Today, running a business (no matter the size, service or industry) requires having a set of processes in place to prepare for unrelenting cyber attackers who seek financial gain or are motivated by bringing someone’s company to a standstill.
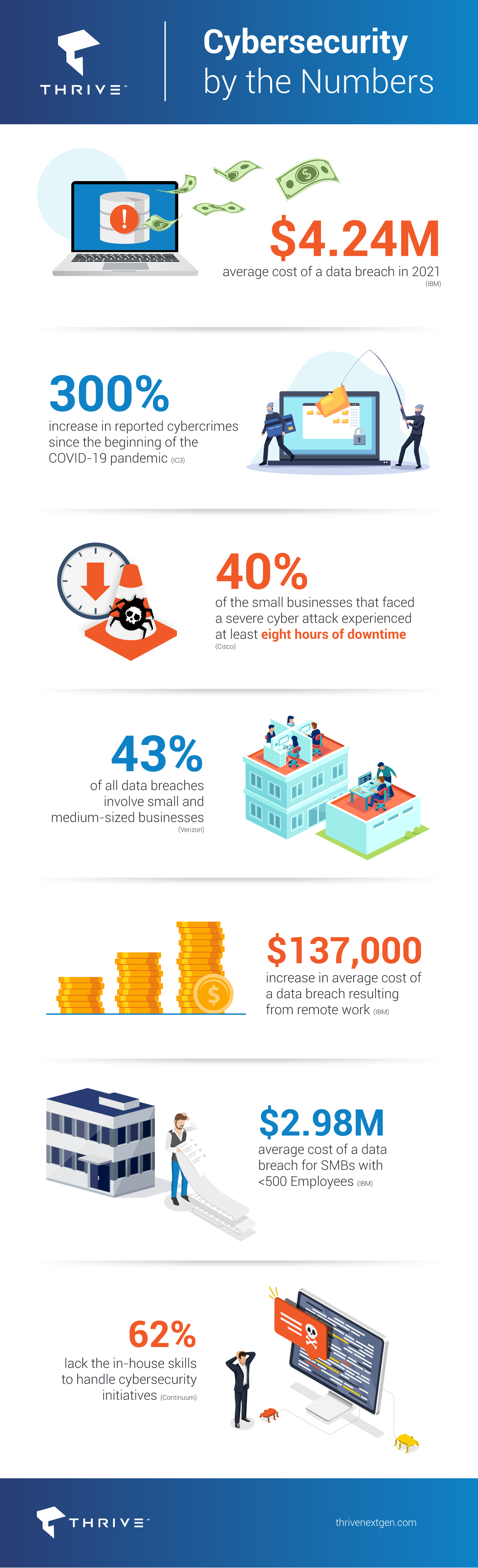
2021 saw the highest average cost of a data breach in 17 years, with the cost rising from $3.86 million to $4.24 million on an annual basis, according to the IBM Cost of a Data Breach Report. Since the pandemic began, the FBI has reported a 300% increase in reported cybercrimes. These cyber-attacks are often referred to as “trench cyber warfare” and mostly affect small business owners, localized infrastructure, and influential individuals. The purpose is to disrupt normal life and daily operations.
A benchmark study by Cisco found that 40% of the small businesses that faced a severe cyber attack experienced at least eight hours of downtime. This downtime accounts for a major portion of the overall cost of a security breach.
Here are some interesting trends that capture the cyber assault on SMBs:
- 43% of all data breaches involve small and medium-sized businesses
- Most employees do not know what to do after one occurs
- Remote work has increased the average cost of a data breach by $137,000
- The average cost of a data breach for SMBs with <500 Employees is now $2.98 million
Clearly SMBs are particularly vulnerable and, concerningly, 62% lack the in-house skills to handle cybersecurity. From hybrid work environments to the growing business imperative of shifting core IT functions to the cloud in order to compete and grow, organizations can minimize or avoid the impact of a cyberattack no matter where it originates or what type of attack it is.
How to Be Proactive
Complete a Cybersecurity Risk Assessment
A Cybersecurity Risk Assessment is the best way to determine a company’s security baseline and identify areas in an organization’s security protocol that need preventative attention and areas that are up to par. Identifying the current cybersecurity posture is the first step toward a more secured network.
Routinely Update Software
When new vulnerabilities are identified, developers release patches and updates to cover them. Ensure that all bases are covered, including OS updates, app, and firmware updates, and IT network asset updates.
