There are around 2,500 museums in the UK and inside each of them are incredible artifacts that define our heritage and gives us insight into how the world we live in today has evolved. The National History Museum alone has some 80 million artifacts, most of which are not on display at any moment in time.
Thrive is extremely excited and honoured to be part of an initiative aiming to leverage the ‘digital world’ to make our heritage accessible to more people. This initiative is focused on ‘Preservation to Presentation’ and, in straightforward terms, is looking to ‘digitally capture’ those artifacts in our museums. Both Augmented Reality and Digital Presentation Tools have, provided schools, higher education, historians, scientists, and the general public with access to these artifacts
The programme is being supported by The Natural History Museum, Imperial War Museum, Science Museum, British Film Institute, and many creative and technology leaders.
Imagine the scenario, a classroom of children is studying dinosaurs, and a trip to the Natural History Museum might be out of the question. However, by clicking on a QR code in the classroom, the children will have the ability to analyse a Tyrannosaurus Rex using Augmented Reality. This tool would be both a powerful, immersive, and transformational learning experience for the children.
Thrive is working alongside Cisco to support this initiative. The role we are playing is providing the private cloud based platform on which this digital content can be accessed. Our highly resilient and secure private cloud environment, built on leading Cisco technology, is hosting both the presentation technology and the data providing the performance and scalability required for such a service. Equally important is the connectivity side; as the initiative looks to run pop-up museums across the country, it needs a service that can cope with significant peaks in bandwidth. A requirement that Thrive can meet through the unique design of our private cloud offerings.
At Thrive, we work with a broad range of organisations, helping them on their digital transformation and their journey to the cloud. This initiative is an invaluable opportunity for us to apply our skills and experience to a fantastic project with far-reaching benefits to the whole country.
If you want to learn more about Thrive’s data centre facilities, the co-location, private cloud, and hybrid cloud services we provide, please look at the Thrive Cloud Services webpage or get in touch with us here.
Why Hiring a Virtual CISO (vCISO) is the Smart MoveFinding a qualified Chief Information Security Officer (CISO) who will be a reliable resource is a challenge, and retaining one even more challenging. Protecting company information, data, and end users is a must. That’s why Thrive has created a Virtual Chief Information Security Officer (vCISO) program, which helps companies fill the gap between business strategy and security operations.
There are several ways in which a company can benefit from hiring a vCISO to assist with strategy, guidance, and oversight. This emerging role provides an outside voice committed to getting the job done efficiently, avoiding internal politics, and eliminating the need for a lengthy search for a CISO.
Why Hire a vCISO?
It’s the dream of every organization to have a long-tenured CISO in their C-suite: a cybersecurity expert capable of driving innovation. That being said, it’s not always the reality.
Larger companies may dedicate time and effort to recruiting and training a CISO, as their resources allow them to do so. Plus, these larger organizations tend to have room in the budget to attract what a CISO commands in salary. That being said, challenges still exist – the average CISO tends to only stay with a company for just about two years according to Nominet, and small- to medium-sized companies may need the services of a CISO, but might not be able to afford one in a full-time role.
As many organizations have an immediate need to address security concerns, it can be difficult to have to wait six to nine months to recruit, onboard, train, and fully immerse a CISO in their role. A vCISO can hit the ground running immediately, be an objective outsider, and provide near-immediate value.
CISOs may also not have the desired combination of business and technical capabilities, struggling to find the balance that is required to manage both business policies and cybersecurity needs – simply put, there aren’t many “unicorn” CISOs available.
Benefits of Hiring a vCISO
When hiring a CISO, organizations have access to an expert, but it tends to be just one person in the role. With vCISO services, an entire team of experts is working to implement a cybersecurity plan and responding to potential threats.
Thrive designs its vCISO services and customizes an Information Security Program that complements business strategy and risk tolerance. In the Discovery stage, we identify what policies and procedures are in place, review internal and external partners, and better understand the current state of affairs.
After acquiring that information and insight, a Risk Assessment is performed, which in turn allows us to create a Current State Analysis document that shows existing deficiencies that should be addressed immediately. In the Development phase, we design and develop a program that’s tailored to the organization. Of course, this is not just a one-time solution – information security is an ongoing effort and the threat landscape is always evolving. We constantly revise our clients’ Information Security Programs to meet regulatory, audit, and compliance regulations.
Our vCISO services fit small- and medium-sized businesses, along with mature organizations requiring assistance with specific policies and governance requirements.
Is a vCISO the right fit for your organization? Speak to our team to learn more about this emerging role and why vCISO may be the best fit for you.
