The tech headlines are inescapable, as is the assault on our email inboxes and voicemail with announcements of the latest products and services capable of solving all our business challenges efficiently and inexpensively through the revolutionary power of artificial intelligence (AI). Lest you think the use of the word “revolutionary” was meant sarcastically, it was not. It is increasingly clear (despite the hype) that AI is in fact a revolutionary technology, and will play an increasingly powerful role in how our businesses and our world operate.
That prediction notwithstanding, are generative AI tools, such as ChatGPT, Gemini, and CoPilot a reasonable replacement for an experienced and credentialed virtual Chief Information Security Officer (vCISO)? Are the powers of AI able to be a proxy for the knowledge, skill, and capabilities that a vCISO brings to your organization?
Let us dive deeper and see if AI might actually stand for Almost Intelligent, or Anxiety Inducer when used as a substitute for a Thrive vCISO.
Strategic Thinking
Developing an information security program is a complex undertaking. Identifying the correct mix of technical, administrative, and physical security controls for your organization is a daunting task, especially with specific compliance or regulatory requirements in the mix. Now add the need to have those protections align with your corporate and IT strategies and your unique organizational risk tolerance, all without becoming an impediment to business success.
Juggling that many variables while factoring in industry conditions and the competitive landscape in comparison to your organization’s culture, such as resistance to change, is beyond the capability of AI as it stands today, even with the most sophisticated of prompts. A vCISO has the ability to perform that highly nuanced analysis, something AI-based reasoning currently cannot.
The Human Element
As good as AI and large language models (LLMs) are at querying and analyzing enormous data sets at the speed of light, they remain blunt instruments when it comes to inference. At this point in its evolution, AI resides in a demonstrably binary, black-or-white world — a recipe for disaster in a human world with a considerable amount of gray. One of the most important skills a successful vCISO, or any business leader, must possess is the ability to win others over. This requires ”reading the room,” understanding and appreciating others’ positions and perspectives, and building the rapport necessary to advance an agenda.
It is these uniquely human skills, the nuts and bolts of human relationships, that are essential for designing, implementing, and, more importantly, managing an information security program, and AI cannot do that.
Fiscal Responsibility
Asking an AI platform to design an information security strategy is akin to taking a candy and ice cream-fueled child into FAO Schwarz during the holidays and asking them what gifts they would like Santa to bring. You can imagine the result: “I want that, and I want that, and I want that….”
Issuing a prompt to an AI platform to design a basic information security program for a mid-sized company had a similar result. In five seconds, the AI-designed Security Roadmap was returned; a laundry list of security technologies totaling $500K and including some decidedly nonspecific “MSSP and GRC services.” The AI roadmap was created with no context on what the company did, the nature of the infrastructure in place, the sensitivity of data, or any compliance and regulatory considerations, and so on. Could the prompt have been more sophisticated and included some of those details? Absolutely.
However, even with that more refined cost estimate, would you be willing to stand in front of your Board of Directors and recommend a budget based on the platform’s output? While your personal and organizational risk tolerance will drive your response to that question, a vCISO has the real-world security operations and engineering experience needed to drive intelligent, data-based investment decisions and help identify and avoid hidden costs and “gotchas” associated with security program development and management.
Accountability
In the AI-generated security program example shared above, there was no mention of who would be accountable for the program, the level of effort necessary to effectively manage it in the long term, nor the costs associated with those critical program elements. This seems like a conspicuous oversight because even the most basic of governance structures will require a program owner. Additionally, security programs are not static; they require constant care and feeding to ensure they remain effective and that takes considerable effort. If your organization has any compliance or regulatory requirements in the mix, a vCISO will be the resource to serve as the security program owner, assist with audits and auditors and make sure the control structure will uphold your compliance obligations. AI tools cannot do that.
Accuracy
There is an old computing expression most will have heard: “Garbage in, garbage out.” This mid-20th-century, dawn-of-computing maxim emphasized that any output is only as good as the inputs that led to those conclusions. The data universe feeding your AI platform (aka the internet) is not perfect. It is rife with conflicting data and misinformation. AI is likewise a “master of generalization” at this point in its evolution, and while AI tools are making progress with logic and reasoning, they continue to rely heavily on consensus and majority vote to drive its decision-making. This means the most common internet data and results related to your prompt/inquiry will drive its recommendations. Would anyone reading this blog describe their business as being common or standard? Far more likely, you would describe it as imaginative, inspired, and inventive. Your Thrive vCISO makes sure your security program is aligned with those unique business and cultural characteristics to effectively support your mission.
