Cybersecurity
What a Better Cybersecurity Posture Looks for SMBs

Today, running a business (no matter the size, service or industry) requires having a set of processes in place to prepare for unrelenting cyber attackers who seek financial gain or are motivated by bringing someone’s company to a standstill.
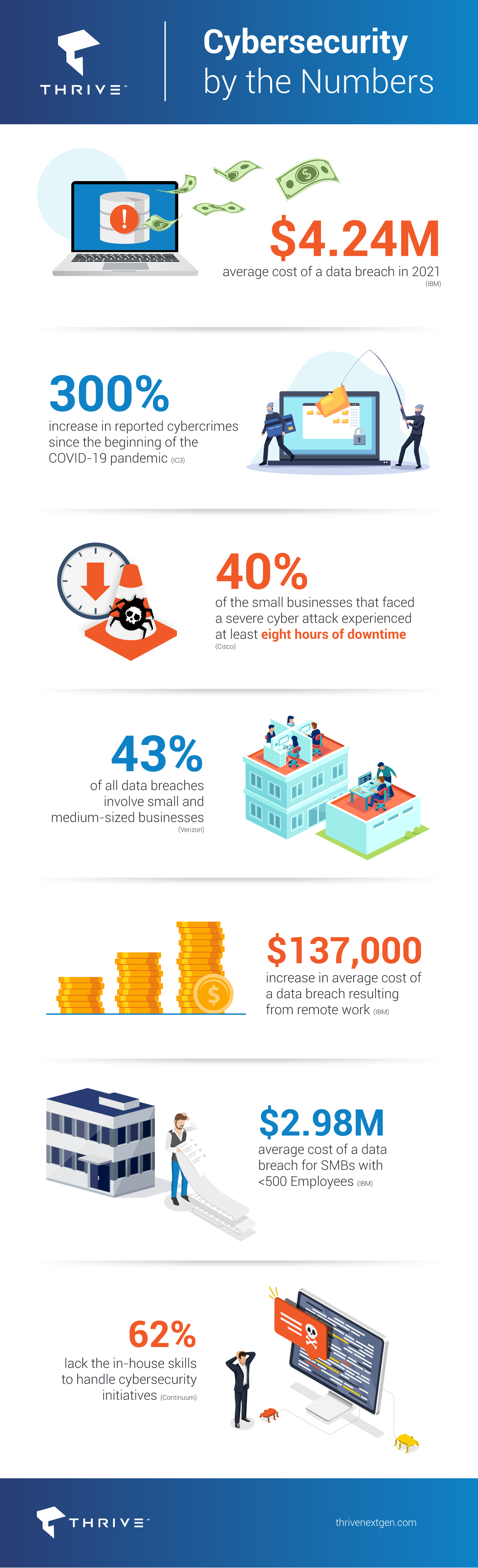
2021 saw the highest average cost of a data breach in 17 years, with the cost rising from $3.86 million to $4.24 million on an annual basis, according to the IBM Cost of a Data Breach Report. Since the pandemic began, the FBI has reported a 300% increase in reported cybercrimes. These cyber-attacks are often referred to as “trench cyber warfare” and mostly affect small business owners, localized infrastructure, and influential individuals. The purpose is to disrupt normal life and daily operations.
A benchmark study by Cisco found that 40% of the small businesses that faced a severe cyber attack experienced at least eight hours of downtime. This downtime accounts for a major portion of the overall cost of a security breach.
Here are some interesting trends that capture the cyber assault on SMBs:
- 43% of all data breaches involve small and medium-sized businesses
- Most employees do not know what to do after one occurs
- Remote work has increased the average cost of a data breach by $137,000
- The average cost of a data breach for SMBs with <500 Employees is now $2.98 million
Clearly SMBs are particularly vulnerable and, concerningly, 62% lack the in-house skills to handle cybersecurity. From hybrid work environments to the growing business imperative of shifting core IT functions to the cloud in order to compete and grow, organizations can minimize or avoid the impact of a cyberattack no matter where it originates or what type of attack it is.
How to Be Proactive
Complete a Cybersecurity Risk Assessment
A Cybersecurity Risk Assessment is the best way to determine a company’s security baseline and identify areas in an organization’s security protocol that need preventative attention and areas that are up to par. Identifying the current cybersecurity posture is the first step toward a more secured network.
Routinely Update Software
When new vulnerabilities are identified, developers release patches and updates to cover them. Ensure that all bases are covered, including OS updates, app, and firmware updates, and IT network asset updates.
Enforce MFA (Multi-Factor Authentication)
To the greatest extent possible, ensure that all users across all devices require at least a 2nd form of identification for access. Additionally, minimum password strength requirements are strongly encouraged to reduce the likelihood of a successful brute-force attack.
Provide End-User Awareness Training
The most effective way to stop cyberattacks is at their most common breach point – the end-user. Social engineering attacks, spear-phishing campaigns, and new SMS attacks (sometimes referred to as “Smishing”) all can be recognized and avoided with proper anti-phishing and cybersecurity awareness training.
Don’t let your organization become another statistic in the growing list of successful cyberattacks. With Thrive’s Cybersecurity Bundle, you can ensure that you’re covered from point A to point Z. Contact one of our experts today to learn more.
