do the following:
- Select an item from the list or library.
- In the ribbon, click the 3 dots (…).
- Hover over Automate.
- Select the flow name from the menu.
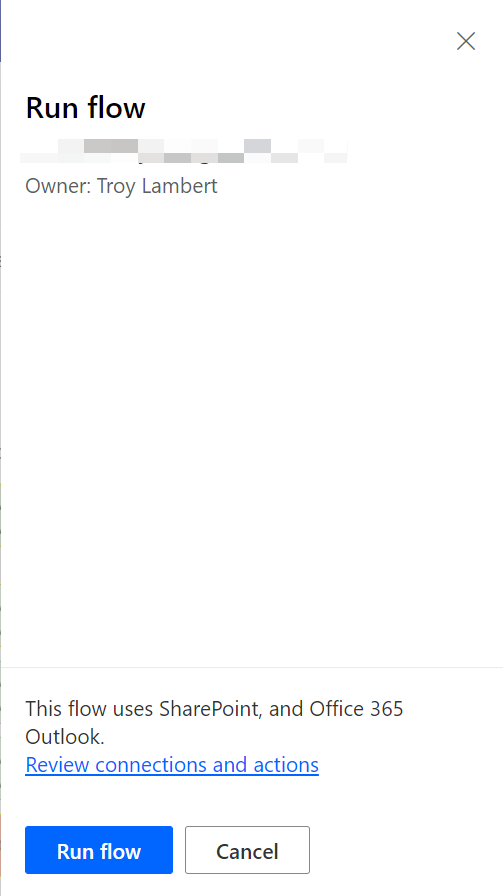
- Select Run flow.
- See screenshots below.
While the OOB method certainly gets the job done and is quicker to set up, it has its inconveniences and limitations. For instance, the number of steps or clicks it takes to run the flow can be a bit much for some users. Understandably so. Selecting an item, then selecting a button from the ribbon menu, then hovering over another button just to be able to select another button that appears, then followed up by one more button to select to run the flow. These days, the less screen navigating, and button clicks the users need to do, the better. That is where the next method has its benefits.
JSON Column Formatting:
This method allows columns to be formatted as a button associated with a specific item. The button will display within the item fields like the rest of the metadata and will open the panel with the Run flow button. Minimizing the amount of clicks a user needs to run the flow.
This method also allows the button to be styled as a link or any way you prefer. Using the JSON formatter. Another neat feature of this method is that you can use conditional formatting based off other columns. In the example below (see screenshot below), the button to run the flow is only visible for items that have an Assigned To. This makes sense for approval workflows. Not allowing approval workflows to be triggered if there is no assigned approver.
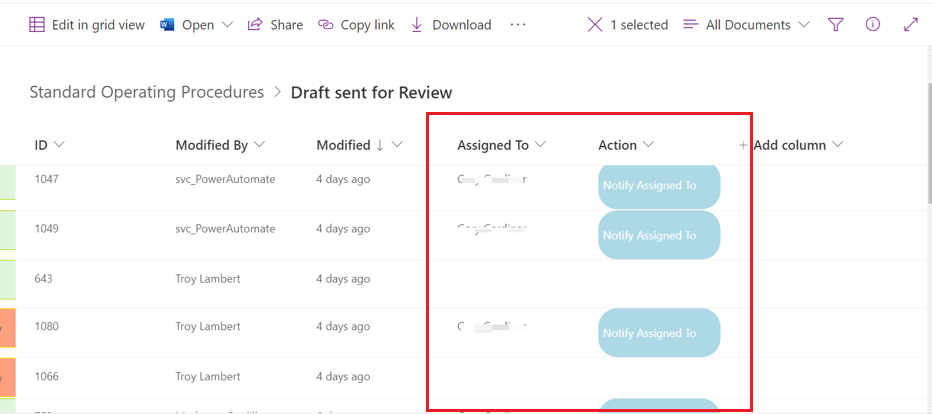
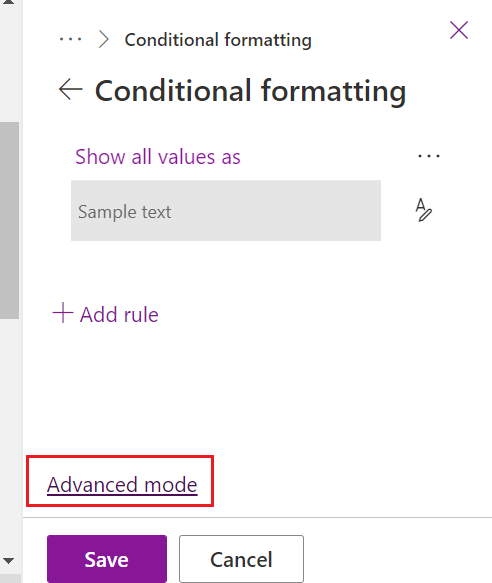
To access column formatting, do the following:
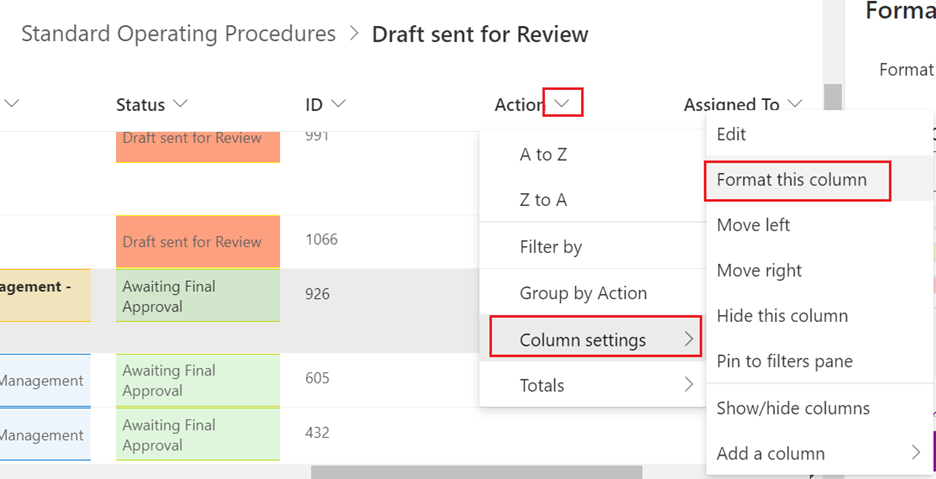
- Click on the dropdown of the column you want to format.