Enforce MFA (Multi-Factor Authentication)
To the greatest extent possible, ensure that all users across all devices require at least a 2nd form of identification for access. Additionally, minimum password strength requirements are strongly encouraged to reduce the likelihood of a successful brute-force attack.
Provide End-User Awareness Training
The most effective way to stop cyberattacks is at their most common breach point – the end-user. Social engineering attacks, spear-phishing campaigns, and new SMS attacks (sometimes referred to as “Smishing”) all can be recognized and avoided with proper anti-phishing and cybersecurity awareness training.
Don’t let your organization become another statistic in the growing list of successful cyberattacks. With Thrive’s Cybersecurity Bundle, you can ensure that you’re covered from point A to point Z. Contact one of our experts today to learn more.
What Kind of Cloud Environment is Best for Your Business?The race to the Cloud accelerated with COVID. Businesses without any Cloud infrastructure or with weak Cloud infrastructure were suddenly made to move remote, and those with Cloud services in place were put to the test in terms of accessibility, availability, and security. Those with no remote access available to their users opted for public Cloud services like Microsoft Azure and 365 to get workers up and running as quickly as possible. Now, two years later, organizations that still haven’t made the move to private or hybrid Cloud environments are beginning to feel the repercussions in the areas of cybersecurity, governance control, and overall ease of managing their day-to-day workflows.
So what are the different Cloud types, and how do you choose what is best for your organization? The answer is almost always private Cloud for businesses, as a key to remaining competitive is maintaining a self-reliant, secure network infrastructure. However, there are exceptions; let’s take a deeper look at the differences between public, private, and hybrid Clouds:
Public Cloud
Public Cloud is the ‘out of the box’, Cloud-based solution for building and deploying various workloads. Administrators have controls over the various offering but not what is under the hood. In the public cloud, resources are shared across multiple organizations. The #1 benefit of working on a public Cloud server is the flexibility and scalability of working with a pre-packaged platform; taking on a new client or onboarding a round of new employees in a public Cloud is a breeze without the red tape of more sophisticated network infrastructures. The #1 concern with choosing to utilize public Cloud services is unpredictable cost; costs can go through the roof due to a pay-to-play pricing model where costs are incurred by the amount of data stored and shared rather than a single, flat usage fee.
Private Cloud
Private Cloud is quite the opposite of public Cloud in nearly every way. Perhaps the leading benefit of working on a private Cloud server is full control; admins have control over virtually every aspect of the Cloud environment – where data is stored, who can access it from what locations, multi-factor authentication (MFA) enforcement, more traditional file structuring, application hosting, and so much more. Purchasing space on a private Cloud server, or building your own, means that you can do nearly whatever you please with it, and for one flat fee! Different from public Cloud, also, is the ability to host business applications on a private Cloud server – so your favorite CRM or modeling software no longer has to run locally on each employee’s device, freeing up memory and enabling more efficient multi-tasking. The downfall to working from a private Cloud server is the level of expertise needed to set it up and monitor it properly; private Cloud services, like Thrive Cloud, are backed by a team of experts managing backups, monitoring for threats, overseeing user access, and more.
Hybrid Cloud
Hybrid Cloud is when an organization chooses to utilize the services of both public and private Cloud services. These scenarios might look something like storing and sharing documents on a public Cloud while running applications and hosting confidential materials on a separate private Cloud server. These environments can be beneficial because they allow for quick scalability using public Cloud while also utilizing the dedicated, safe Cloud computing services offered by private Cloud. On the downside, hybrid Cloud environments still leave organizations open to data loss caused by malicious attacks on any data not stored, monitored, and backed up in the private Cloud environment.
What’s Best for Your Business?
The answer to this question is often private Cloud, but it depends on a business’ openness to the risks often found on public Cloud environments. Cybersecurity is the number one component to consider when thinking about implementing a public Cloud solution into your business’ network architecture. How would your business recover if the files you work with in the Cloud were suddenly deleted or released to the public? Without the option for remote backups or the ability to control file access via MFA, storing files in the public Cloud is always a gamble.
Perhaps the biggest tradeoff between public and private Cloud, however, is cost. With a per-transaction or per-kilobyte fee, public Cloud can quickly grow to an astronomical cost compared to private Cloud environments which are often billed as a predictable, monthly fee. In times where quick scalability is needed, hybrid environments can be beneficial if you’re willing to pay the fee for that flexibility. At the end of the scaling period, however, migrating those users into the private Cloud environment might be the best cybersecurity-focused and financially-conscious move.
