For mid-size British businesses, the cyber threat landscape has become a minefield in recent years. We have already reported on state-sponsored threats to private companies and public services. This year’s massive cyber attack on London National Health Service (NHS) hospitals by a Russian ransomware group has caused hundreds of operations to be cancelled, the need for emergency blood supplies to be found, and IT systems suspended, leading to the manual processing of patients because of a hack into the NHS supply chain.
While criminal hackers and financially motivated cybercrime groups have long plagued companies from known sources, a new and even more alarming threat has emerged: state-sponsored hacking operations backed by the Chinese government.
Recent developments have shed light on the sophisticated and persistent efforts by Chinese hackers to compromise systems, steal data, and even interfere with democratic processes across the UK and its allies. No business is immune, no matter its size or sector, so in this article, we’ll explain how you can protect your business from this imminent threat.
Investigated by the NCSC
In March 2024, the UK government took the bold step of publicly calling out China for two major cyber campaigns targeting British democratic institutions and Members of Parliament. As revealed by the National Cyber Security Centre (NCSC), a Chinese state-affiliated group gained widespread access to the systems of the Electoral Commission between 2021-2022, potentially exposing data on a whopping 40 million Britons on the electoral register. In a separate campaign in 2021, the same Chinese hacking group carried out reconnaissance against British members of parliament, particularly those outspokenly critical of Chinese government policies.
These were by no means isolated cases but rather represent, according to the Foreign Office, a “part of a large-scale espionage campaign” by China. These revelations were supported by allies like the United States, who announced criminal charges against Chinese hackers and partners across Europe and the Indo-Pacific, condemning Beijing’s malicious cyber activity.
Newly discovered malware
One particularly sly tactic Chinese threat groups use is exploiting the trusted relationships and supply chains of the targeted organisations. Crowdstrike’s Global Threat Report assessed that Chinese threat actors known as “Jackpot Panda” and “Cascade Panda” “consistently exploited trusted relationships through supply chain compromises and actor-on-the-side or actor-in-the-middle attacks.” These groups can quickly gain clandestine access and deploy malware inside a victim’s network by hijacking software updates or compromising close third-party vendors.
For example, Jackpot Panda was found to have “trojanised” installers for legitimate Chinese software to deploy their malware. Similarly, Cascade Panda intercepted update traffic from commonly used software utilities to install its WinDealer remote access tool on systems belonging to Chinese-speaking targets. Even little-known groups potentially linked to Beijing pulled off supply chain attacks, such as compromising an Indian (among other) critical infrastructures with a cybersecurity vendor, I-Soon, distributing malware via its software updates across multiple sectors, affecting users across the globe.
Three ways your company could find itself in the firing line
While the Chinese government’s motivations may usually be centred on gathering intelligence (mainly for monitoring dissidents), UK companies could easily get caught in the crosshairs. Firstly, they represent a treasure trove of intellectual property, research, customer data, and other sensitive information crucial to Beijing’s strategic interests and economic leverage. The Chinese military policy of “civil-military fusion” blurs any remaining lines between the private sector and state assets.
Secondly, British firms are deeply embedded in the same supply chains, software ecosystems, and trusted vendor relationships, actively being exploited as vectors for initial access by Chinese hackers. After all, a company’s cybersecurity posture is only as strong as its weakest link in such an interconnected business environment. Threat actors have demonstrated a keen ability to methodically map out these interdependencies and pounce when the opportunity presents itself.
Finally, UK businesses like yours should be prepared for the potential collateral damage and interruptions caused by Chinese cyber operations, even when not directly targeted against them. The data thieves’ campaigns highlighted above directly interfered with the IT systems of government bodies responsible for administering elections and democratic processes in Britain. So, any company’s operations could halt if its technologies or data flow intersects with compromised systems.
How can you shield your business?
