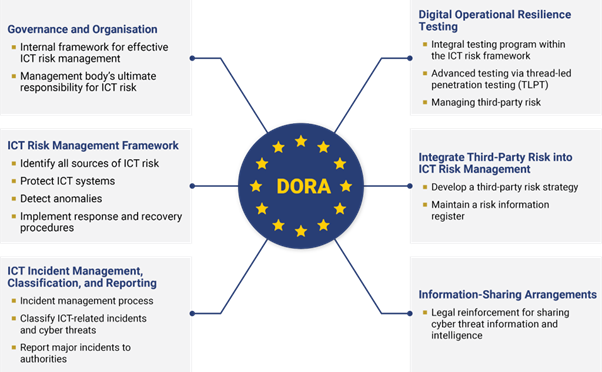
DORA Compliance
Why DORA Compliance Is Important
- Operational Resilience
- Regulatory Alignment
- Data Protection
- Third-Party Risk Management
- Market Confidence
- Standardized Approach
How Thrive Can Help
Thrive strengthens clients’ operational resilience with our robust platform, reducing reliance on single systems and enhancing risk management in alignment with Digital Operational Resilience Act (DORA) objectives. Partner with Thrive to address DORA requirements, including:
- Resilience Testing
- Third-Party Risk Management and Oversight
- Incident Response, Audit Trails, and Governance
- Critical Risk Management Frameworks and Daily Operations
Thrive supports required processes with vCISO policies based on CIS and NIST. Thrive also has newer policies for AI and other emerging areas. From incident response and SIEM to day-to-day compliance-ready operations, Thrive can provide thorough records for auditors. We also assist with gap analyses to identify and address implementation needs.
Note: Nothing herein shall constitute legal advice, compliance directives, or otherwise. Customers and prospective customers should consult a solicitor and/or other compliance professional regarding their organisations’ compliance obligations, including, without limitation, the regulations described herein.


Thrive Is the DORA-Ready Partner You Can Trust
Thrive has assessed the operational policies and procedures of our offerings listed below and will attest in the applicable service agreements to their alignment with DORA compliance requirements for service providers, including CTPPs, financial services, and ICT third-party service providers. This assists firms to implement resilient and secure solutions in accordance with DORA regulations.
Service providers must verify that their IT providers meet DORA compliance standards before provisioning even basic managed services. This includes managed systems, as third-party access to critical systems and sensitive data can impact operational resilience and regulatory alignment.

DORA-Ready Managed Cybersecurity and IT Services
Thrive’s portfolio of integrated, Next-Generation services are fully CJIS Compliant and include:
- Autonomous Penetration Testing
- Incident Response and Remediation
- vCISO
- Cybersecurity Mesh Architecture with Identity Management
- Vulnerability Scanning and Assessments
Learn More About DORA Compliance
Ready to Simplify Compliance? Let’s Talk.
Compliance Disclaimer
The information on this web page may not be construed or used as legal advice about the content, interpretation or application of any law, regulation or regulatory guideline. Customers and prospective customers must seek their own legal counsel to understand the applicability of any law or regulation on their use of Thrive services. Please also note that the relevant contract(s) between you and Thrive determine(s) the scope of services provided and the related legal terms and this page is provided for reference purposes only, and is not part of, and does not otherwise create or amend, any agreement, warranties, representations or other obligations between you and Thrive. Thrive disclaims any terms or statements contained herein that seek to impose legal or operational requirements on Thrive for the delivery of the services. Customers acknowledge that they remain solely responsible for meeting their legal and regulatory requirements. By accessing this content, customers and prospective customers acknowledge the information provided herein and/or any of the attachments accessible via this page shall strictly be considered as general commentary and nothing herein shall constitute legal advice or otherwise.