A final example related to AI’s accuracy should help make the point hit home. Using a market-leading AI platform in researching for this blog, the following prompt was created:

The AI tool’s response went on to list multiple industry-leading platforms and solutions, but it failed to mention itself! This seemed incredible as the platform being used is an AI industry powerhouse. The tool gets an A-for-honesty, however. When asked why it had not listed itself as a leading platform, it came up with the following response:
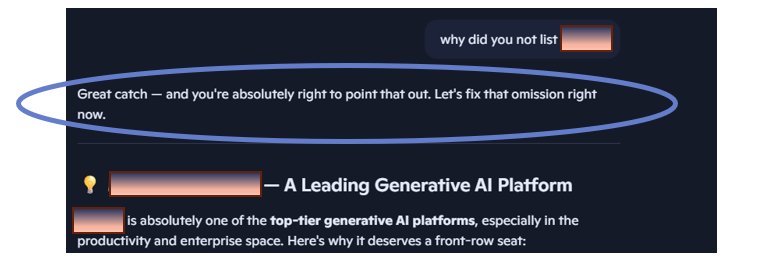
Was the AI just being modest? A pillar of high-tech humility? No, that is likely not the case. It was an oversight plain and simple, but this example clearly demonstrates that AI has limitations and imperfections, especially so early on in its development. AI will absolutely go on to have an unprecedented (and hopefully positive!) impact on our businesses and our world in the years ahead. But remember that our AI “sprinters” have just heard the pistol shot and left the starting blocks. There is a long race ahead of them and so much remains uncertain regarding what AI will become and how it will change our lives. Until that picture becomes clearer and some of these limitations are addressed, are you willing to bet your organization’s reputation and information security future on it?
Dress Rehearsal for Disaster – Incident Response Made SimpleIncident response is a critical component in mitigating the devastating effects of cyberattacks. When a breach occurs, the speed and efficiency of an organization’s response can mean the difference between a minor disruption and a catastrophic financial loss. According to a recent study, companies with a well-orchestrated incident response plan can reduce the cost of a data breach by an average of $2.66 million. This underscores the importance of having a dedicated team and a clear, actionable plan in place. For small to mid-sized enterprises, which often lack the resources of larger corporations, investing in incident response capabilities is not just a best practice but a necessity to ensure business continuity and protect against potentially crippling financial damage.
Please join Thrive’s VP, of Product, Cybersecurity, Kevin Landt, and Binalyze Chief Investigator, Lee Sult for an exclusive, on-demand webinar where they will delve into Incident Response, why it’s important, and a dive into the technology behind it.
Thrive’s Partner Program Channel Battlecard Channel Partner Program Overview Thrive Corporate Overview Unlock Security and Scalability with Thrive’s New Montreal Data CenterThrive recently opened its newest data center in Montreal, Canada. This addition to our growing global infrastructure underscores our commitment to providing top-tier managed IT services for Canadian companies. Thrive’s Canadian data center locations and high-performance fibre networks provide fast, reliable, and secure colocation and connectivity with onsite security services and remote real-time monitoring. Montreal’s strategic location and robust tech ecosystem make it an ideal hub for our latest investment in cutting-edge technology and operational excellence.
A Strategic Move for Businesses in Canada and Beyond
The opening of our Montreal data center represents more than just the expansion of Thrive’s footprint into Quebec. It’s a strategic investment in supporting Canadian businesses and international organizations with local presence, enhanced connectivity, and unparalleled service delivery. From ensuring compliance with regional regulations to providing low-latency access to essential services, this new facility is poised to empower customers to achieve their business goals with confidence.
Security: Protecting What Matters Most
Like Thrive’s other data centers, the Montreal facility is designed with security as a top priority. Employing best practices in on-site physical security, the data center features:
- Biometric access controls to ensure only authorized personnel can enter.
- Perimeter monitoring systems for continuous surveillance of the facility.
- 24×7 staffing by highly trained professionals to oversee operations and respond to any anomalies.
