Want the best of both worlds when managing the cloud? A multi-cloud approach allows for the strategic use of services from different Cloud providers to optimize performance and cost when running different workloads on different platforms. Thrive recently launched Hybrid Cloud Director to provide clients visibility and management capabilities across the private ThriveCloud, public clouds like Azure and AWS, and on-premise virtual server deployments.
Why the Multi-Cloud Approach Works
We’ll use the example of a thriving e-commerce company to help illustrate the value of the Hybrid Cloud Director. This hypothetical organization wants its resources secured and available 24/7/365, with a need for performance certainty, knowing the resources contracted for are performing at the level required when traffic spikes or seasonal events occur.
These environments will typically be placed in private Clouds. However, if a development team writes new software code for a temporary e-commerce site that is not in the private Cloud, it may lead to the IT team managing workloads in different locations. Plus, it can be a challenge to move the development workload on Azure or AWS to a production workload on the private Cloud without a lot of heavy lifting.
Thrive’s Hybrid Cloud Director does the hard work, and provides visibility into the state of virtual machines, resource usage, and any potential resource conflicts across each Cloud service to ensure smooth performance for users. The platform can work with all of the different environments an organization may have deployed, be it in ThriveCloud, Azure, or AWS, and not only manage workloads, but seamlessly move them between services. It takes only a few clicks to move workloads between clouds, while the platform facilitates everything on the back end.
Cutting-Edge Self-Management Solutions
Thrive has the capability to fully manage multi-cloud deployments, but self-service and direct control of environments may be preferred in many instances. We’ve heard the feedback from those who want that instant access to perform tasks such as virtual machine creation. The old way? Calling a sales representative to create an order for a new virtual machine can take days just to complete the contract. The new way? Within minutes, that machine can be up and running by using the Hybrid Cloud Director.
It’s easier than ever to create new virtual machines, remove machines, or add resources. It’s also easy to log in to the Hybrid Cloud Director and add more storage to machines on the fly if needed, too.
There are Cloud-related challenges, and retaining control over resources and knowing where they’re stored is one of them. Through this single platform, however, clients have visibility and control over their ThriveCloud, Azure, and AWS servers. It’s sort of like the air traffic control platform for diverse cloud environments.
To learn about Thrive’s NextGen Services and what we can do for your organization, get in touch with us today.
Thrive’s ServiceNow-Powered Platform Transforms IT Service ManagementOver the past few years, we’ve worked hard to improve how we deliver managed IT services to clients. With the Thrive Platform, powered by ServiceNow, we eliminate many of the IT challenges organizations face on a daily basis.
The platform removes manual error from the equation, allowing tasks to be handled more efficiently, improving the day-to-day productivity of the IT team and saving valuable time. By building on the enterprise-class power of ServiceNow, the Thrive Platform gives clients better access to service and more accurate environment insights, while also transforming how IT is consumed through self-service.
The Power of Self-Service IT
When it comes to self-service, our goal is to streamline the process for employees and organizations. Whether utilizing a managed services provider or an IT help desk, employees may have to place a call or send an email to solve even the simplest of issues, such as changing a password. Gartner Group estimates at least 20% of help desk calls revolve around password resets. With the Thrive Platform, that once-tedious task is simplified by providing an employee a portal log-in, where a password reset takes just seconds.
Organizations can benefit from Thrive in a variety of ways. One example is in the legal profession. I’ve talked to a number of CIOs in the legal world, and it’s clear the top issue they face is maximizing billable hours. Attorneys need to be spending time on what they do best, not waiting for new passwords or finding time to handle application updates on their own time. And that’s just one quick example. There are so many organizations that can benefit from having a platform that:
- Automates IT tasks
- Enables self-service for employees
- Delivers a 360-degree view of an organization’s technology
IT Service Management Drives Efficiency Gains
The Thrive Platform provides a number of benefits to users in SMB, mid-market, and enterprise organizations.
The platform automates the user creation process, so new hires enjoy a streamlined onboarding process that puts them in control. The outdated method of emails, spreadsheets, and manual entry leaves new hires waiting around for access to key applications and programs. The Thrive Platform brings them up to speed almost instantly.
Even when the onboarding process has come and gone, end users have access to helpful knowledge articles, too. These guides allow users to solve their own issues without contacting IT.
The IT team benefits, too, as the platform offers dashboards with reporting information, including service desk metrics and the ability to sort tasks by order of importance. Instead of manual calculations and outdated user issue reports, IT sees the latest trends and knows where to direct resources.