While there is no one right answer for every scenario, Thrive can assist in determining the best route to take for your business
Cutting Costs
So when exactly do private Cloud environments make financial sense for quickly growing companies that demand remote flexibility and optimized collaboration capabilities? Stay tuned for another blog where we’ll dive into tips and tricks for managing Cloud costs!
Want more info about getting your company up to speed in a Cloud-based world? Contact Thrive today.
How To Ensure Your IT Systems Comply with the Cash Payment RuleAccording to a study by the Federal Reserve, the number of cash payments from 2020 to 2021 increased, making it the first increase in cash usage in over 5 years.
While credit and debit cards are accepted in almost all businesses, there is still a cash economy. According to a study by the Federal Reserve, the number of cash payments from 2020 to 2021 increased, making it the first increase in cash usage in over 5 years. The average number of cash payments increased in October 2021, accounting for 20 percent of all payments. This is up from 19 percent in 2020.
This means that while the use of cash has decreased in recent years, it is still a part of our economy. In some cases, cash is the preferred method of payment. There are a few reasons for this. First, cash is a tangible form of currency. This can be reassuring to some people who prefer to have a physical representation of their money. Second, cash is a universal form of payment. It can be used in any country.
Given that cash is still a significant part of our economy, it’s important to know how to account for it. Government restrictions on cash transactions have become more common in recent years, so staying up-to-date on the latest regulations is important. Cash payment reporting requirements vary from country to country, so it’s important to know the rules in the countries where you do business.
What Is the Cash Payment Rule?
In the United States, the Cash Payment Rule is a regulation that requires businesses to report any cash payments they receive that are over $10,000. This rule is designed to help the government prevent money laundering and other criminal activities. Businesses that do not comply with the Cash Payment Rule can face severe penalties, including fines and imprisonment. If your business accepts cash payments, you must take steps to ensure that you comply with this regulation. Failure to do so could result in serious consequences.
Federal law requires businesses in the United States to report cash payments by filing IRS Form 8300. The purpose of this form is to help the government detect and prevent the following:
- Money laundering
- Tax evasion
- Bank fraud
- Terrorism
- Drug trafficking
If you receive a cash payment that is over the $10,000 threshold, you must take the following steps:
- Get the identification information of the person or business who made the payment. This includes their name, address, and taxpayer identification number.
- Calculate the cash you received from that person or business in a single day. This includes all forms of payment, such as cash, checks, and money orders.
- Report the total amount of cash you received on IRS Form 8300. You must file this form within 15 days of the transaction date.
- Keep copies of IRS Form 8300 and all supporting documentation for at least 5 years. This includes the identification information of the person or business who made the payment and the calculations you used to determine the total amount of cash received.
Who Must Comply with the Cash Payment Rule?
The Cash Payment Rule applies to all businesses that receive cash payments. This includes sole proprietorships, partnerships, corporations, and limited liability companies. The rule also applies to non-profit organizations, trusts, and estates. You must comply with the Cash Payment Rule if your business accepts cash payments.
What Are the Consequences of Violating Cash Transaction Limits Regulations?
Businesses that violate cash transaction limits can be subject to significant penalties, including fines and jail time. In addition, businesses that violate these regulations may be subject to special reporting requirements. These requirements can burden businesses significantly, as they may be required to track and report all cash transactions above a certain threshold.
How Can IT Systems Ensure Compliance with Cash Transaction Limits?
IT systems are a critical tool for ensuring compliance with cash transaction limits. These systems can track and record all cash transactions, making it easier for businesses to identify and report transactions exceeding the legal limit. In addition, IT systems can help businesses automate the filing of IRS Form 8300, making it easier to comply with the Cash Payment Rule.
There are a variety of IT systems available that can help businesses comply with cash transaction limits. These systems range from simple accounting software to complex enterprise resource planning (ERP) systems. When choosing an IT system for your business, selecting a system capable of tracking and recording all cash transactions is important. In addition, the system should be able to generate reports that can be used to comply with the Cash Payment Rule.
Here are a few ways in which IT systems can help businesses comply with cash transaction limits:
- Transaction Monitoring: IT systems can monitor cash transactions to ensure they do not exceed the limit. If a transaction does exceed the limit, the system can alert the business so that they can take appropriate action.
- Customer Identification: IT systems can help businesses identify their customers. This is important because businesses must be able to identify the person who is responsible for a cash transaction.
- Record Keeping: IT systems can help businesses keep records of their cash transactions. This is important because businesses must be able to provide these records to the government if requested.
- Compliance Reporting: IT systems can help businesses generate compliance reports. These reports show the government that a business complies with the Cash Payment Rule.