Thrive’s Virtual CISO Webinar: Key TakeawaysThrive recently held its vCISO webinar, hosted by CRO John Holland, who was joined by Andrew Archibald, vCISO, and Dave Sampson, VP of Consulting. In this webinar, Andrew and Dave discussed the role of a vCISO, the importance of implementing a security program, and why organizations must continue to nurture a security program.
Check out the highlights from the webinar below, and get in touch with the Thrive team to learn more about our vCISO offerings.
Dave Sampson, VP of Consulting
On the latest cyber attacks in the news:
When we look at a lot of the attacks this year, we’ve identified some common trends. As we’ve watched the news, it’s clear many of the organizations attacked have no formal security program. There needs to be a formal security program, and that has to start at the executive suite, starting from the top and working its way down. Having a comprehensive security framework behind security strategy is critical, too. Buying a specific tool may require some areas in the framework, like email hygiene, multi-factor authentication, and disaster recovery. When we see news stories and hear of the unpredictability of recovery time, that means the recovery plan probably hasn’t been validated and tested on a consistent basis. Third-party vendor risk has been in the news, too. When you’re providing data to third-party vendors, who is accessing it? If it’s stolen, it’s just as impactful to you as it is to them.
Why a vCISO is the right fit for an organization:
A vCISO coming in on a part-time basis provides the knowledge and the ability to collaborate. Not all organizations need a full-time CISO, and there’s a shortage of full-time CISOs on the market. A vCISO can provide a better cost model and work with executives throughout the organization, and be results-focused. You’re also getting the experience of several individuals. The Thrive consulting team is certified and able to socialize requirements and find the best solutions. We work in different verticals and have the experience to enhance your security posture.
What a vCISO looks like:
This individual will help spearhead a proactive, security-first approach. We have a policy resource library that a vCISO will help modify to meet your needs. A vCISO can also help plan sustainable business operations, and ensure recovery plans are being validated on an annual or semi-annual basis to create a strong cyber security posture.
Andrew Archibald, vCISO
On how Thrive’s vCISO foundation is built:
The Thrive vCISO offering is built on two foundational concepts. The first is the Center for Internet Security (CIS) framework. Thrive has worked with CIS for many years. It’s an easy to understand and approachable framework, yet extremely comprehensive. CIS has added controls around cloud security and remote work in response to the pandemic, as well. It maps to all of the other frameworks, including NIST and ISO. The second component of the vCISO service is built around the ISACA Certified Information Security Manager (CISM) credential and the domains for them. We make sure that there is a robust security culture throughout the organization, as information security is not just a box that is checked. Ultimately, this risk-based information security program is customized to your organization, taking corporate and IT strategy into consideration. We also make sure that recovery measures are in place to respond to, mitigate, and recover from a security incident.
What you get from the vCISO program:
If you don’t have an information security program, we will help develop and maintain a program that complements business strategy and risk tolerance. Some organizations are more willing to accept risk, and others are risk averse, and we take that into perspective when developing a plan. Our offering is based on creating reasonable information security measures to protect corporate assets. This approach is also eminently flexible. Every company has unique security challenges and concerns, and we remain flexible to address challenges and concerns organizations are facing.
On the vCISO process:
We have a 5-step process to implementing and maintaining the vCISO program, starting with Discovery. In this phase, we’re trying to better understand the existing information security program, or designing one if there is nothing currently in place. We look forward to talking with the board of directors and senior leadership, along with the IT experts to get a grasp of technologies and how they are implemented. We want to make sure the appropriate protections are in place in the Risk Assessment phase, and address any glaring deficiencies immediately.
The Current State Analysis includes a 20-40 page report with recommendations to implement ranked by importance, with remediation items managed and tracked appropriately. In the Information Security Program Development phase, we work to develop a security-focused culture, and create an umbrella document, the Comprehensive Written Information Security Program (WISP), that lays out security strategy, and can be shared with auditors if needed. Of course, day-to-day operations and nurturing will continue, providing updates to management as needed and conducting annual policy and procedure reviews, while making sure the risk profile hasn’t drastically changed.
Missed the Thrive vCISO webinar and want to learn more? Click here to gain on-demand access!
What is Azure Virtual Desktop?As has become evident in the past few years (particularly in the last year), remote work is no longer just a possibility, but a reality. Organizations have seen the value of completing work from anywhere, but many have used patchwork solutions and short-term fixes to help establish a remote workforce.
Azure Virtual Desktop provides business leaders with a scalable, long-term solution, something many organizations are looking for. The right tools are required for collaboration and innovation, but important information and data must be protected in the process. Azure Virtual Desktop enables a secure remote desktop experience from any device at any time, providing end users with the access they need to get the job done.