In the face of this daunting threat from a competent nation-state adversary, mid-size UK businesses must boost their cyber defences and resilience. A proactive, comprehensive cybersecurity strategy centred around advanced threat detection capabilities is essential. Implementing strong access controls such as multiple-factor authentication, tight identity management, encryption, and vetting the cybersecurity practices of third-party vendors can all reduce risk exposure.
However, even the most robust technical controls have limits against skilled, determined, and infinitely meticulous nation-state attackers like China’s hacker groups. Businesses require professional cybersecurity monitoring services, threat-hunting experts, and incident response capabilities to identify and neutralise intrusion attempts quickly. For this reason, continuous security awareness training to educate employees on the latest tactics, like supply chain compromises, is also critical.
Take protective steps now
As the UK government has demonstrated with its recent actions, exposing and holding malicious Chinese cyber criminals accountable is a priority for preserving our national security and democratic values. Businesses must follow suit and implement comprehensive defences against this looming threat. Unfortunately, failing to do so risks surrendering your organisation’s most valuable data, suffering crippling interruptions, or unwittingly aiding and abetting Beijing’s authoritarian projects. Now is the time to get ahead of those jeopardising UK companies – before a rocky cyber stance becomes a devastating crisis for your company.
Don’t hesitate to contact Thrive today to learn more about nation-state threat detection and mitigation strategies tailored to mid-market UK businesses. Protecting your organisation from state-backed cyber campaigns demands the vigilance and expertise that our experienced team can provide you with every step of the way.
How Should CISOs Navigate the SEC Cybersecurity and Disclosure Rules?Michael Gray, CTO, Thrive: While the Securities and Exchange Commission’s (SEC) Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure rules went into effect toward the end of 2023, many organizations still have questions when it comes to filings and disclosures. Under these rules, organizations have to disclose significant cybersecurity incidents and provide annual updates on their cybersecurity posture. Being able to accurately share cybersecurity updates, sometimes within short time frames, requires teams to have a deep understanding of 8-K and 10-K filings, and to implement new processes that simplify compliance.
Thrive, A Service Bridge-integrated ServiceNow ProviderBridging The Gap
At Thrive, we’ve been through an amazing journey with ServiceNow Service Bridge, an extremely powerful feature that’s part of the Thrive Platform. Thrive is one of the few Service Bridge-integrated providers, providing your organization with even greater access to the Thrive Platform and its NextGen capabilities. Currently, the Thrive Platform gives clients better access to service and more accurate environment insights, while also transforming how IT is consumed through self-service.
What is Service Bridge?
Service Bridge is an application that allows businesses to connect two (or more) distinct ServiceNow instances to seamlessly collaborate and process requests while still working within your organization’s instance of ServiceNow. As a business grows, and recognizes the need to scale their operations and outsource security or other IT functions, Service Bridge allows its ServiceNow instance and another provider’s instance to be directly connected. This allows the organization’s designated ServiceNow administrators to build assignment groups that reference the external instance and more important fulfiller groups from a third party, if needed.
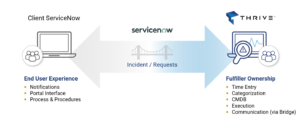
Moving forward, if an incident is opened in an organization’s service portal, the record immediately replicates to the provider instance. As the provider’s resources update the incident, all the notes are sent back to the consumer instance in near real-time. Everything is seamless to the end user. The solution builds a team-like partnership without the need to change end user interactions.
Investing in ServiceNow can be costly to organizations – both in time and resources. With Service Bridge, organizations can maximize their investment. Many IT providers or IT management software require organizations to change their process in order to work together. Service Bridge dispenses with this requirement and highlights the value of robust software integration.
Service Bridge is licensed on the provider’s instance and is free to consumers. Thrive now offers Service Bridge integrated managed services, enabling your organization to seamlessly integrate with Thrive to reach your business goals and ensure business continuity and optimal customer service. If you are a ServiceNow customer and curious about Service Bridge’s offerings and capabilities, please see the following documentation.
Contact Thrive today to learn more about ServiceNow and Service Bridge.