- Fraud Detection: IT systems can help businesses detect and prevent fraud. This is important because businesses could face severe penalties if money laundering or other criminal activities are involved.
The Cash Payment Rule is a critical regulation that businesses must comply with. IT systems can play a vital role in helping businesses comply with this regulation. By using streamlined IT systems, businesses can avoid the hassle and wasted time associated with manual compliance processes.
How Can Businesses Ensure That Their IT Systems Comply with the Cash Payment Rule?
As business and technology become increasingly intertwined, the question of compliance with regulations is increasingly important for businesses. With new technologies such as blockchain and cryptocurrency, businesses must stay up-to-date with the latest regulatory changes to avoid penalties.
Ensuring your IT systems comply with cash transaction limit regulations can be a complex task, but there are a few key steps you can take to simplify the process:
1. Keep Up-To-Date With The Latest Regulatory Changes
The first step to ensuring your IT systems comply with cash transaction limit regulations is to keep up-to-date with the latest changes. New technologies and regulations can emerge anytime, so it’s important to stay informed of any new developments. You can do this by subscribing to relevant news sources, attending industry events, or speaking with regulatory experts.
2. Conduct A Risk Assessment
Once you’re up-to-date with the latest changes, the next step is to conduct a risk assessment. This will help you identify any areas of your IT systems that may not comply with the new regulations. When conducting a risk assessment, consider the full scope of your IT systems, including any third-party vendors or service providers.
3. Implement The Necessary Changes
After conducting a risk assessment, you may need to implement changes to your IT systems to ensure compliance. These changes can range from simple updates to your internal processes to more complex changes, such as implementing new software or upgrading your hardware. Depending on the extent of the changes, you may need to seek external help from IT consultants or service providers.
4. Test & Verify The Changes
Once you’ve made the necessary changes to your IT systems, testing and verifying that they are fully compliant with the new regulations is important. This can be done by conducting internal audits or working with an external compliance testing firm.
5. Create A Compliance Management Plan
After ensuring your IT systems comply with the latest cash transaction limit regulations, you should create a compliance management plan. This plan should outline the steps you’ll take to maintain compliance in the future, such as conducting regular risk assessments and keeping up-to-date with regulatory changes.
These steps will help ensure your IT systems comply with cash transaction limit regulations. However, compliance is an ongoing process, so it’s important to review your compliance management plan and make necessary changes regularly.
Thrive specializes in providing end-to-end IT solutions to businesses of all sizes. We offer a complete range of IT services that can be customized to meet the specific needs of your business. Our team of highly skilled and experienced IT professionals can provide you with the expertise you need to take your business to the next level. We are committed to providing the highest quality IT services and solutions at competitive prices.
Contact us today for more information on how we can ensure your IT systems comply with cash transaction limit regulations.
What Is the Gramm-Leach-Bliley Act (GLBA)?The Gramm-Leach-Bliley Act (GLBA), also known as the Financial Services Modernization Act of 1999, is a United States federal law that repealed the Glass-Steagall Act of 1933.
As our world becomes more and more digital, we store an increasing amount of sensitive information online. This is why government laws and regulations are constantly being updated and enacted to protect consumers’ information. One of these laws is the Gramm-Leach-Bliley Act (GLBA).
The Gramm-Leach-Bliley Act (GLBA), also known as the Financial Services Modernization Act of 1999, is a United States federal law that repealed the Glass-Steagall Act of 1933. GLBA was passed by Congress in response to the changing nature of the financial services industry, which had seen a dramatic increase in the number of mergers and acquisitions between banks, securities firms, and insurance companies.
The GLBA requires financial institutions to disclose their information-sharing practices to their customers and to take steps to protect the non-public personal information of their customers. The GLBA also imposes restrictions on sharing certain customer information between financial institutions and non-affiliated third parties.
There are three main categories of protection:
- The Financial Privacy Rule: This rule requires financial institutions to provide customers with a privacy notice that explains what information is collected about them, how it is used, and what steps are taken to protect it. See 16 CFR Part 313.
- The Safeguards Rule: This rule, as the name suggests, requires financial institutions to take steps to protect customer information from unauthorized access or theft. This may include physical, electronic, and procedural safeguards. See 16 CFR Part 314.
- The Pretexting Rule: This rule prohibits financial institutions from sharing customer information with third parties unless the customer has been given the opportunity to opt out or has specifically consented to the sharing. See 15 USC § 6821.