- Hover over Column settings.
- Select Format this column.
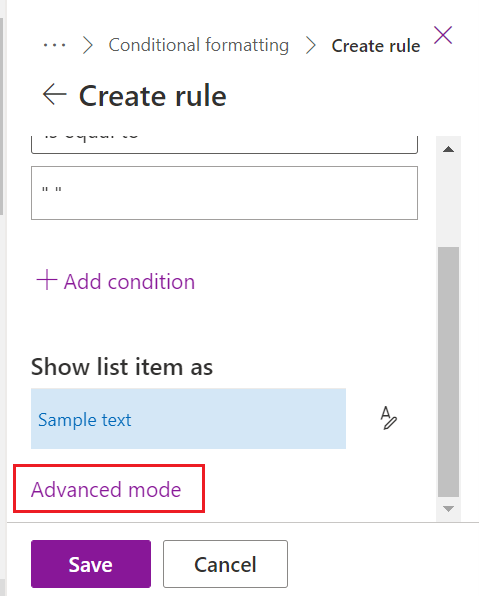
- See screenshot below.
To add custom JSON, do the following:
- Select Advanced mode.
- Paste in the code.
- Select Save.
- See screenshots below.
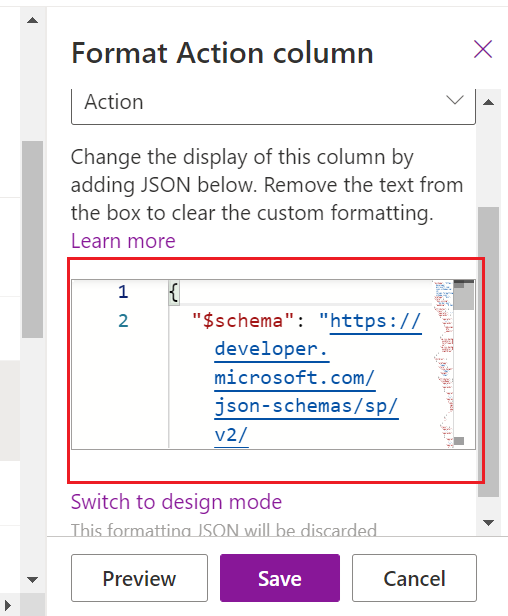
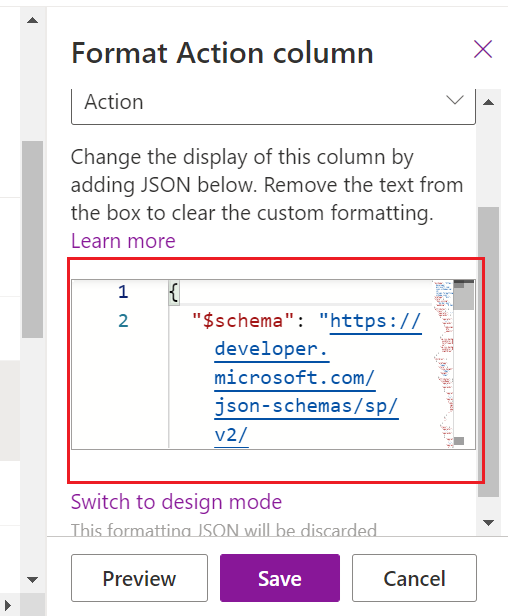
In my example above, to get the light-blue button with white text and have it show only on items when the Assigned To column is not empty, use the following code:
{
“$schema”: “https://developer.microsoft.com/json-schemas/sp/v2/column-formatting.schema.json“,
“elmType“: “span”,
“customRowAction”: {
“action”: “executeFlow”,
“actionParams”: “{\”id\”: \”546e42c3-23fc-41fa-950f-6f7331e7edce\”}”
},
“attributes”: {
“class”: “ms-fontColor-themePrimary ms-fontColor-themeDarker–hover”
},
“style”: {
“border”: “none”,
“background-color”: “lightblue”,
“color”: “white”,
“padding”: “5px”,
“border-radius”: “20px”,
“display”: {
“operator”: “:”,
“operands”: [
{
“operator”: “==”,
“operands”: [
“[$AssignedTo.email]”,
“”
]
},
“none”,
“flex”
]
},
“cursor”: “pointer”
},
“txtContent”: “Notify Assigned To”
}
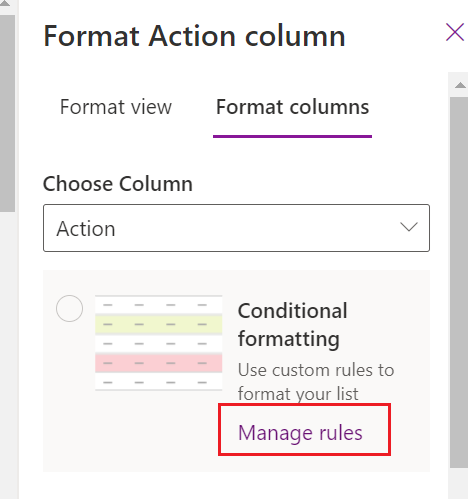
As a pointer for creating your own custom JSON, a neat little hack I find very useful is to use the design mode OOB conditional formatter to intuitively add rules and conditions. This generates JSON underneath, and that JSON can be used as a starting template for add your own customizations to. It is much easier to start with JSON that your SharePoint list already recognizes than it is to start from scratch or find solutions online that need to be completely restructured.
To accomplish this, do the following:
- Select Manage rules.
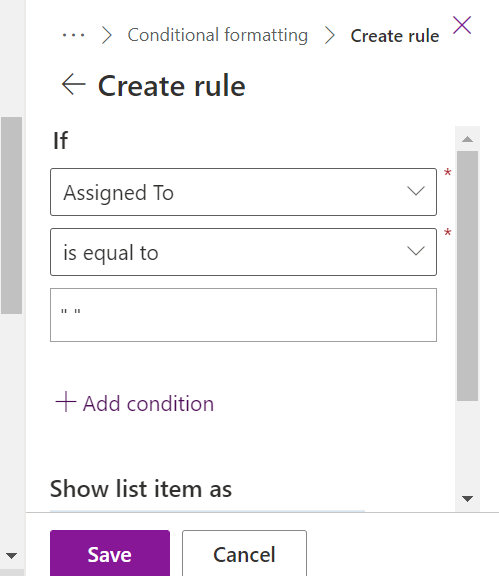
- Select the column to base your condition off.
- Select the operator of the condition.