A Hedge Fund Achieves Compliance and Growth with Thrive’s Tailored Managed IT Solutions Download Now
Monterone Partners LLP, a European equity-focused hedge fund in London, needed more support to manage its internal IT infrastructure and compliance. Over the past nine years, Thrive has been a steady and trusted partner and has reduced the firm’s costs associated with internal IT teams, equipment, and full-time employees needed to manage systems, data centres, hardware and more.
Since 2015, Monterone, a small, London-based firm with only eight employees, has relied on Thrive to outsource its foundational IT infrastructure and security needs. Monterone benefits from Thrive’s comprehensive services, including its fully hosted IT infrastructure, managed zero trust, endpoint security, disaster recovery, and more. Thrive ensures Monterone’s operations remain resilient and compliant with SEC and FCA regulations. By removing the need for internal IT teams and reducing equipment costs, Thrive provides the critical foundation for Monterone’s growth and protection against cyber threats.
Why Thrive Was Chosen
Thrive, formerly known as Edge, stood out during Monterone’s search for a provider with deep expertise in alternative investments and hedge funds. Monterone recognised Thrive’s proven track record of delivering reliable solutions, which was crucial as the firm built its first infrastructure. The focus was on creating a system that was not only future-proof but also met stringent regulatory and resiliency requirements, particularly with the FCA and SEC providing oversight.
What truly sets Thrive apart is its ability to design and implement a solution tailored specifically to Monterone’s needs. Monterone relied heavily on Thrive’s expertise without an internal CTO to manage a smooth and disruption-free transition. This included everything from coordinating with providers to handling licensing and installation.
“Thrive’s expertise in alternative investments and hedge funds was invaluable. They also had experience with more complex firms, so they knew how to build a dependable system that could scale with us as we grew,” said Phillip Chapple, COO of Monterone Partners LLP.
Strategic Deployment of Advanced Security Measures
Monterone faced significant regulatory requirements and, without an internal CTO, needed a rock-solid and well-supported infrastructure, particularly with oversight from the FCA and SEC. The firm wasn’t seeking the latest technology but a reliable solution that could efficiently handle all their needs without complications.
“We were building our first infrastructure at the time and needed something that would last. We were focused on future-proofing, meeting all the regulatory and resiliency requirements, and finding a reliable partner for the long haul. Switching providers is a big deal for a firm our size—it’s disruptive and costly—so we had to get it right from the start,” added Chapple
Thrive handled every aspect of Monterone’s infrastructure setup. They sourced and installed all the necessary hardware, including printers, firewalls, switches, and wiring, and configured the Wi-Fi and internal networks. Additionally, they set up Monterone’s private Cloud infrastructure—a decision influenced by the regulatory landscape at the time, when public Cloud solutions were still met with some hesitation. Thrive also managed the piping and point-to-point connections to the data centres, ensuring a comprehensive and seamless implementation.
Thrive’s Impact
Over the past nine years, Thrive has been instrumental in helping Monterone navigate the increasingly complex world of compliance, especially as regulatory demands have intensified, particularly during events like COVID. Thrive’s proactive approach has consistently impressed Monterone, providing timely advice and solutions without waiting for instructions. Their expertise in regulated industries has allowed Monterone to stay ahead of industry standards with products that evolve alongside the firm’s needs without requiring major overhauls.
Thrive’s support has been particularly vital under the scrutiny of SEC and FCA audits, ensuring Monterone can securely store and easily reconstitute communications compliant, all while maintaining cost efficiency. The firm’s exceptional reliability has been a standout feature, with only one significant downtime incident in nine years—an issue promptly addressed and turned into a learning opportunity. Thrive’s proactive and seamless service has been vital to Monterone’s resilience, especially in trading operations where downtime could be detrimental.