Running Azure Virtual Desktop on the Cloud
Running Azure Virtual Desktop on the Microsoft Azure Cloud platform allows users to set up a multi-session Windows 10 deployment that provides a scalable Windows 10 instance accessible from anywhere. An end user gains access to Azure Virtual Desktop via a company-issued device, a shared computer, or their own device. For on-the-go employees, the benefits are clear – no matter where someone is, they’re always connected to a full desktop experience with the proper functionality and customization they’re accustomed to.
Organizations will realize cost savings immediately. Hosting on Azure requires less infrastructure than a traditional setup, and there’s no need for costly servers and the space required to house them. Plus, with employees working from anywhere, office spaces can be consolidated, giving users the option to log on either from home or perhaps a co-working space. Should IT departments choose to forego the process of searching for and maintaining hardware, bring-your-own-device (BYOD) is an option. Allowing employees to use their own device reduces costs and ensures a certain level of comfort.
In a BYOD setup, a company can continue to grow without having to focus on costly IT infrastructure or a lengthy procurement process. Since an Azure Virtual Desktop is always up to date, it has the latest security features capable of detecting threats and taking action, and for IT departments, is an alternative to purchasing expensive new equipment or backup and disaster recovery services.
Azure Virtual Desktop Benefits and Considerations
Azure Virtual Desktop deploys and scales in a matter of minutes, with the ability to use existing licenses so you only pay for what you use. For example, if you’re already signed up for Microsoft Office 365 or an enterprise Windows version, a virtual desktop instance can be set up for each user at no extra cost. Remote users gain access to a virtual desktop interface from anywhere, regardless of device type:
- Windows
- Mac
- iOS
- Android
- Any device with an HTML5 web client
IT administrators can increase the number of virtual CPUs, virtual RAM, and create more virtual hard disk storage with just a few clicks. Azure Virtual Desktop can also be the first step towards bringing legacy applications to the Cloud, for those yet to implement a software-as-a-service (SaaS) solution. This allows for the hybridization of the work environment; if an end user requires a full desktop, Azure Virtual Desktop is the solution, but if they only require access to O365, they can work locally.
As the platform is rolled out to employees, organizations must consider the needs of the end user. While an IT department and a group of tech-savvy professionals may enjoy having access to a virtual interface, some members of a team may require further training and coaching on how to use the technology and how to ask for additional resources if they’re required. Our Thrive team provides detailed training prior to deployment.
Azure Virtual Desktop is a great opportunity for organizations to maximize the benefits of the Cloud. Plus, Azure Virtual Desktop is just one more way to provide employees with remote desktop access and the ability to accomplish tasks even if they’re nowhere near the office. To help your organization deploy Virtual Desktop on Microsoft Azure, get in touch with us today.
7 Must-Know Information Technology AcronymsTech acronyms are everywhere these days, but unless you’re an IT expert, you may not have a full understanding of these acronyms and what they’re trying to tell us. Some days, it’s hard not to run into a new tech acronym you’ve never heard before.
At Thrive, we are always happy to spend our time developing targeted solutions for clients and providing necessary services. At times, however, all those acronyms can start to add up, which is why we are taking some time to explain what it means, for example, that your MSP is going to provide DR services to protect your organization and end users. (That’s a Managed Service Provider providing Disaster Recovery services, for those of you keeping track at home.)
Let’s take a closer look at some of the acronyms we use on a near-daily basis, what they mean, and what it means for your organization.
SIEM (pronounced “sim”): Security Incident and Event Management
This is a software solution that can collect data from across the IT environment within your organization, helping pick up on trends and detect threats. Thrive’s managed SIEMaaS (that’s Security Incident and Event Management as a Service) is a modern solution designed to monitor IT infrastructure and SaaS based applications without complicated hardware or a large, specialized security team required.
SOC (pronounced “sock”): Security Operations Center
At a Security Operations Center, security professionals monitor network activity, tracking potential threats from around the globe. SIEM and SOC complement one another – the SOC team of analysts tracks any alerts coming from the SIEM, and take further action to remediate issues when required. Our 24×7 SOCs monitor infrastructure and threats for businesses.
vCISO (pronounced “vee see-so”): Virtual Chief Information Security Officer
For organizations not looking to hire a full-time CISO, a vCISO can fill operational and business gaps. This emerging role can be a good fit for start-ups and small- to medium-sized organizations. Our vCISO experts assist with developing and implementing a customized Information Security Program, ensuring you meet all regulatory, audit, and compliance regulations.
EDR: Endpoint Detection and Response
Endpoint Detection and Response brings together real-time monitoring and the collection of tangible endpoint data, with the ability to respond against threats and stop malicious activity. Traditional antivirus and malware technologies don’t go far enough, and don’t offer high levels of protection against suspicious activity. Thrive’s Endpoint Detection and Response offers the necessary round the clock real-time threat detection organizations need.