- Enter the value the operator should look for.
- Switch to Advanced Mode.
- Copy out the code that was generated.
- See screenshots.
That concludes the pot.
Cybersecurity: A Sound Investment in Your Firm’s FutureBy Ian Bowell, Head of Information Security – EMEA
Cybersecurity is now in the direct line of sight for executive management and boards in the alternative asset industry. C-level executives have the power to act and ensure the investment in their IT strategy. An effective cybersecurity program can protect infrastructure against severe threats and eliminate potential reputational damage caused by bad actors.
A company board is charged with guiding and challenging the company’s senior leaders. The board is in the right position to focus on opportunities in long-term, versatile cybersecurity planning. A short-sighted, narrow plan of action should be challenged in this ever-changing landscape.
Board members have a strategic role to play in guiding opportunities for expansion and change in response to threats as well as challenging long-held assumptions.
Relevant questions are:
- How are we responding right now to the threats affecting our industry?
- Where does the leadership team see the business in 2025?
- What can we do to move toward that vision?
However, it’s not so simple or complete. It’s a great step forward when top-level leadership is paying attention. There is still a lot to be done to quantify or address the risks in cybersecurity as well as demonstrate how an IT-based strategy can generate positive business outcomes. The investment is needed to raise the bar, and the wall, against the growing flow of vulnerabilities and opportunistic, well-planned hacking. Insider threat and exfiltration of data are other areas of concern with different indicators and protection tactics.