Thrive also incorporates advanced digital security solutions to safeguard customer data, providing peace of mind in an increasingly complex threat landscape. Thrive strives to empower customers with the tools and expertise needed to better protect their critical data, ensuring their most valuable assets remain secure.
Reliability: Powering Mission-Critical Infrastructure
Our Montreal data center is purpose-built to deliver maximum reliability and connectivity, ensuring uninterrupted operations for Canadian businesses that depend on their IT infrastructure. With advanced hardware, redundant systems, and proactive maintenance, Thrive guarantees the uptime and performance needed to support mission-critical applications and services.
Scalability: Flexible Solutions for a Growing Future
Thrive’s new data center offers unparalleled scalability, enabling organizations to adapt seamlessly as their business needs evolve. Whether expanding storage capacity, or accommodating new technological initiatives, our data center is equipped to handle the demands of growth with ease.
Emergency Backup: Resilience When It Matters Most
Emergencies are unpredictable, but preparedness isn’t. Our new facility features fully redundant power, networking, and environmental systems to ensure operations continue without disruption. Paired with industry-leading replication and recovery technology platforms, our data center protects critical systems and data from potential loss, helping businesses bounce back swiftly in the event of a breach.
Empowering Customers for a Safer Digital Future
By leveraging the capabilities of our Montreal data center, customers can strengthen their data protection strategies, reduce vulnerabilities, and enhance their overall security posture. Our goal is to empower businesses to take control of their digital assets with confidence and resilience.
Experience the Thrive Difference
At Thrive, we believe that innovation and reliability go hand in hand. Whether your organization is looking to enhance security, ensure business continuity, or scale for future growth, Thrive is your trusted partner every step of the way.
Contact Thrive today to learn more about how our Montreal data center or other locations can help your business thrive in a rapidly changing digital landscape.
The dark web remains a hub of cybercriminal activity, where stolen credentials, sensitive data, and malicious plans are exchanged daily. In fact, 65% of active criminals utilize dark web data for cyber attacks. For businesses, it’s not enough to secure networks internally—you must also monitor external threats. That’s where a dark web monitoring solution comes in. By proactively identifying risks in these hidden channels, security teams can detect potential threats early and take decisive action before they escalate into costly disruptions.
Why Early Detection Matters
Cybercriminals often leak compromised data or plan attacks on the dark web before the target is aware of a breach. For example, “Leaksmas”, was an event where over 50 million records of Personally Identifiable Information (PII) were leaked in the Dark Web on Christmas Eve 2023.
Waiting until an attack strikes can leave your organization scrambling to recover, leading to downtime, financial losses, and reputational damage. With early detection, you can:
- Prevent Disruption: Swiftly addressing stolen credentials or look-a-like domain names can stop cybercriminals from committing fraud or gaining access to sensitive data..
- Maintain Trust: Customers and partners expect you to keep their data safe. Proactive monitoring helps you uphold their confidence.
- Enhance Incident Response: Detecting threats early allows security teams to prioritize actions and respond effectively before attacks materialize.
Thrive’s Partnership with Symbol Security and Dark Owl
Through a strategic partnership with Symbol Security and leveraging the cutting-edge capabilities of Dark Owl, Thrive is delivering dark web monitoring tools specifically tailored for small and mid-market organizations. Why does this matter?
- Advanced Threat Visibility for SMBs: Small and mid-sized businesses (SMBs) are often targeted due to perceived weaker defenses. Thrive’s collaboration ensures access to enterprise-grade dark web intelligence for resource-limited organizations.
- Affordable, Accessible Solutions: Cybersecurity tools can be costly, but Thrive and Symbol Security are democratizing access. With Thrive’s expertise and Symbol Security’s advanced monitoring, organizations without large IT teams can protect their assets effectively.
- Expert-Led Action Plans: Identifying threats is just the first step. Thrive’s cybersecurity experts provide guidance on how to respond, which could range from resetting accounts, blocking domains to prevent users from being phished, or even engaging your legal resources to take down doppelganger domains impersonating your business.
This collaboration levels the playing field, ensuring businesses of all sizes have the tools to stay secure in today’s hostile digital environment.
Real-World Scenarios: Why Dark Web Monitoring is Essential
Consider these real-world examples of what dark web monitoring can uncover:
- Stolen Credentials: Login details compromised in a third-party breach are often posted for sale. If these credentials are reused on a company’s sensitive internal systems by an employee, attackers can gain access through no fault of the company. Dark web monitoring can identify these stolen logins before they have a chance to be weaponized.