On October 27, 2021, the Federal Trade Commission (FTC) finalized a rule to amend the Gramm-Leach-Bliley Act (GLBA) Safeguards Rule and the Privacy Rule. The intentions of the update were to ensure the security and confidentiality of customer information, protect against any anticipated threats or hazards to the security or integrity of such information, and protect against unauthorized access to or use of such information that could result in substantial harm or inconvenience to any customer.
What Businesses Does GLBA Cover?
The law defines financial institutions as companies that offer products and services that are “financial in nature.” The GLBA applies to any financial institution subject to the jurisdiction of the federal banking agencies, the Securities and Exchange Commission, or the Commodity Futures Trading Commission.
These businesses can include:
- Banks
- Credit unions
- Securities firms
- Insurance companies
- Auto dealerships
- Mortgage brokers
- Tax preparers
What Types of Data Does the Gramm-Leach-Bliley Act Protect?
The GLBA applies to any type of customer information used to identify an individual. Non-public personal information (NPI) is a key concept in the GLBA. NPI is any information about an individual that is not publicly available and that can be used to identify that individual.
Examples of NPI include:
- Social Security Numbers
- Driver’s License numbers
- Bank account numbers
- Credit card numbers
- Home address
- Birthdate
Complying with GLBA regulations can be challenging for companies, especially those not used to handling customer data. However, complying with these regulations will put your organization at a lower risk for privacy issues.
Non-compliance with GLBA requirements can result in the following:
- A civil penalty of up to $100,000 per violation
- Individuals in charge of compliance may be subject to criminal penalties of up to $10,000
- individuals who knowingly and willfully violate the GLBA may be subject to imprisonment of up to five years
How Can Organizations Become GLBA Compliant?
Compliance with government regulations like the Gramm-Leach-Bliley Act (GLBA) is more important than ever for businesses in the financial services industry. Gaining a thorough understanding of the Safeguards Rule is an important step in becoming GLBA compliant because this rule focuses on the confidentiality and security of customer information.
To comply with the Safeguards Rule, businesses must do the following:
- Designate an employee or employees to oversee the development and implementation of the security program
- Conduct a risk assessment to identify potential threats or hazards to customer information
- Develop and implement policies and procedures to address the risks identified in the risk assessment
- Train employees on the security program and policies and procedures
- Test the security program to ensure that it is effective
Getting and staying GLBA compliant can seem difficult and daunting for financial institutions. You take pride in protecting your customer’s data, but it can be hard to keep up with the ever-changing compliance landscape. That’s where managed IT comes in. Managed IT providers can help you meet GLBA compliance standards and exceed them. By working with a managed IT provider, you can have peace of mind knowing that your customer’s data is always safe and secure.
Thrive Can Help With GLBA Compliance
Thrive offers premier managed IT services that can help financial institutions in Miami and Fort Lauderdale comply with the Gramm-Leach-Bliley Act. Our network security services include, but are not limited to:
- Penetration Testing
- Firewall Management
- Intrusion Detection and Prevention
- Vulnerability Management
- Web and Email Filtering
- Security Assessments
- Malware Protection
We understand how complex and time-consuming it can be for financial institutions to keep up with the latest compliance regulations. This is why our team of IT experts will work closely with you to ensure that your IT infrastructure is secure and compliant.
We will take the following steps to secure your IT infrastructure:
- Perform a comprehensive security assessment of your current IT infrastructure
- Identify any vulnerabilities and potential risks
- Implement the necessary security measures to mitigate those risks
- Regularly monitor your IT infrastructure for any changes or new risks
Your technology should not be a roadblock to growth but a strategic asset that helps you meet your business goals. With our managed IT services, you can focus on your core competencies while we take care of the rest. We take the time to learn about your business from top to bottom to provide you with the most comprehensive IT solution possible.
Please contact us if you would like to learn more about our managed IT services and how we can help your financial institution in Miami or Fort Lauderdale comply with the Gramm-Leach-Bliley Act. We look forward to hearing from you!
Cheers to 1000! Thrive Experiences 200 Percent Growth in Employees Since Jan 2021It feels like a lifetime has gone by since January of last year – but we are proud to share that Thrive has experienced 200 percent growth in its employee headcount since this time. We’d like to say welcome to all of the new team members who have joined the Company in recent months – and cheers to reaching 1,000 employees!
We have made six acquisitions in 2022, bolstering our technology offerings and strengthening our managed services to help businesses optimize business performance, ensure scalability, and future-proof digital infrastructure operations.
