Cybersecurity
Secure Score – Blocking Automatic Forwarding

Secure Score is a service provided by Microsoft to give administrators a guideline of how to better secure their tenant. Think of it as a credit score for Office 365. Guideline tasks can vary from reviewing audit logs to enabling MFA on all user accounts.
In this article, we will address a specific secure score metric — Enable Client Rules Forwarding Block Advanced Action. We’d like to address this specifically, as the rules that Secure Score assist you in making do not work as intended and do not cover all bases when it comes to disabling the Auto Forwarding feature in Exchange Admin.
Exchange Admin – Mail Flow / Transport Rules
When using Secure Score and looking at the Enable Client Rules Forwarding Block Advanced Action metric, you will notice that they have an option to “Apply” a rule to your Exchange Admin Center.
The rule that Microsoft creates attempts to filter messages that are received internally and block them if they have the type of “Auto-Forward” and are sent to an external organization. The purpose of this rule is to minimize the possibility of sensitive information leaving your organization (especially without you knowing it).
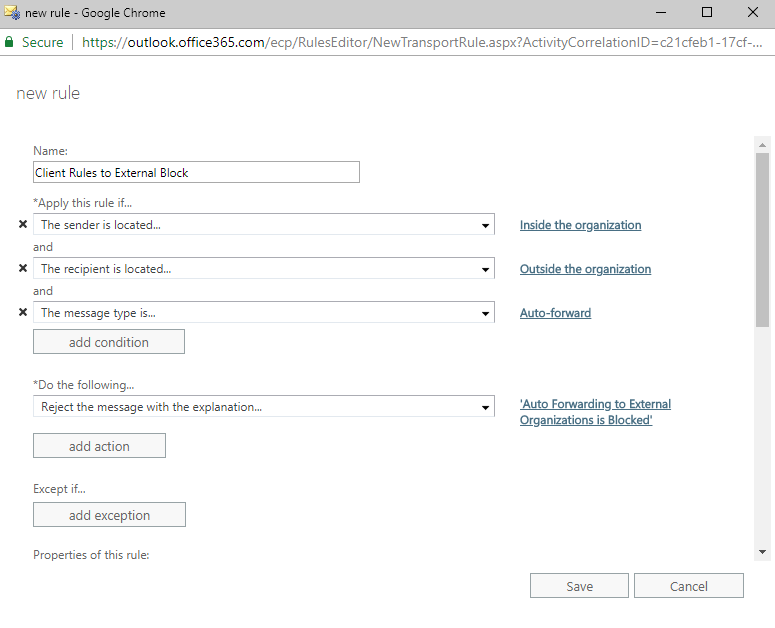
There are a few issues with this rule.
For one, this rule only blocks auto-forwarding if the message was sent from someone inside your organization and you auto-forward it outside. This means that someone could send your users a message from outside the tenant, and it will successfully auto-forward outside the tenant again.
To solve this issue, we need to have two rules instead of one: one that blocks auto-forwarding if the message was received internally and sent externally and one that was received externally and sent externally.
The second issue is that the rule attempts to pick up on the type of “Auto-forward”, but it does not seem to work. In this case, we found that a unique header can be used to block these messages successfully.
Filtering messages based on the “X-MS-Exchange-Generated-Message-Source” header for a result that includes “Mailbox Rules Agent” will successfully block auto-forwarded messages.
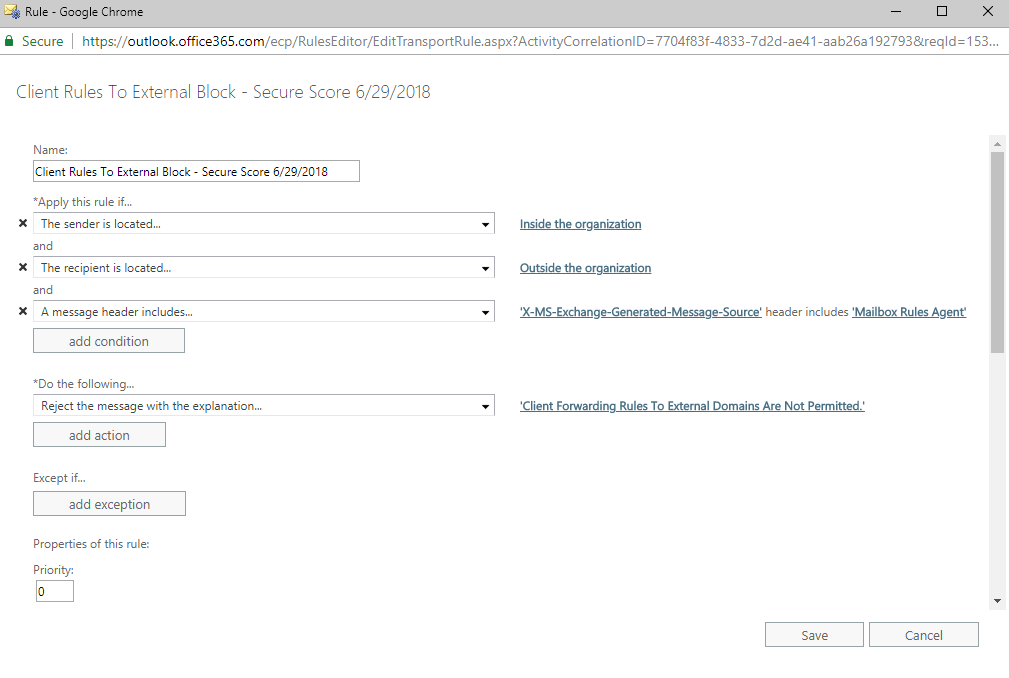
The rule above takes care of blocking messages received internally and sent externally. The following rule takes care of blocking messages received externally and sent externally.
