Executives Decoding Cybersecurity
Thursday, April 13, 2023
11:30AM – 1:30PM
Morton’s The Steakhouse, Orlando, FL
What You Can Expect to Learn:
The Current State of Cybersecurity Threats
Organizational Cyber Risk Mitigation
How to Recover from a Cyber Attack (Preparedness and Recovery)
Evaluating IT Providers for Your Alternative Investment FirmWe’re an IT services provider who is fully immersed in the world of alternative investments and the latest advancements in technology. And because the service and performance we provide are built on commitment and trust, you’ll clearly benefit as a result.
At Thrive, our difference is our people and the talents that they possess. Our seasoned team of technology professionals focus their skills on serving the demanding needs of some of today’s leading alternative investment firms across the globe. Their expertise and knowledge is available as a service to help you plan, implement and assess your overall technology strategy. Think of Thrive as your Talent as a Service solution.
DOWNLOAD PDF

Migrating to the Cloud isn’t always a simple undertaking. There are many considerations any organization must address when it contemplates migrating data and applications from its on-premises solution into a Cloud environment.
Thrive not only has the experience and resources to guide you through the migration process, but also the managed service offerings to help you optimize and manage your applications once they get to the Cloud. Our Cloud analytics tools can determine optimal memory, CPU, and storage tier needs to ensure that your Cloud services are right-sized for predictable billing and performance.
DOWNLOAD Cloud Migration PDF

Guide to Cloud Migration
A goal for any government agency looking at the Cloud is fairly straightforward: cut waste, and enable employees to deliver services to the public faster and better. Choosing a reputable Cloud services provider is crucial for the government and law enforcement agencies migrating to the Cloud. To minimize risk and maintain the security of critical information, be sure that the Cloud provider you choose has a lead agency sponsor or that the Criminal Justice Agency (CJA) has completed a site security checklist.
The first thing a government agency may want to consider is finding a CJIS-compliant Cloud provider that can work within their budget. Many Cloud providers adhere to the consumption-based billing model, meaning that the amount an organization pays can vary wildly from month to month. For government agencies operating on a
strict budget, such fluctuations are not acceptable.
DOWNLOAD CJIS Compliance PDF

This checklist PDF outlines the 3 different paths to becoming CJIS Compliant in Florida (though many states utilize a similar process). Checklist 1 will walk you through becoming compliant internally. Checklist 2 will walk you through becoming compliant with a Cloud vendor that is not yet sponsored by a leading agency. Checklist 3 will walk you through how simple it is to become CJIS-compliant with a lead agency-sponsored vendor like Thrive.
Thrive is a leading provider of outsourced IT infrastructure. Thrive delivers comprehensive managed services and unmatched expertise to drive secure digital transformation. Thrive’s unique combination of industry experts, an automated technology platform, and the Thrive5 Methodology provides customers with a strategic advantage as they look to secure, scale, and succeed.
DOWNLOAD CJIS Checklist

Your firm’s IT goals need to result directly from your business goals – not the other way around. Think about it. When was the last time you actually considered how your business goals interrelate with your IT goals?
The right IT partner will be able to make the connection between your business needs and your technology needs. Be realistic about what your business goals are and communicate them clearly to your IT partner, who should be able to create a solid strategy tailored to your alternative investment business.
DOWNLOAD Our Buyer’s Guide Today!