Want to Learn More?
The Thrive Platform offers several advantages, from increased end user productivity to faster support resolution to less IT time spent on tasks.
If you’re interested in learning more about our easy-to-use portal, get in touch with us to schedule a demo today. It’s the best way to experience the Thrive Platform for yourself!
How to Perform a Cyber Security Tabletop ExerciseIncident response planning is an important part of any organization’s cyber security program. Having a proper plan in place ensures smooth communications and quick decision-making in the event of a breach or attack.
To facilitate planning, the team at Thrive devises cyber security tabletop exercises to help organizations identify and prepare for various scenarios. The goal is to increase situational awareness and facilitate discussion of incident response.
This invaluable exercise clarifies an organization’s incident response plan, identifying what works and where improvements should be made.
Types of Cyber Security Incidents to Prepare For
An incident can occur at any time and include many variables, so it’s not always practical to write step-by-step instructions for each potential one. However, a tabletop exercise provides clarity on how to handle different types of incidents with an actionable strategy.
First, it’s important to understand the types of attacks that can occur.
- External/removable media: An attack executed from a flash drive, CD, or other device
- Attrition: A brute force attack meant to compromise or destroy systems, networks, or devices
- Web: An attack from a website or web-based application
- Email: An attack executed via an email or attachment (phishing)
- Improper usage: An incident resulting from a violation of usage policies
- Loss or theft: A computing device or media used by the organization, like a smartphone or laptop, is deemed lost or stolen
These categories can be used to define specific responses, as different incidents will require certain response plans.
As the tabletop exercise commences, Thrive runs through various scenarios, discussing proper course of action at each inflection point.
Preparation
Before any technology or business practice discussion begins, a risk assessment will be performed. The assessment can be formal or informal, and enables a full understanding of typical network activity while documenting network infrastructure.
Identification
The mock scenario seeks to detect the incident and determine its reach, while involving the appropriate parties. Information sources will be analyzed, including antivirus logs, server connection attempts, and suspicious network traffic.
Mitigation
The primary goal of mitigation is to lessen the impact of a security incident. It’s generally assumed that incidents will occur from time to time, so containing the incident and mitigating its effects are key. This portion of the exercise includes taking steps to disconnect an infected area from the internet, while understanding how to best throttle or block distributed denial of service (DDoS) traffic.
Remediation
Ensuring impacted services are once again reachable, the remediation stage involves discussing best practices for security patches, antivirus signature database updates, and restoring data from uninfected backups. If disclosed data cannot be recovered, a report must be provided to executive management, and applicable legal and customer teams must be made aware of the issue.
Recovery/Root Cause Analysis
Recovering from an incident is key to future success. The analysis exercise identifies what went right, what went wrong, and provides a timeline of important events. We will discuss the results of the incident, the lessons learned, and explain the steps to take to respond more effectively in case of a real attack.
The Benefits of Completing a Tabletop Exercise
A tabletop exercise raises security awareness within an organization, highlighting what could occur during a real cyberattack. It is meant to highlight deficiencies and weaknesses, so proper steps can be taken to prepare an efficient organizational response in advance.
The exercise determines whether an organization can coordinate communications, business operations, and external parties, with every scenario designed to focus on the likeliest threats.
Thrive provides enterprises with the tools to facilitate a tabletop scenario, but we also have the capability to run the exercise from beginning to end. To get better insights into the readiness of your organization’s cyber security incident response plan, contact our experts today.
4 Reasons Why Alternative Investment Managers Should Consider the Public CloudThe public cloud is in demand for small start-ups and larger existing firms alike. How can you take advantage of all the cloud has to offer?
Here are the benefits to consider when moving from on-premises to cloud computing, including real-life examples from Thrive, Managed Service Provider (MSP) and trusted advisor to the alternative investment industry.
1. Layered Security
Human error is the biggest security risk any company faces. In the cloud, you remove all internal human error from physical data center security. Working with an MSP experienced in creating cloud environments, you have the ability to add layers of cybersecurity around data access.
For example, Thrive applies automated cybersecurity warnings to our clients’ environments to detect any attempted breaches immediately. “One of our hedge fund clients recently experienced an attempted breach, which was immediately identified and blocked via multiple conditional access policies, resulting in zero data loss or compromised accounts,” stated Michael Laudenslager, Cloud Architect at Thrive. “Prior to becoming an Thrive client, that same hedge fund experienced a security breach resulting in data and monetary loss. The breach was not discovered for a few days.”