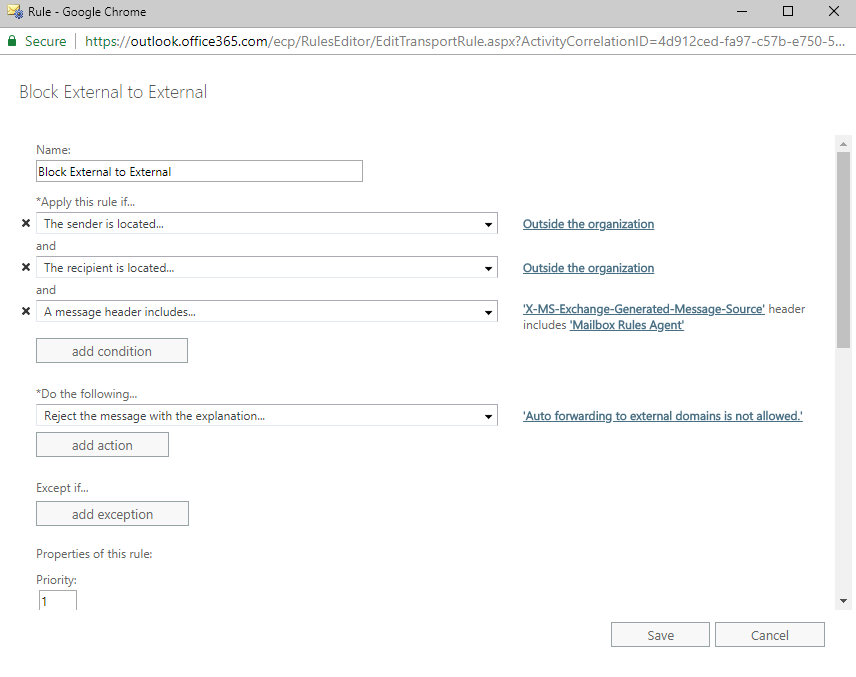
Now that these two rules are set up, we should be successfully blocking auto-forwarding to external organizations. However, there is one more step we need to take to complete this process.
Auto-forwarding in Office Web Apps
Unfortunately, a user will still be able to successfully auto-forward messages if they set up auto-forwarding within OWA in their settings (as shown below).
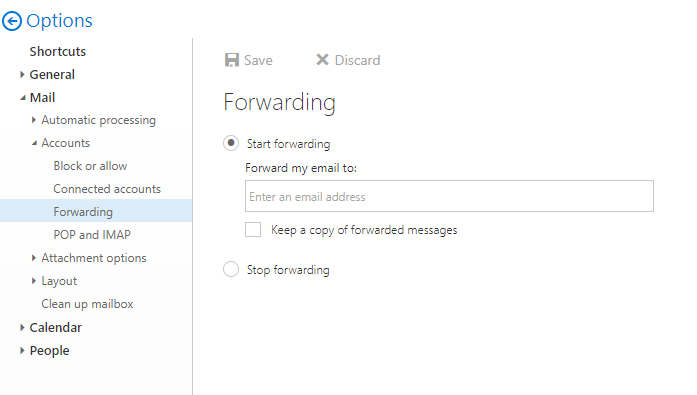
The mail flow rules only filter out messages that are set up using Inbox Rules. To disable the ability to auto-forward in OWA we need to head over to the “Remote Domains” section in Exchange Admin.
Once there, edit the Default policy and uncheck the box for “Allow automatic forwarding”.
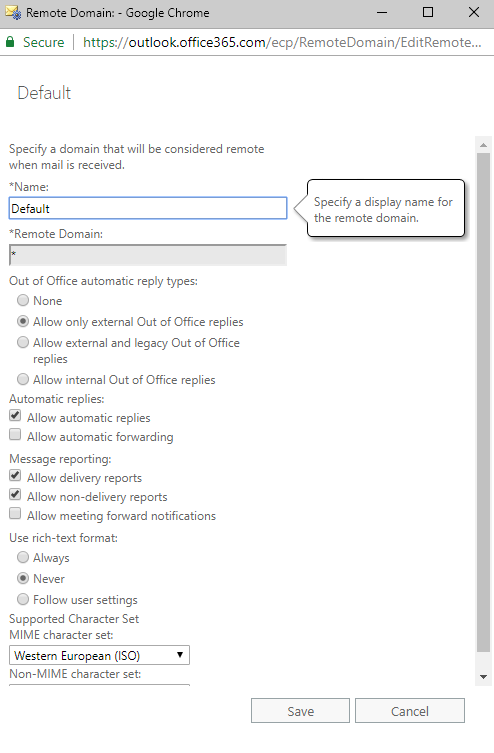
Save your changes, and you should be all set for blocking all automatic-forwarding to external organizations!