The managed services market is growing, and shows no signs of stopping. The global MSP market size grew to $238.71B in 2021, and is expected to reach $274B by 2026, with expansion occurring at a compound annual growth rate (CAGR) of 13.4% from 2022 to 2030. Put more simply, demand for managed services is on an accelerated path as more businesses strive to boost operational efficiency, productivity and cater to remote work environments.
For customers, implementing and managing infrastructure technology will continue to become more complex and challenging as firms transition to the Cloud to stay competitive while also facing a constant stream of issues around cybersecurity and network management.
Here’s what else is going on:
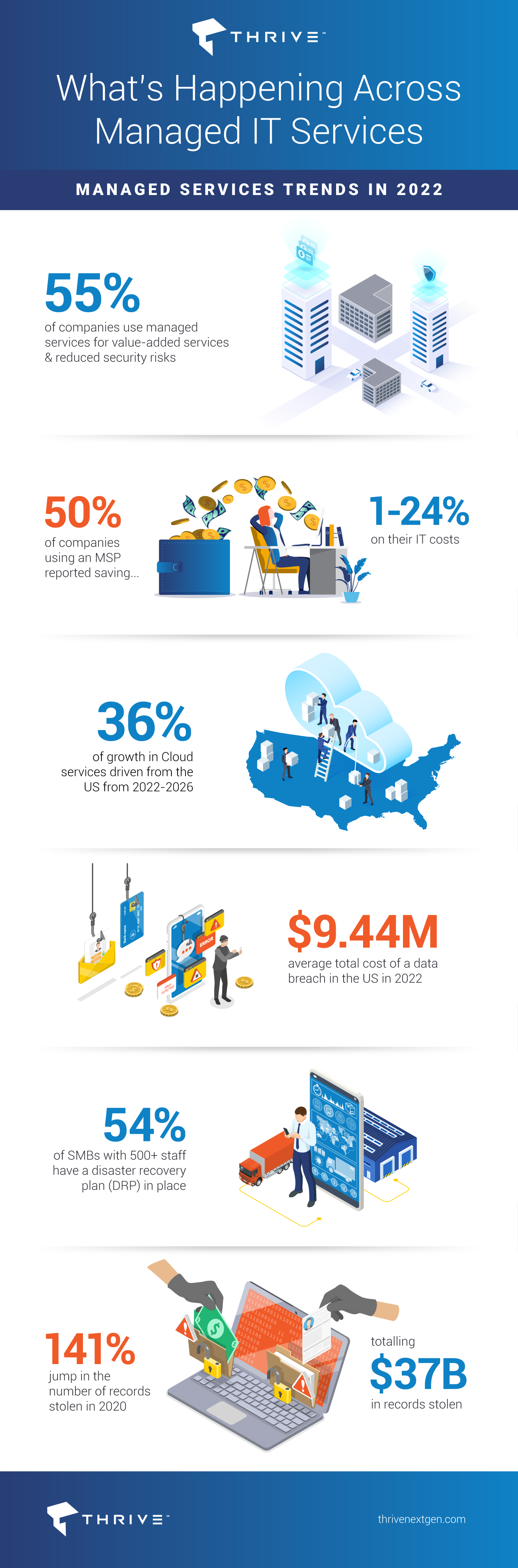
- According to a commissioned IDC study, nearly 55% of companies are using managed services for value-added services and to reduce security risks, which have multiplied since the pandemic’s outbreak as employees work remotely and business partners and customers rely entirely on electronic communication
- One survey by CompTIA showed that 50% of companies who engaged an MSP saved 1-24% in annual IT costs, 33% saved 25-49%, while 13% reported savings of more than 50%
- It is expected that 36% of the ballooning managed cloud services growth will originate from North America between 2022-2026, with the U.S. being the key driver. According to a 2022 report by Technavio, this increasing cloud technology adoption among end-users such as SMBs and large enterprises for automating their business process, including data processing and outsourcing and Internet services, will fuel the growth
- According Statista, the U.S. has the highest average total cost of a data breach at $9.44 million. In 2020, 25 percent of respondents worldwide reported the average hourly downtime cost of their servers as being between $301,000 and $400,000 U.S. dollars
- A 2021 study found that only 54 percent of respondents at U.S. businesses employing 500 or more staff have a documented, company-wide disaster recovery plan in place.
- Globally, there was a 141% jump in the number of records stolen in 2020 – reaching a total of 37 billion, as cybercriminals target more diverse data sources to sell and to use for extortion.
Keeping pace with the rate of technological change is hard enough, it is even harder to rationalize managing IT, digital transformation, and the cyber threat landscape on your own.
Whether you’re managing your IT in-house and need a boost, or are looking for a partner to manage it all – Thrive can help. Speak with one of our experts today to see how our bundled managed services packages can help your organization meet its NextGen IT goals.
How to Enable Data Loss Prevention in Case of Natural DisastersData loss prevention is critical to ensure data and business continuity after a natural disaster. Recover your systems and data as quickly and fully as possible by mitigating risk with the right policies, processes, and infrastructure.
Here are the key questions you should be asking when creating a plan to protect and recover your data in the case of a natural disaster:
What does your current backup situation look like?
The first step toward improving your data protection practices is to consider your current IT infrastructure and systems. Do you have a disaster recovery plan in place? If not, why not?
The assumption that nothing bad will ever happen to your data exposes your business to major risks and devastating losses. It’s not a question of if your data will be destroyed or compromised; rather, it’s when.
Even the most cautious organization will run into situations like natural disasters, hacking attacks, or even user error, where their data is lost or compromised and needs to be recovered. A well-prepared business should always have a comprehensive backup and disaster recovery plan at the ready.
Have you talked to your employees?
By developing and instituting clear internal processes and best practice standards for data management, businesses can help to prevent data loss following natural disasters. Once employees are properly handling files and information day to day and know the correct steps to take during adverse events, your business is a critical step closer to ensuring data protection and successful business continuity.
How often do you test your backups?
Even if you have a backup system in place, how often do you test your procedures and backups to make sure that you can rely on them when you need them the most? It’s not unheard of for a business to lose everything in a fire, and when attempting a recovery, they find out that the entire backup is corrupted or doesn’t work properly. You shouldn’t hope that your backups are reliable, complete, and ready to go; you need to guarantee that they are.