The importance of engaging a knowledgeable vendor was underscored by a recent survey[i] reporting that security misconfiguration errors accounted for 67% of all cloud data breaches in 2020. An expert vendor will know how to avoid these costly pitfalls.
Another security consideration for moving to the cloud is the outages that data centers can suffer. In the public cloud, you don’t have to worry about the physical security and availability of your company’s data. Mr. Laudenslager cited Superstorm Sandy: “We had clients whose buildings were flooded, and some lost equipment.” The risks associated with on-premises equipment vanish for firms fully invested in the cloud.
2. Cost Reduction and Increased Revenue
Right now, the physical location of your data center is racking up costs for maintenance, energy, a generator, and support personnel. The equipment housed inside will deteriorate over time, giving way to necessary and costly upgrades, on top of software licensing and renewal fees. There is the added expense of Disaster Recovery (DR), which requires a second location to allow seamless transitions from the primary system in the case of a disruption. Switching to a qualified public cloud service provider can reduce these operational costs, as well as infrastructure overhead.
The cloud’s flexibility can also drive revenue. “Our customers are hedge funds, private equity firms, other alternative investment companies, and quant [quantitative] funds,” said Mr. Laudenslager. “When we look specifically at quant funds, they trade by programming. The public cloud’s flexibility and agility support them on high-volume trading days, increasing resources based on the volume of trades.” For these types of funds, prices can drop within seconds, so the cloud’s speed is paramount, yielding increased revenue.
Hedge funds, by their very nature, are ideal for the cloud’s flexibility. The average hedge fund employs less than 20 people. If you have14 people in five countries, you can share the same functionality and save money because you don’t need a data center in every single country or location (an additional cost savings).
Migrating to the cloud can also yield cost savings[ii] by eliminating telecom expenses, offloading storage, streamlining data-intensive processes, and creating a unified infrastructure.
3. Flexibility and Agility
It can take a short amount of time to go from a blank slate to a fully functioning cloud environment depending on complexity and need. If you only need to use certain parts of the public cloud, such as solely using Microsoft Teams for collaboration, you can be set up and configured in a matter of hours, with zero interruption to workflow.
With the public cloud, you can easily increase computing and trading speed point-to-point from your office to the data center. AWS’s Direct Connect and Microsoft’s Express Route offer different storage tiers and processing speeds. And it’s important to note that the public cloud is completely customizable for speed and resources, depending on your needs.
In addition, the public cloud allows you to process a tremendous volume of workflow, using collaborative SharePoint sites or web apps, without concerns about memory and storage space. And for international operations, you can go global in minutes, setting up operations in the UK or Singapore, enabling you to expand your global business faster and eliminating the need to be physically in those locations.
A 2017 Harvard Business Review study reported[iii] that “business agility/flexibility” was the primary reason companies either migrated fully to the cloud or adopted a hybrid cloud architecture.
In this fast-moving, agile world we now live in, the public cloud gives your IT infrastructure flexibility to keep up with business, social, and/or environmental changes that may materialize.
4. The Public Cloud Is Always Progressing
New functionality is updated daily in the cloud. At Microsoft alone, just under 1,000 new features are currently at various stages in its roadmap. However, your firm doesn’t have to lift a finger to accommodate these upgrades-—an experienced cloud provider handles all these new functionalities and administers all your software upgrades for you.
As the adoption of the public cloud is exploding, you as a customer are constantly benefitting from extensive R&D and testing. Your company gains from all these innovations without having to undergo the costs of testing or any potential issues that arise during the testing process.
Recently the cloud has been constantly innovating[iv] in response to the pandemic, as enterprises’ IT infrastructures become more complex and remote working expands to home offices and devices.
Lastly, cloud providers build compliance tools and configuration options into their infrastructure, so you have peace of mind your technology solutions are compliant. These compliance features enable you to easily configure and/or audit your environment to address discrepancies in governing body regulations and compliance policies, making it easier to adhere to government regulations.
In the world of alternative investments and hedge fund cybersecurity, there’s nothing you can’t get in the cloud. If you’re interested in learning more about what the public cloud has to offer—security, flexibility, cost savings, and increased revenue—let’s talk about the best solution to meet your business requirements.