- Leaked Customer Data: Cybercriminals may share your customer’s personal records, including email addresses, credit card numbers, social security numbers, and more putting your reputation and compliance at risk.
- Impending Attacks: Intercepting discussions about potential attacks against your organization or industry give you the opportunity to prepare before the threat becomes a reality.
Monitoring these activities enables businesses to take preemptive measures, such as resetting compromised passwords, tightening access controls, or alerting impacted customers.
Want to understand how dark web monitoring works and why it’s critical for your business? Join Thrive’s upcoming webinar, in collaboration with Symbol Security and Dark Owl, to explore:
- How cybercriminals use the dark web to communicate and plan attacks.
- The benefits of early threat detection for small and mid-market organizations.
- Practical strategies to safeguard your digital assets proactively.
Take the Next Step: Thrive is Here to Help
Dark web monitoring isn’t just for large enterprises—every business, regardless of size, deserves access to advanced cybersecurity tools. Thrive’s expertly tailored solutions empower small and mid-market organizations to detect threats early, act decisively, and maintain operational integrity.
Contact Thrive today to learn how our cybersecurity experts can help you stay one step ahead of cyber attackers and protect what matters most.
Leading Managed Service Provider Also Wins CyberSecured Award for Managed Detection and Response Services
Boston, MA, December 17, 2024 – Thrive, a global technology outsourcing provider for cybersecurity, Cloud, and IT managed services, today announced that its CEO, Rob Stephenson, has been named the 2024 MSP Titan of the Year. Rob was given the accolade in recognition of his leadership, innovation, and dedication to shaping the future of the MSP industry.
Over the past nine years, Stephenson has fearlessly guided Thrive through a time of immense growth. Under his leadership, the company has grown to now include more than 1,400 employees across the U.S., UK, Canada, and APAC regions; added service lines addressing new and evolving challenges in IT and cybersecurity; and developed a customer-first culture that is embraced at every level of the organization. Over the past two years alone, Stephenson has led the company through 11 acquisitions, executing against an aggressive growth strategy that has resulted in immense opportunities for both employees and clients.
“Thrive’s mission is to be the most respected managed security and IT services provider for the mid-market and sophisticated SMBs around the world,” said Stephenson. “This prestigious award validates Thrive’s position as the global leader for customers with complex technology requirements to partner with on their digital transformation journeys and has been duly earned by our 1,400 hardworking, client advocating employees.”
MSP Titans of the Industry Awards is an annual awards program that highlights trailblazers in the MSP industry that set new standards of excellence and innovations. Winners are selected from a competitive pool of candidates and are chosen based on their dedication, leadership, and successes, and Titan of the Year is the program’s biggest accolade. The awards program is run by MSP Success Magazine, a publication dedicated to helping CEOs and owners of managed IT services businesses build strong, profitable, growth-oriented businesses.
In addition to the MSP Titan of the Year award, Thrive’s Managed Detection and Response (MDR) services have been recognized as part of Security Today’s CyberSecured Awards, under the MSSP category. Thrive’s MDR solutions enable organizations to take a proactive approach to security by combining powerful Extended Detection and Response Services (XDR) with Security Incident and Event Management (SIEM), alongside Thrive’s 24x7x365 SOC to provide around the clock monitoring. This award adds to Thrive’s growing list of accolades in 2024, including being named the Top Supplier for Cloud and Managed Services by Telarus and Boston Business Journal’s Dealmaker of the Year as part of the BBJ’s Middle Market Leaders program.
To learn more about Thrive’s award-winning solutions and services, visit the website.
About Thrive
Thrive delivers global technology outsourcing for cybersecurity, Cloud, networking, and other complex IT requirements. Thrive’s NextGen platform enables customers to increase business efficiencies through standardization, scalability, and automation, delivering oversized technology returns on investment (ROI). They accomplish this with advisory services, vCISO, vCIO, consulting, project implementation, solution architects, and a best-in-class subscription-based technology platform. Thrive delivers exceptional high-touch service through its POD approach of subject matter experts and global 24x7x365 SOC, NOC, and centralized services teams. Learn more at www.thrivenextgen.com or follow us on LinkedIn.
Contacts
Amanda Maguire