We have diversified our customer base, reaching customers in financial services, healthcare, professional services, life science, state and local government, and manufacturing. Our leadership has been busy pounding the pavement to boost their technical chops, expand our engineering team and advance Thrive’s cybersecurity services to meet the dire need in the market for safeguarding your business.
Need more proof? Check out some of our stats in the last year – and check out our newsroom to keep tabs on Thrive in the news.

The future of education is in the cloud. According to Technavio marketing research, the global cloud computing market in K-12 education will see a compound annual growth rate of 18.77%, growing by 1.74 billion dollars through 2026 as educators try to enhance productivity, and improve the overall learning experience. To do this, they’re leveraging virtualization in cloud computing, migrating learning modules, student and faculty activities, as well as data storage to the cloud with strict data protection protocols in place. Findings from an EdWeek survey corroborate this, with 80% of education technology leaders stating that their districts are using cloud-based software to save time and money. Let’s look at some of the top ways the cloud is changing education.
The cloud eliminates the need for expensive and outdated textbooks.
College and university students, who generally need to buy new books each year for each class, spend an average of $1,200 per year on textbooks. Meanwhile, K-12 schools spend $700 per student per year—and because it’s funded through tax dollars, they’ve become a major expense to the public at large. That’s not even the worst of it; on average, textbooks tend to be nearly a decade old, teaching outdated or simply wrong information. Textbooks are often even older in low-income areas, putting these students at a distinct disadvantage.
Cloud-based textbooks can solve both problems. Digital content costs significantly less than printed material. This can save college and university students hundreds per year and help level the playing field between lower and higher-income students. Cloud-based materials can also be easily updated so students always have access to the most current learning resources.
Virtualization in cloud computing eliminates the need and cost of expensive hardware.
It used to be that every school would have a room full of on-premise servers that ran all systems and held all data. This could get expensive whenever capacity was reached and new servers had to be purchased. But with most third-party cloud providers, schools only pay for the capacity they use, much like a utility. That’s not all; in a cloud-based model, schools don’t have the expenses associated with server room cooling, electric, and maintenance, which can get very costly, especially in warm-climate states (not to mention the need to keep them cooled and operational even when not in use during the extended holiday breaks). Finally, with many schools facing overcrowding, eliminating a server room frees up valuable space!
The cloud offers easy accessibility and mobility.
In the cloud, applications can be run on internet browsers, so schools and students don’t necessarily have to own pricey computers or laptops; an inexpensive smartphone or tablet can allow access to lesson plans, coursework, and digital textbooks. The cloud also gives teachers the ability to work from home in order to finish up their work. Rather than getting to school hours before the first bell rings and staying hours after the last bell, teachers can grade tests and homework assignments, develop course curricula, enter grades, and respond to parents from the comfort of their homes when it’s convenient for them. With the 2021 EducationWeek report revealing that over 60% of teachers are highly stressed out and describing their mental health as “not good,” this could go a long way toward helping relieve their stress, which ultimately creates a better learning environment.
Virtualized data in the cloud offers more collaboration.
The cloud offers seamless integration between schools and university departments through file-sharing across any device, so faculty no longer needs a specific medium in which to collaborate or communicate with others. For students, the power of collaboration is also key when it comes to learning and preparing for the workforce. Students can work within virtual classrooms, communicate with students far away in real-time, and combine the education of people from completely different backgrounds. And because kids frequently get sick, they won’t have to miss assignments or give up participating in classroom discussions. This may also open the door for home-schooled children to participate with other students without attending class.
The cloud eliminates costs associated with paper—while cutting the carbon footprint.
Most educators are concerned about their carbon footprint—and more and more young people are worried about the environment, too. But education is one of the worst offenders when it comes to paper usage (or more appropriately, paper waste). Edutopia did some number crunching and found that on average, a school with 100 teachers uses approximately 250,000 pieces of paper per year. Based on paper costs, that’s $25,000, and printing on that paper would be another $7,500 per year, not to mention costs of copy toner and service agreements. Through the cloud, these schools can significantly reduce their carbon footprint and put over $30,000 back into the budget each year. (It’s worth noting that eliminating individual server rooms in schools can also significantly cut back on CO2 emissions and energy consumption, also making the school greener!)
How Thrive can help
Schools, colleges, and universities can greatly benefit from virtualization in cloud computing. They can reduce costs (and when funding is constantly being cut, this is huge), promote a better learning environment for students, and create a better working environment for educators. Thrive can help K-12 schools or post-secondary institutions move to a public cloud, hybrid cloud, or virtual private cloud with ease. Contact Thrive to learn more.