SD-WAN: Software-Defined Wide-Area Network
SD-WAN overlays on an existing network, helping provide better application engagement and simplifying operations at the WAN edge. Software-driven WAN provides better connectivity among varying network environments. Thrive offers Managed Secure SD-WAN Service capable of enabling application-based path selection from remote branch offices to the applications that drive your business, whether they reside in your data center or in the cloud.
DRaaS: Disaster Recovery as a Service
Should a natural or man-made disaster occur, Disaster Recovery as a Service (DRaaS) utilizes the Cloud to protect important applications and data. We partner with IT teams to create a comprehensive business continuity plan, with a DRaaS plan activated if needed. DRaaS ensures businesses limit downtime and return to regular business operations as soon as possible.
Now that you are up to date on your acronyms and our solutions, we invite you to contact our experienced team to assist with your NextGen managed service needs!
How Is a Business Continuity Plan Different than a Disaster Recovery Plan?When important systems become unavailable due to infrastructure failure, human error, or a security breach, it can lead to unaffordable business interruption and downtime. The best way to ensure your organization is prepared for any scenario is to have business continuity and disaster recovery plans on hand.
While these terms are often used interchangeably, there are notable differences between the two, which is why it’s critical to have both plans in place to help mitigate the impact to business operations.
A business continuity plan refers to how a business continues to operate when key systems are down or an outage occurs. A disaster recovery plan, on the other hand, refers to how specific platforms, data, and applications are restored following a cyber attack, disaster, or other failure. At Thrive, we understand the needs of businesses and stress the importance of having actionable business continuity and disaster recovery plans in place.
Business Continuity Plan: A Must-Have for Every Organization
A March 2020 study from Mercer concluded that 51% of businesses did not have a business continuity plan in place to combat a global emergency, such as Covid-19. For many organizations, this lack of planning meant loss of revenue, unexpected expenditures to support a remote workforce, or loss of market share as better prepared competitors took advantage of their ability to adapt. Business continuity plans keep a business running effectively, even when faced with an unexpected disaster, and they’re a must-have for organizations across nearly every industry.
The goal of a business continuity plan is to know what processes can be kept in place when a disaster occurs, and which ones must be adapted. At Thrive, we stress two important terms when helping our customers to hone and craft a business continuity plan:
- Recovery Timeline Objective (RTO) – The time it takes systems to fully recover
- Recovery Point Objective (RPO) – The amount of data loss acceptable to a business
It must be plainly understood across departments within an organization where data is stored, what applications are in use, who stores the data, and who has access to it.
With a proper plan in place, it’s easier for everyone to know how to react should disaster strike. A plan allows you to prioritize what’s important – for instance, not being able to access email isn’t as critical as losing customer data that allows you to finalize an order or payment.
And, as our CIO Michael Gray outlined in a previous blog post, it’s worth the time to perform a tabletop exercise, which can help organizations identify and prepare for various scenarios, when it comes to business continuity planning.
Putting a Disaster Recovery Plan in Place
A disaster recovery plan refers to the specific part of the business continuity plan to be followed during and after data loss. It’s most important to get systems back up and running following a data loss event, in an effort to minimize downtime and business disruption.
As Thrive works with organizations, we tend to find there are on-premises and Cloud systems, along with SaaS applications, carrying various backup platforms. Our team can assist in testing these backup systems to see if they match what is laid out in the business continuity plan.
We understand that designing and executing a disaster recovery plan can be limited by budget, technology, resources, and staff on site, which is why our Disaster Recovery as a Service (DRaaS) is a strong solution for many businesses. We will partner with your IT team to create a comprehensive plan allowing for backup of data and the IT infrastructure in a third-party Cloud environment. This makes it easier to access IT infrastructure following a disaster.
At Thrive, we will partner with you to create a comprehensive business continuity plan that extends to include disaster recovery planning. Get in touch with our experienced team to explore Thrive’s targeted solutions for your organization.
Mastering Microsoft Teams8 Tips and Tricks to Improve Your Teams Experience and Boost Productivity
This month we’re looking at Microsoft Teams — a collaboration application that helps your team communicate and stay organized. Teams is actually a suite of bundled collaboration services available on your desktop, mobile device, or browser.
Many users assume that Teams only offers voice and calling capabilities. After all, with most of us working remotely, the phrase “I’ll send a Teams Meeting invitation shortly” is now a part of our daily vocabulary.
However, that’s just one of Teams’ many features. In this article, I’ll show you eight tips and tricks every Teams user should know.
1 – Customize Your Experience
The Microsoft Teams desktop application interface is highly customizable. Simply drag and drop the nodes into your preferred order or remove a node entirely by right-clicking and selecting ‘Unpin.’