Where do your backups live?
Many businesses rely on their servers for backup, either on-premise or off. In these cases, you should be sure to design a network of backups that offers sufficient redundancy and to have the appropriate resources and expertise to maintain and service them.
What backup approach works for you?
Many organizations that maintain their own data centers also use third party cloud-based solutions for a secondary backup. Having servers in diverse locations supports data loss prevention by minimizing risks due to natural disaster.
A hybrid approach that combines on-premise servers with third-party managed cloud infrastructure can provide geo-redundancy and additional managed services capabilities.
Take advantage of Disaster Recovery as a Service (DRaaS)
The most effective way to enable data loss prevention is to create a seamless disaster recovery plan that includes Disaster-Recovery-as-a-Service (DRaaS). DRaaS simplifies many of the backup and recovery processes, provides storage-related cost savings, and allows businesses to backup their data more frequently with less administrative complexity.
In the event of a natural disaster, a third-party DR service provider can typically help you recover much faster because of their significant and specialized training and resources. DRaaS providers also have the experience of handling multiple catastrophic events in a diverse range of scenarios and can contribute their expertise around handling real world failovers. Third party service providers can rapidly respond when disaster strikes to assist your business in successfully minimizing damage to your data, reputation, and business continuity.
Thrive Specializes in Data Loss Prevention
By following data protection best practices, your organization can weather natural disasters and reduce or eliminate disruption to your business.
Working with Thrive will allow you to avoid costly outages and data loss that could harm your operations, reputation, and profitability. Preparation means businesses gain a competitive advantage by keeping the lights on during the storm.
Stay Safe in the Cloud with Thrive
Is It Time to Take a Hard Look at Your Cybersecurity?Cybersecurity breaches and data privacy/transparency issues are on the rise. Notably, adapting to COVID-19 forced many companies to bypass certain cybersecurity controls,1 which contributed to a 141% jump in breached records globally in 2020 compared to 2019.2
The SEC thus identified this as one of its 2021 priorities and has proposed rule amendments to improve cybersecurity risk governance disclosures.3
Thrive’s cybersecurity solutions can help secure both your data and your assets. Employing both proactive and preventative measures, our cybersecurity consulting and solutions reach well beyond typical reactionary support. Early detection means we’re able to stay ahead of growing and ever-evolving cyber threats—and protect your business. Cybersecurity is a sound investment in your firm’s future.
Taking a good hard look at your current cybersecurity posture now can help secure a solid future in many ways, including:
- Building investor confidence
- Gaining a thorough security vulnerabilities assessment
- Going into Investor audits fully prepared
- Ensuring ongoing financial regulator compliance
Early detection means you’re able to stay ahead of growing and ever-evolving cyber threats—and protect your business. To learn how our team can build customized cybersecurity solutions for your firm, contact us today.
1. Source: EY, October 2021, “How cybersecurity risk disclosures and oversight are evolving in 2021”
2. Source: Risk Based Security report, January 2021. Based on roughly 3,900 publicly reported breaches globally in 2020.
3. Source: The National Law Review, September 2021
Cybersecurity risk management applies to business entities in every vertical. Whether you’re in finance, healthcare, education, or beyond, it is vitally important to regularly assess your information technology assets in order to know your organization’s security posture on an ongoing basis. Especially when signing up for a cybersecurity insurance policy, insurers need to know where an organization’s risk profile currently stands and the steps they’re taking to proactively mitigate cyber risk on an ongoing basis.
A Cybersecurity Risk Assessment involves:
- Taking a look under the hood to assess a company’s technology infrastructure
- Identifying potential vulnerabilities
- Verifying that controls are put in place to minimize organizational risk and maximize information security.
Download our Cybersecurity Risk Assessment Guide to understand how best to calculate your cybersecurity risk exposure.
DOWNLOAD our white paper today!