3 Things You Can Do to Boost Collaboration EffectivenessBusiness is a collaborative effort, and no one individual putting in all the work will create the same results as a well-oiled group fueled by cooperative collaboration. To help your organization build this type of productive collaboration, we’ve put together three tips you can implement to maximize your team’s willingness and capabilities to work together.
Promote a Culture of Collaboration
Employees can get so preoccupied with their work that they might be unaware of what the rest of the office is caught up with. When teams are siloed and don’t know what is going on elsewhere in the business, it can be a problem in the long term. If you want to promote collaboration in the workplace, you should make sure that collaboration is not only expected, but also encouraged. Creating this culture of collaboration can be challenging, but it can lead to a higher degree of fulfillment, satisfaction, and engagement within your workforce.
Hold Regular Staff Meetings
If your staff see each other every so often, but not regularly, they might be more reluctant to collaborate. Regular staff meetings give your team members a chance to catch up with everyone else on what each department is doing and how they are all working together toward the same goals. If you give your team more opportunities to get engaged and involved in this way, you can facilitate better collaboration moving forward.
Implement Collaborative Technology Solutions
It is hard to encourage collaboration if your team doesn’t have the tools to make it happen in a remote or hybrid environment. Plus, depending on the size of your workforce, it might be hard to gather everyone in one place for a staff meeting. Software tools that allow for meetings and collaboration are more accessible now than they have ever been before. Video conferencing, instant messaging, file sharing, and more are all staples in the collaborative space, and any organization hoping to make it happen without them will be in for a rude awakening.
How does your business handle its collaborative efforts? You can take things up a notch by working with Thrive. We can equip your business with all of the best tools to make collaboration easy and less of a pain. To learn more about what we can do for your business, contact us.
Responding to Cyber Attacks AbroadAmidst Russia’s attack on Ukraine, one may find it unsurprising to hear of Russian cyberattacks targeted at weakening infrastructure in Ukraine. While some efforts have successfully infiltrated Ukrainian networks and wreaked havoc on the lives of citizens, Russia’s cyber attacks can best be described as trench cyber warfare and have most affected small business owners, localised infrastructure, and influential individuals.
Strontium, a group known also by the names Fancy Bear or APT28, has been specifically targeting Ukrainian infrastructure entities as well as EU & US government bodies involved in foreign policy decision making. After successful breaches outside of the conflict zone were identified, governments and private companies alike have stepped up to help curb the success and influence of Russian hackers.
NCSC Advisory
On the 11th of May, the National Cyber Security Centre (NCSC) jointly issued an advisory for service providers and their customers, outlining steps to better protect themselves in light of Russia’s attacks on Ukraine. This advisory was pushed alongside the UK’s partners in the US, Australia, Canada, and New Zealand, and urges MSPs and their clients to strongly consider implementing the following procedures:
- Enable and contractually require MFA on all customer services and products
- Conduct rigorous security risk assessments across all groups to identify vulnerabilities and prioritise resource allocation
- Enable monitoring and logging
- Keep log records for at least 6 months, as there is often a lag between when a breach occurs and when it is detected
US Department of Justice (DOJ) Efforts
The US DOJ successfully disrupted thousands of internet-connected firewall devices that had been compromised by the alleged GRU-sponsored group, Sandworm. Following a court-authorised procedure, the National Security Division of the DOJ targeted a range of Command and Control (C2) servers that were operating the botnet by closing the external management ports which Sandworm had originally used to access them.
Help from Microsoft
Since 2016, Microsoft has been working to dismantle Russian GRU-connected actors such as Strontium and Sandworm. Through a specially designed legal process established to enable Microsoft to receive quick access to the resources needed to disrupt these groups, they have successfully seized control of over 100 Strontium-controlled domains on 15 separate occasions alone.
CISA
Cybersecurity authorities in the US, Canada, Australia, New Zealand, and here in the UK jointly issued a Cybersecurity Advisory (CSA) on the 20th of April 2022 warning against Russian-sponsored actors as well as Russian-supporting cybercrime groups. Among the tactics listed were ransomware, DDoS attacks, and destructive malware – all used in efforts to maintain persistent intrusive access to IT networks, extract sensitive data from those networks, and disrupt critical industrial control systems (ICS).
Avoiding Impact of Cyber Attacks
There are many steps organisations and individuals can take to avoid and/or minimise the impact of a cyberattack, no matter its geographic source.