2 – App Integration
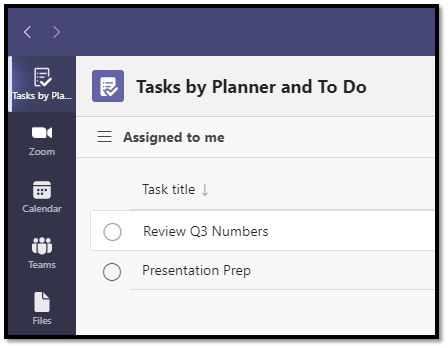
Teams provides an App Gallery that lists Microsoft and third-party apps. If you’re using Microsoft Planner for task management or Zoom for video, you can prevent application switching by adding them to the Teams user interface.
If you’re not yet using Microsoft Planner, click here to review our Microsoft Planner blog.
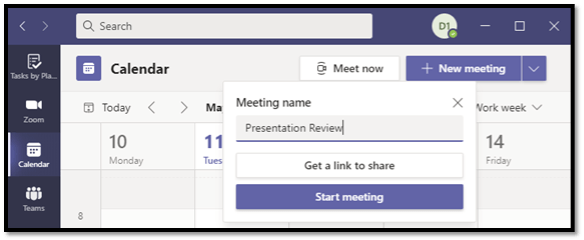
3 – Meet Now
Have you ever needed to get your team on a call quickly? Using emails, phone calls, and text messages to notify everyone is slow and painstaking. Teams has a fix for that! Click the Calendar node, and in the top right-hand corner, you’ll find Meet Now. Click the button, give the meeting a name, then click Start Meeting.
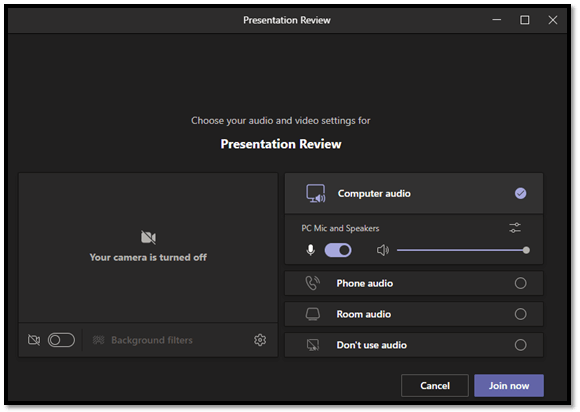
When the standard Teams Meeting screen appears, select the required settings and click Join Now.
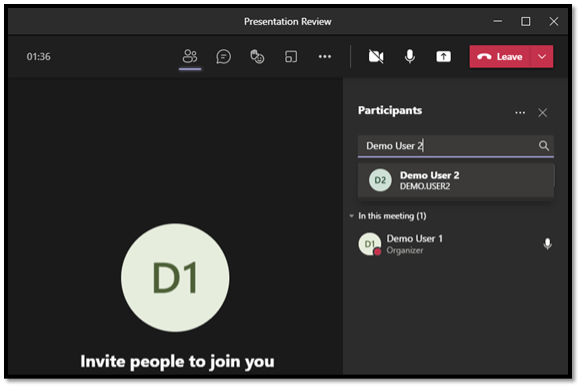
4 – Screen Sharing
Previously, screen sharing was not available to everyone and didn’t always work well. But performance has improved, and now everyone has access to this feature!
When in a Teams Meeting, click the screen sharing button, select the screen or document you want to share, and you’re done! This feature is also available in the mobile app, so you can easily share documents while on a call. Who says you can’t close deals while sitting in the airport lounge or enjoying coffee and cake on a restaurant patio?
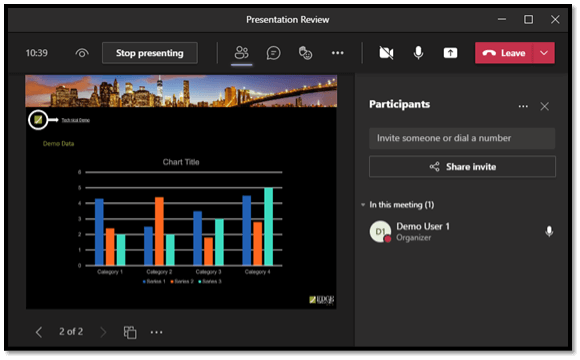
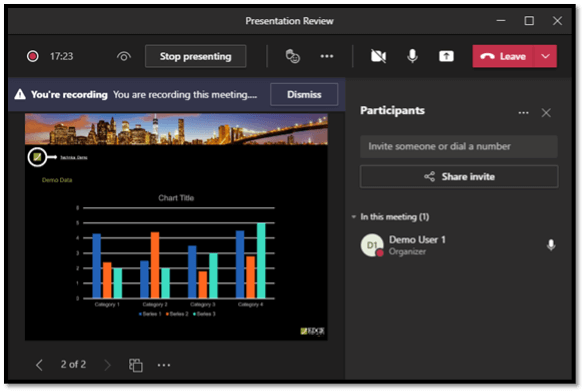
5 – Recording
If you’re presenting via Microsoft Teams and need to record, Microsoft Teams has you covered. Click the menu button (3 dots) at the top of the screen, then click Start Recording. A banner will appear across the screen, alerting everyone that the call is being recorded. We’ll discuss how and where this recording is saved later in this article.