“Thrive has always been proactive. They notice potential issues and start triaging before we realise a problem. They’ve often already switched over to backups or failovers by the time we’re aware of the situation. Their service is critical to us and consistently delivers what we need,” stated Chapple

“What impressed me most was how Thrive designed and implemented exactly what we needed. As a smaller firm, we didn’t have the in-house expertise to nail down every detail ourselves. We needed someone who could guide us without overcomplicating things. Thrive delivered a solution that fit us perfectly, handled all the providers and licensing, and took care of the installation. It was a white-glove service—they took care of everything and ensured it all happened with minimal effort and disruption on our end.” ~ Phillip Chapple, COO of Monterone Partners LLP
About Thrive
Thrive delivers global technology outsourcing for cybersecurity, Cloud, networking, and other complex IT requirements. Thrive’s NextGen platform enables customers to increase business efficiencies through standardization, scalability, and automation, delivering oversized technology returns on investment (ROI). They accomplish this with advisory services, vCISO, vCIO, consulting, project implementation, solution architects, and a best-in-class subscription-based technology platform. Thrive delivers exceptional high-touch service through its POD approach of subject matter experts and global 24x7x365 SOC, NOC, and centralized services teams. Learn more at www.thrivenextgen.com or follow us on LinkedIn.
Meeting the New Cyber Insurance RequirementsIn 2023, there was a 72% increase in data breaches since 2021, which has previously held the all-time record. In response to this growing frequency of cyber threats, cybersecurity insurers have significantly revised their policies for businesses, making them more stringent and demanding in terms of risk mitigation and management. Insurers are now requiring businesses to demonstrate not just the presence of cybersecurity protocols, but also their effectiveness and ongoing maintenance. For example, organizations are expected to implement comprehensive security measures, including advanced threat detection, regular vulnerability assessments, and a robust incident response plan. Failure to meet these heightened standards could result in denied claims, leaving businesses exposed during a cyber event and costing them financially.
How to Reduce Cyber Risk in Healthcare OrganizationsIn February, hackers took Change Healthcare offline in one of the most high-profile and wide-reaching cyberattacks to date. Change Healthcare serves hundreds of thousands of providers in the U.S. and processes billions of transactions every year. With Change Healthcare’s systems compromised, cash stopped flowing for hospitals and physician offices everywhere. Providers couldn’t submit new claims, pharmacies couldn’t charge appropriately for prescriptions, and prior authorizations couldn’t go through for critical procedures.
Safeguarding Your Health: 5 Ways Healthcare Organizations Can Navigate Cybersecurity RisksThe healthcare industry poses a unique set of challenges when it comes to its cybersecurity framework. Hospitals, doctors’ offices, and local clinics are all home to vast amounts of sensitive patient and employee data. Hospitals alone store about 50 petabytes of sensitive data every year. In order to operate seamlessly and provide the best care possible, these healthcare havens need to ensure that their IT stack is robust. Cyber threats are rampant and have the potential to jeopardize patient privacy and safety, while also disrupting healthcare services to those in need and compromising the organizational integrity of the healthcare facility.
Navigating the SEC’s 8-K Reporting Mandate: Cybersecurity Challenges & Compliance RealitiesIt has been about a year since the SEC enacted its cybersecurity disclosure mandate, which requires the disclosure of any material cybersecurity breach on form 8-K, item 1.05, as well as cybersecurity-specific additions to companies’ annual 10-K filing.
Companies may still be grappling with questions surrounding the new rules and processes needed to meet the SEC’s requirements.
Fortifying Your Cybersecurity Chain: Understanding Third-Party Vendor RiskKevin Landt, the VP of Product for Cybersecurity at Thrive, explains how understanding third-party vendor risk can help companies fortify their cybersecurity chain from potential issues. This article originally appeared in Insight Jam, an enterprise IT community that enables human conversation on AI.
Meeting the New Cyber Insurance RequirementsIn the event of a cyberattack, companies – especially small to mid-sized businesses – often face losses so great they risk pulling their business under. With the number of ransomware attacks, phishing schemes, and data breaches on the rise, it only makes sense that business leaders and owners take steps to protect their businesses by investing in insurance – the same way they would protect company property and assets.