It’s great to recognize and identify the risk, but what should be done about it? What will happen if the board doesn’t act to fully eliminate or mitigate so many risks out there? There are two main approaches to evaluating cybersecurity requirements: maturity-based and risk-based and both are needed to function optimally.
Maturity-based approaches are great for a quick check across a very wide range of technical, and let’s not forget about physical, security challenges. Risk-based approaches are great for targeting specific prioritized areas, such as staff training, but one is not sufficient without the other.
Read more: Cybersecurity for a distributed workforce.
The maturity-based approach is necessary to cover all the ground and the risk-based approach can help prioritize the weakest areas, but both are needed to ensure a complete process. The maturity approach is useful when starting from scratch, or when facing a new environment, in need of assessment or update. The maturity approach also helps to feed the risk-based approach and roll up assessments across a company, enterprise, or organization with many entities, especially those recently acquired.
Often, a recent acquisition or series of acquisitions brings into focus the nature of cybersecurity as an investment risk, especially in the governance of ESG investors. Here at Thrive Technology Group, we are partnering with our clients to help assess their cybersecurity risk and maturity ultimately leading to a positive impact on their investment portfolio. Any firm in the alternative asset industry not sufficiently secure, and exploited by a cybersecurity attack, sees a significant market hit on the value of their company in the public and private markets. Thanks to mean reversion, this is also an opportunity for those ready to buy low and, subsequently, sell high, if the risk has been evaluated correctly.
Cybersecurity maturity changes over time, ideally improving from strategic planning by executive leadership and company boards. The benefit of a cybersecurity training program or intrusion detection investment can jumpstart the path to a more secure future. Thrive Technology Group is ready to take that first step with you in cybersecurity and be by your side for the journey.
Contact us to learn how you can succeed with Thrive.
Supporting An Agile, Hybrid Cloud EnvironmentYou are likely to be on a journey to cloud with a roadmap to migrate to a hybrid environment that will see some equipment remaining on-premise, some elements moved to a private cloud and over time, increasing use of public cloud services and applications. The mix of this hybrid environment is set to change over time. As you continue your journey, it is also critical that you have a Managed Service Provider that understands and can help you embrace the hybrid world.
During this transitionary time, a partner that understands both on-premises and cloud environments is invaluable. They can assist in the migration of infrastructure to cloud, are experienced at unifying the management of hybrid environments and can add considerable value in helping you understand what is possible and evaluate all of your available options.
Guiding You On Your Options
Along your journey to the cloud there are so many options available to you and it is vital you understand all of these and get help in making the right decisions. Do you create a private cloud environment? What are the best options in terms of public cloud services and how do you manage those applications and servers that cannot move to cloud?
Impartial advice from a partner that has expertise across the whole hybrid world is key in truly understanding all of the choices and recognising that some options you take may just be an incremental step.
Simplifying The Public Cloud
Where there are many benefits from utilising a public cloud service, simplicity is probably not one. For many IT teams it is a challenge to understand all of the services that are available, how these work together, which ones are needed and which pricing model is applied.
In many cases, organisations find themselves paying too much for a public cloud environment that does not entirely meet their needs, not to mention the periodic ‘bill shock’ that can occur.
Getting help here can prove invaluable; accessing specific expertise around Azure or AWS can save you a great deal of time and ensures you get the service you need. Likewise, leveraging the expertise of a partner who understands public cloud can ensure you continue to optimise these services.
Taking Care of The Misfits
Not everything that currently sits in your comms room or on-premise data centre can be moved to the cloud. The challenge is, as you migrate more of your infrastructure you create a disproportionate cost to maintain the misfits.
Utilising co-location can prove to be an attractive option for these applications and you should be relying on your MSP to assist you with the migration to this environment and ongoing management until a point that these applications can move to cloud.
Creating Unified Management of a Hybrid World
The biggest challenge once you are in the hybrid world is consolidated management. Many organisations fail to see the full benefits of moving to the cloud as they don’t unify management and have the additional overhead of managing three environments: on-premises, private cloud and public cloud.
As each of your business-critical applications and the experiences they provide to end-users and customers likely spans across all parts of your hybrid world, ensuring these perform requires a holistic approach to operations. You need visibility and performance insights that spans the different clouds, security and access management that is consistent across clouds and a management framework across all environments.
This again points to the need to have in place a Managed Service Partner that is not focused solely on one specific environment but are truly experts in hybrid environments. Their focus should be on helping you seamlessly migrate across environments and to create next generation operations that holistically covers the hybrid world.
At Thrive we do exactly that; we have expertise in on-premises infrastructure, private cloud environments and public cloud services. We would love to talk to you about your specific challenges and explore how Thrive can provide you a more holistic managed service. Please do not hesitate to contact us on 01582 211530 or through our Contact Us page.