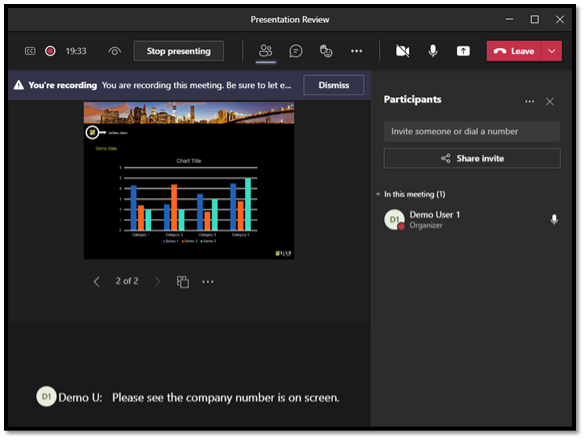
6 – Live Captions
Have you ever lost sleep wondering if Microsoft Teams had a captions feature? Perhaps not, but don’t worry — there’s a captions feature built into the application.
Click the menu button (3 dots) at the tops of the screen, then click ‘Turn on Live Captions’ to see the dialogue printed at the bottom of the screen.
7 – Meeting Notes
Did you know that Microsoft Teams provides a Meeting Notes feature? Click the menu button (3 dots), then click Meeting Notes. This creates a new group in Teams Chat, automatically adding all meeting members and ensuring that everyone has access to the meeting minutes, both during and following the meeting.
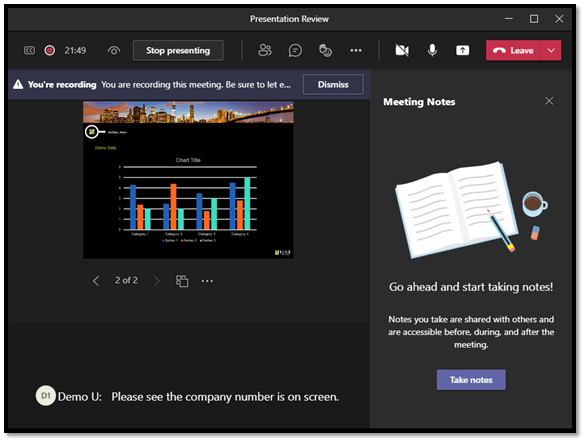
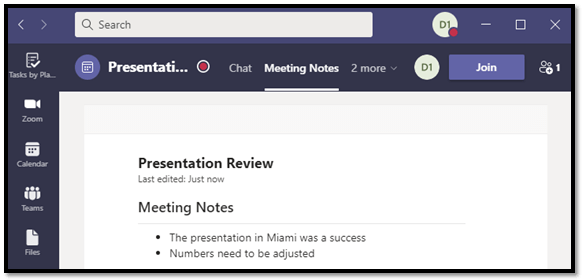
8 – Content Aggregation
Once your meeting has ended, you’ll find the meeting notes and call recording listed in a newly created group under Teams Chat. Teams automatically puts everything in a single, easy to access location.
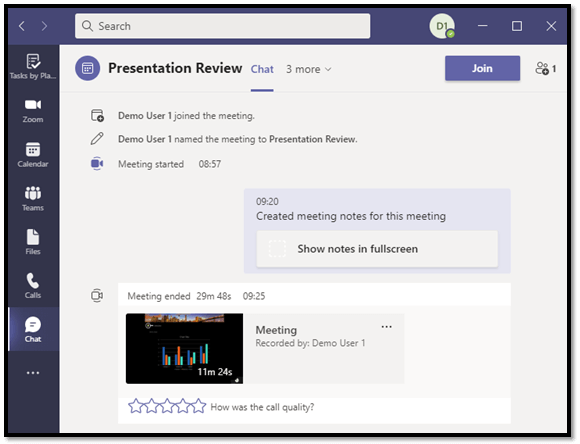
Are You Teams-Ready?