[i] Security Magazine; Nearly 80% of Companies Experienced a Cloud Data Breach in Past 18 Months; 6/5/20
[ii] InfoWorld; Where to look for cost savings in the cloud; 3/16/20
[iii] Data Kitchen, Your Cloud Migration is Actually an Agility Initiative; 9/10/20
[iv] The Cube on Cloud; 12/21/20
How Thrive’s Layered Cyber Security Bundle Protects Your DataToday, it’s hard to go more than a few days without hearing of some sort of cyber security issue or breach on the news. Cyber security isn’t just a “set it and forget it” type of endeavor — it’s something that requires planning, detail, and attention.
Thrive’s Cyber Security Bundle leverages best-in-class technologies to educate and ultimately protect end users. We’ve worked hard to protect businesses and organizations by preparing a multi-layered cyber security plan that mitigates the enormous consequences a data hack can have.
Protect Against a Potential Data Breach
Data breaches affect organizations in many ways, both monetarily and psychologically. It’s possible the issue may be smaller in nature; perhaps an employee’s laptop is infected with ransomware, causing a lost day of work or decrease in productivity. The employee may have had personal information on that laptop, even if it was a work-issued device.
If a large-scale database hack were to happen, that personal information exposure may be more widespread. The database could hold valuable client information, including usernames, e-mail addresses, and phone numbers, and the PR ramifications can be immense.
No solution provider can promise organizations they will never be breached. A company that stays in business long enough may deal with a cyber security issue at some point, but it’s imperative to create layers of security to protect the organization.
Just five years ago, it was widely believed antivirus software on a workstation and a firewall would do the job. Today, with many people working from home, the firewall idles in the office while antivirus protection only does so much. More specifically, signature-based antivirus protection may not catch a malicious file, which is why we look at anomaly-based antivirus protection while adding a cyber security bundle to deliver best-in-class endpoint security.
Targeted Cyber Security Training That Informs
Thrive’s Cyber Security Bundle offers protection for end users against:
- Malware
- Social engineering
- Phishing
- Ransomware
One of the top bundle benefits is the targeted training it provides for employees. It’s easy to tell someone not to click on a phishing email, but is that practice being followed? Thrive sends simulated phishing messages, changing the patterns and language to make each one a challenge. While we do inform organizations that these simulated phishing exercises exist, they are designed to mimic the real thing. This is all in the name of better informing end users so they can easily pick up on real phishing attacks.
We devise quarterly training for organizations through videos, too. These videos are short, typically around five to 15 minutes in length, and discuss important topics like what phishing emails look like, social engineering, and how to create strong passwords. Security and IT can have a negative connotation and imply a broken process that needs fixing, but these training videos open the lines of communication and provide end users with the information they need.
Educating and protecting end users mitigates data and productivity loss, which is why Thrive offers end user security solutions through our Cyber Security Bundles. Find the right fit and bring your cyber security practices up to speed today!
Best Practices for Building a SharePoint Intranet for the Remote WorkforceA SharePoint intranet is a connected workspace that allows teams within your organization to connect, collaborate, and share information, whether you’re in the same building or distributed across the world. When built correctly and used successfully, intranets are a powerful tool to engage people and to connect them with the knowledge and resources they need to do their jobs.
To ensure your team correctly utilizes the powerful capabilities of an intranet, we put together this guide of nine best practices to follow to help you get started.
DOWNLOAD our white paper today!

Microsoft SharePoint helps organizations achieve specific collaboration, business process or operational goals as part of their larger digital transformation strategy.
Learn how to build a comprehensive SharePoint governance plan that works for your organization by managing the three main pillars: IT governance, information management and application management.
DOWNLOAD our white paper today!

Microsoft Teams is a great team collaboration solution that Thrive supports as part of our Digital Transformation services. After integrating the people, content, and tools into Teams, it’s important to establish a strong governance approach to ensure long-term satisfaction and security.
Learn a more organized and strategic approach to preparing, documenting, configuring, implementing, communicating, maintaining, and adjusting your Teams governance journey.
DOWNLOAD our white paper today!

Thrive White Paper Teams Governance Cover
How the Thrive5 Methodology Delivers IT Best Practices
Are your applications and data properly protected? Our Thrive5 Methodology helps answer that critical question for businesses every day.