1. Complete a Cybersecurity Risk Assessment
A Cybersecurity Risk Assessment is the best way to determine your baseline and identify areas in your security protocol that are up to par and areas that need preventative attention. Knowing the current state of your cybersecurity posture is the first step towards a more secured network, and Thrive can help.
2. Routinely Update Software
When new vulnerabilities are identified, developers release patches and updates to cover them. Ensure that all of your bases are covered, including OS updates, app and firmware updates, and IT network asset updates.
3. Enforce MFA
To the greatest extent possible, ensure that all users across all devices require at least a 2nd form of identification for access. Additionally, minimum password strength requirements are strongly encouraged to reduce the likelihood of a successful brute-force attack.
4. Provide End-User Awareness Training
The most effective way to stop cyberattacks is at their most common breach point – the end-user. Social engineering attacks, spear phishing campaigns, and new SMS attacks (sometimes referred to as “Smishing”) all can be recognised and avoided with proper anti-phishing and cybersecurity awareness training from Thrive.
What Is Your Risk Exposure?
Russia is not the first, nor the last, government body to engage in cyber warfare for monetary or military gain. While Russia’s efforts have been targeted at Ukrainian entities and politically influential groups abroad, cyberattacks originate and target people from all corners of the globe. Keep your cyber defence mechanisms up to date with a team that is on the cutting edge of security news – contact Thrive today to learn more.
Maximizing Microsoft 365Microsoft 365 is a robust suite of collaboration tools oftentimes underutilized by its users. More than just a range of solutions for video chatting, text chatting, document building, and document sharing, Microsoft 365 offers an advanced level of customizability over administration, governance, front end appearance, implementation, security, and more. Paired with Power Platform, choosing Microsoft 365 could not only improve your business’ security posture and collaboration efficiency, it also has the potential to gather and analyze crucial data to unlock a new level of business forecasting, client behavior tracking, and user interaction analytics.
This white paper is to provides a summary of what each tool in Microsoft 365 offers and how they all come together seamlessly to offer users more than just a place to store their files and communicate. Download this guide to learn how to best maximize your Microsoft 365 investment.
DOWNLOAD our white paper today!

Cyberattacks have caused many millions of dollars’ worth of damage to businesses over the past several years, so it makes sense that your business should invest in its cybersecurity to mitigate these damages. That said, there is only so much you can invest into your cybersecurity budget, as you have to factor in other parts of your business, too. Today, we want to share with you three ways you can invest in cybersecurity initiatives that won’t completely break your bank.
Many organizations hire a CISO, or Chief Information Security Officer, to handle the management of their cybersecurity budget and the general security management for IT resources. This individual might operate under the CIO, but they have the chief responsibility to ensure that the cybersecurity budget is allocated as the business sees fit. Here are four tips you should keep in mind when finding your CISO.
Identifying Your Organization’s Digital Strengths and Weaknesses
Most IT implementations are rooted in an understanding of your infrastructure’s strengths and weaknesses. In order to get the most out of your IT capital, it helps to know just what needs to be addressed and where you can benefit the most. You might be shocked by how much an audit can help with this process. Some of the common issues suffered by small businesses include:
- Business continuity plans: Businesses don’t always have contingency plans in place for the worst-case scenarios, especially for their IT systems. If they’re not careful, downtime could become a serious problem in the event of a disaster.
- Phishing and cybersecurity training: With the threat landscape constantly changing, you’ll want to make training your staff a priority. Phishing attacks are the top way malware spreads across systems.
- Cybersecurity insurance: Cybersecurity insurance does exist, and it can help to protect against data loss and cyberattacks.
A comprehensive security audit can help your business address the many challenges it might face moving forward.
Aligning Your Security to Support Your Business
Certain investments might be practical, but they also need to suit your business’ specific needs. Security spending is something that can be justified as long as risks can be managed appropriately. To this end, you should invest in solutions that provide a return on your investment over the long term such as risk mitigation, regulatory compliance, and solutions that also boost productivity and efficiency, such as automation. This can justify the expenses associated with automated security processes.
Onboard Solid Contributors
The final piece of the puzzle involves building a strategy that requires investments be made in your IT infrastructure. Whether you are trying to hire new employees or bring in professionals to help train your existing workforce, investing in the people power of your business will always be fruitful. The more your employees understand about the role they play in securing your business, the easier it will be to keep your organization safe.
Network security doesn’t have to be challenging. If you make informed decisions about your security investments, you can remain confident that your organization will be making the right decisions moving forward. To learn more about how Thrive can fit into your IT decision-making process, reach out to our professional technicians and consultants.