Microsoft continues to integrate new features into Teams, improving and expanding its capabilities. In future posts, we’ll explore some of the more advanced Teams features. In the meantime, using these eight tricks and tips should help improve your productivity and overall Teams experience.
Protecting Patient Information While Working VirtuallyCyber attacks are an unfortunate reality that all organizations must contend with. For those in the healthcare field, it’s of the utmost importance to meet all HIPAA compliance regulations while safeguarding critical protected health information (PHI).
Remote work presents a long list of challenges for doctors, healthcare professionals, and staff, which is why Thrive works to provide an actionable cyber security plan that considers two important components – CybeRTO and CybeRPO. Ensuring all staff can work remotely while mitigating security breach risks is imperative to protecting the long-term success of any healthcare organization.
Are you doing enough to defend your organization from HIPAA violations while providing a remote work setup? CyberRTO and CybeRPO should be important considerations in any cyber security continuity plan, especially in healthcare.
HIPAA Compliance: An Evolving Process
Within the healthcare industry, inherent risks exist that other industries and organizations may not face – so often, end users are the ones who must have a close eye on compliance regulations and policies. It’s important to limit access to only those who need it. PHI should only be seen by members who need it to complete their work, and HIPAA-compliant applications and tools should be used to protect patient privacy.
Encryption is an important part of any work-from-home policy for healthcare organizations. Wireless routers, email, and devices should be configured in a manner to protect valuable patient information. For instance, Microsoft 365 comes with the option of data loss prevention (DLP), which is capable of screening emails for PHI, encrypting any email that may contain personal information.
Disabling of removable media storage should be done as well. If PHI is on a device, USB drives and portable media drives shouldn’t be able to transfer data off the computer’s hard drive.
The Thrive team can help implement a HIPAA-compliant process as technologies and data needs continue to evolve within the organization.
Cyber Attack Preparation: Putting a Plan in Place
CybeRTO and CybeRPO represent security response times and the recovery of data in the event of a breach or cyber attack. Together, they define just how much time and data loss a healthcare organization can afford.
CybeRTO refers to how long it takes to respond to a threat, and could be something as simple as patching a vulnerability before an incident occurs or something as complicated as reacting to a cyber event. It also takes into account how long it will take to recover from an attack that has affected the work environment.
On the other hand, CybeRPO refers to the data that could be lost in a cyber attack, and how much data would be exposed. In the case of the healthcare industry, that could mean the loss of PHI and having to respond to HIPAA compliance issues.
Thrive designs solutions capable of backing up data when you want it backed up – whether that’s in real time as files or servers, or hourly, daily, or weekly. We recommend real-time Cloud backup, giving end users the ability to easily access files they need if a disruption occurs.
As you create your continuity plan, keep in mind the CybeRTO and CybeRPO requirements, especially in this work-from-home era. Contact the Thrive team for more information about protecting your end users (and patients) while working virtually.
Talking Tech: Collaboration and SecurityRecently, Thrive’s CISO, Chip Gibbons, and EVP & GM of Microsoft Collaboration, Ryan Thomas, hosted an informative webinar discussing the important topics of security and collaboration.
Discussion included secure external sharing in Microsoft Office programs, the security and governance controls that should be in place in every organization, and how platforms continue to evolve and why it’s important to stay up to date with the latest features and changes.
Below, check out some highlights from this enlightening conversation.
On what’s driving transformation in collaboration:
Ryan: People are looking for efficiency. They have vendors, consultants, and external projects to complete. Sending outdated, antiquated documents back and forth over email and trying to piece the changes back together is difficult. As someone who has been diving into Microsoft Teams for years now, when I have to go back to sending items over email it’s tough.
Chip: Absolutely. I’m sure I’m not the only person who has dealt with this, but starting an email thread can sometimes morph into something completely else, or something that doesn’t have to deal with the original email. This is where Teams and collaboration can shine. With Teams, there’s built-in security that’s already there, because you know who you are collaborating with and doing so in real-time.
Ryan: Right. Email is a tough place to store data and access it. It’s fine to send a message to someone, but when it comes to working on a document or sending one, it becomes difficult to use email. We hear from clients that their vendors and their customers are asking for [collaboration tools], too. It’s not just for internal use, but it’s for external use, too.
Why data classification and protecting data matters:
Ryan: One of the things we always highly recommend is a governance plan. Governance is half about security, and half about guidance. Part of governance is about architecture, and understanding the type of data that will be shared externally, so policies can be set.
Chip: Policies and procedures are important. You can’t secure anything before knowing what you’re trying to secure and how to secure it. We do come across clients who may not have an information security plan. It doesn’t have to be perfect the very first time, but there has to be a plan on paper to start with. If there is no written information security policy, employees don’t know what they can and can’t share. Should they be on social media? Should they be able to plug a USB port into a work computer and take data home? It depends on the security policy. If there’s nothing there, then we don’t know what should and shouldn’t be protected.