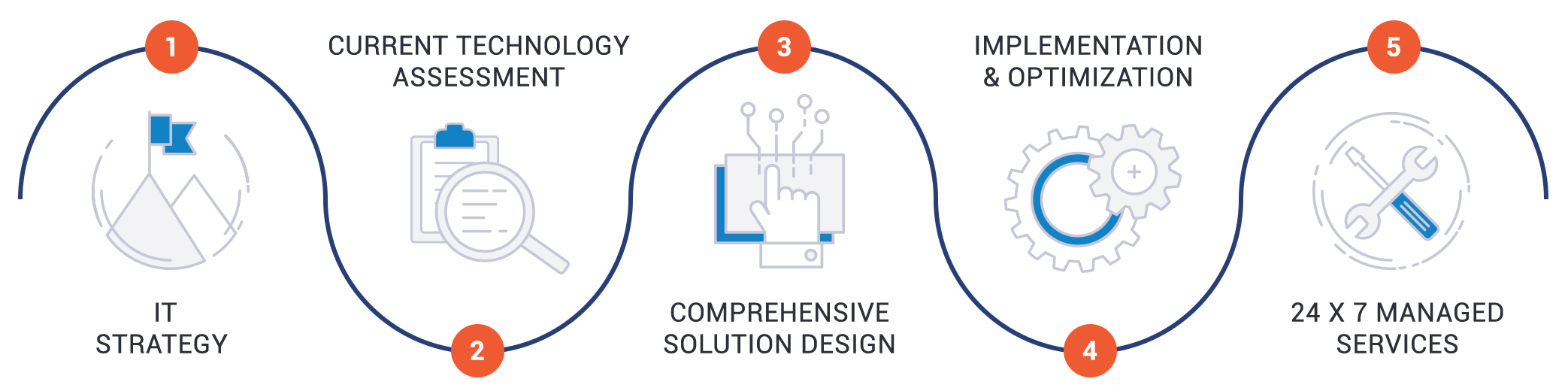
Our consultative approach takes a deep dive into multiple segments of IT operations and infrastructure to understand business requirements and provide solutions. At Thrive, we’re well-positioned to provide solutions to existing IT issues while working to prevent potential emerging threats.
The Thrive Technology Assessment
Does your organization need someone to lift up the hood and take a closer look at your IT operations? There’s a good chance the answer to that question is, “Yes.” During the initial phase of the Thrive5 Methodology, we perform a technology assessment that includes an in-depth review of your:
- Servers
- Networking
- Cybersecurity
- Governance
- Messaging
Looking at the existing solutions, we compare them against IT best practices to identify gaps that can be eliminated to mitigate risk and deliver greater efficiency for the business.
We all know that in 2020, IT departments were thrown a significant curveball. More specifically, backup and disaster recovery became a critical piece of our assessment process as many Americans worked from home. Just last month, a large-scale Google outage struck, affecting end users and their ability to access e-mail, YouTube, Google Drive, and Google Classroom, among other things. We help organizations plan for these types of scenarios, among others, to mitigate downtime.
We evaluate business processes as well as technology to ensure you’re meeting your company’s uptime requirements. What is your business willing to tolerate from a downtime or data loss perspective when unexpected events occur? Typically, that tolerance is low. We peel the layers back to understand your current technology stack and make specific recommendations to fill in the gaps and provide perspective on cost and priorities.
Solutions that Meet Your Specific Needs
Nine times out of ten, a company is missing critical tools that enable them to understand the current state of their environment on a real-time basis. That makes it nearly impossible to know how to deploy upgrades and new solutions.
For example, we have seen several organizations using on-premise hardware when it makes more sense to be in the cloud. Part of our assessment process maps out how our clients will migrate to the cloud. Some customers require a full overhaul, while some may only need minor updates. What the majority, if not all of our customers need, is the latest generation of security products, including our fully-developed SIEM/SOC solution, EDR-based protection for workstations, next generation firewalls, and disaster recovery.
As many of our services are standardized and consistent across the board with best practices, we have built out our service delivery and account management structure with the flexibility to align with our clients’ specific needs. Our service delivery teams also have vertical alignments, enabling them to provide additional value and expertise in both their recommendations as well as implementation and a best-in-class customer service experience.
__________
No matter where your employees are currently working, the team at Thrive is here to answer the call and provide solutions through our Thrive5 Methodology. To learn more about creating an IT roadmap for your organization, get in touch with us today!
The Thrive Platform: NextGen IT Service DeliveryFor businesses of any size, keeping employees connected, working and productive is critical. But managing the IT needs of an organization is complicated. That’s why the NextGen technology experts at Thrive have created the Thrive Platform, powered by ServiceNow.