On platform capabilities and what they can offer:
Ryan: I think a lot of people don’t know what the platform capabilities are and how these platforms can protect them. Simply going through settings can give you an idea but won’t give you the full picture. The first thing we always do is we start to educate ourselves on what a platform can offer, to better understand what data can and should be locked down. Education is important.
Chip: Education is important, yes. It can’t just stop, either. The platform will keep on changing.
Ryan: Exactly. Customers ask us to help them keep up with everything a platform has to offer. From a security and a sharing perspective, that is a risk, right? When things change in the platform, they need to be identified quickly. Capabilities continue to be added, and it can present more challenges along the way. We’re here to help. When a platform is set up with proper policies, it can be secured where it would pass a stress test of a security audit.
Chip: We don’t ever put something into place and leave it and walk away. It’s important to monitor, maintain, and adjust as things change.
How to avoid “shadow IT”:
Chip: There’s a whole concept of “shadow IT”, where employees are trying to do their jobs, and they want to do their job right, and they need to get data to someone. So, they might, for example, open up a personal Dropbox account and transfer data that way. The last thing anyone wants is data leaving the organization and not knowing where it’s going. Having policies and procedures in place goes a long way to eliminating shadow IT and data leaving the organization. It’s not malicious intent. It’s just an employee trying to do their job. They need to have the right tools so they can do their job effectively and not put an organization at risk.
Ryan: We can set the needs up in a way that they are supported. Generally, end users will find a way. We call it shadow IT, but essentially, they’re working around systems. So, give them a viable solution to do what they need but make it viable and secure. You’re better off that way than you are letting them try to figure it out on their own and seeing data or important information slip through the cracks.
Be sure to check out the full conversation below, and contact the Thrive team for all of your digital transformation and security needs. We are here to ensure organizations have everything they need to work successfully, whether in the office or remotely.
Microsoft OneDrive vs. SharePoint: Which Platform Do I Need?As remote work continues to play a pivotal role in our lives, it’s more important than ever for employees to have access to what they need when they need it most. Thrive helps clients manage an ever-evolving remote work setup, one that may require access to a file management platform.
Microsoft offers both OneDrive and SharePoint in its suite of services, and while these file management platforms have plenty in common, there are some key differences between the two, with distinguishing features that help drive business efficiencies.
Ensure a proper approach to file sharing, collaboration, and document management, with Thrive’s customized recommendations of how to deliver a complete file management solution.
Are OneDrive and SharePoint One and the Same?
OneDrive and SharePoint assist in file management, with any documents and data safely stored in the Cloud, giving users the ability to view documents, make changes, and see the version history of the document itself.
Made for those on the go, they both offer mobile-friendly features and syncing of files across devices. With OneDrive and SharePoint in Microsoft Office 365, files are stored in the Cloud, and it’s easy to sync either OneDrive or SharePoint files to a computer.
Think of OneDrive as the best choice for individual employees. Employees can create a document privately, work on a first draft, and manage projects yet to draw in the larger team. SharePoint allows employees to take that next step, uploading a personal draft from OneDrive so the larger team has access to the file. Administrators can set up permissions, too, giving access only to authorized team members. Now, multiple employees can comment, edit, and make changes to the document within the SharePoint system, so everyone is kept up to date with the latest progress.
Working solo? OneDrive is the way to go. Bringing a larger team in for the conversation? SharePoint access will drive productivity.
What are the Key Differences Between OneDrive and SharePoint?
With OneDrive, users have a personal account which keeps them in full control of files they create and upload. Only when a larger team needs access to the file will it be shared from OneDrive, which is a Cloud-based offering.
SharePoint is designed as a work process management platform, and while through Office 365 it offers Cloud capabilities, it can become an on-premises solution, as well. SharePoint allows administrators to create team-specific sites, going beyond the basic personalized interface of OneDrive. These team-specific sites may include easy-to-use dashboards, calendars, project updates, and task lists, ensuring seamless collaboration among all users.
Another major SharePoint advantage is the ability to customize internal team sites and outgoing communications. For example, admins can update an employee portal using the SharePoint interface and team-shared documents. Thanks to SharePoint’s CMS application, it’s easy to update a customer-facing website, too, with the ability to publish documents directly to the site.
Organizations have choices to make when it comes to OneDrive and SharePoint, but the reality is that using a combination of both will benefit businesses. To discover how to best utilize OneDrive and SharePoint and better understand Cloud and on-premises options, get in touch with the experienced team at Thrive today.
