With many of us working from home during COVID-19, one unexpected benefit remote workers may be experiencing is better performance and faster response times to the business applications that are used daily to perform our jobs, such as email in Office 365 or GSuite, Salesforce, Dropbox and many other cloud-based applications. This improved performance may be a result of not traversing across a corporate network to get access to the internet to reach these cloud-based applications. You may have a more direct path to these applications from home than you have from your office, especially if you work at a remote branch office that is tied to a corporate network.
This unprecedented event has proven that the internet is clearly capable of providing enterprise level networking. Surely, each of us has experienced the occasional fuzzy video or audio drop, but by and large, the internet has held up well with the big spikes in network traffic since stay at home orders were put in place.
As organizations will look to cut costs with reduced budgets, Software Defined Wide Area Networking (SD-WAN) provides an opportunity to lower network costs while improving application and network performance for the branch offices to cloud-based applications you’re accessing from home today. SD-WAN enables you to augment or replace your traditional legacy WAN services with lower cost broadband internet services for direct access to cloud-based applications and ensures that performance is not sacrificed in doing so.
Security must still be a key consideration when implementing a SD-WAN solution as enabling direct internet access at branch offices opens the network to more entry points for potential threats. Combining network security and SD-WAN onto a single platform provides the ability to gain improved remote branch application performance while ensuring your critical assets and data are protected from outside threats. A combined Secure SD-WAN platform also reduces equipment costs and management complexity. Organizations with legacy MPLS network infrastructure should take a hard look at the performance and cost benefits a secure SD-WAN solution can provide as more and more applications move to the cloud and out of the corporate data center.
To learn more about Managed Secure SD-WAN, CONTACT US TODAY!
Boston Buisness Journal – Here are all this year’s Fast 50 companies Power Automate – Avoiding “File Locked For Shared Use” Failing Your WorkflowIn our workflows, we often need to perform file metadata updates, check-ins, moves, etc. If a file is locked and we do not account for it, it can fail our workflow entirely and prevent it from moving forward.
Consider a common scenario of running an approval flow that updates a Status field or other fields based off of the stage of the workflow and end-user responses. Utilizing a “Do until” loop and configuring the “run after” settings of actions we can ensure metadata updates are performed before moving onto the next steps of the workflow.
How does it work?
The basic premise is to create a variable to store the state, then use a Do Until loop to keep trying to update the item. If the update fails, execute a Delay and try again. If it succeeds, update the variable to exit the loop. The Run After conditions need to be set on both the Delay and the Set Variable. The Delay will run when the Update fails or is timed out, while the Set variable will run if the delay is skipped.
1. Initialize a Boolean variable and set it to False.
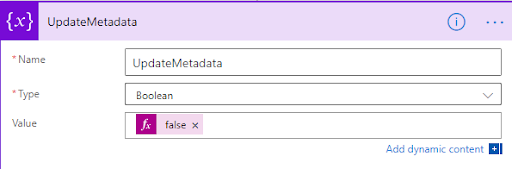
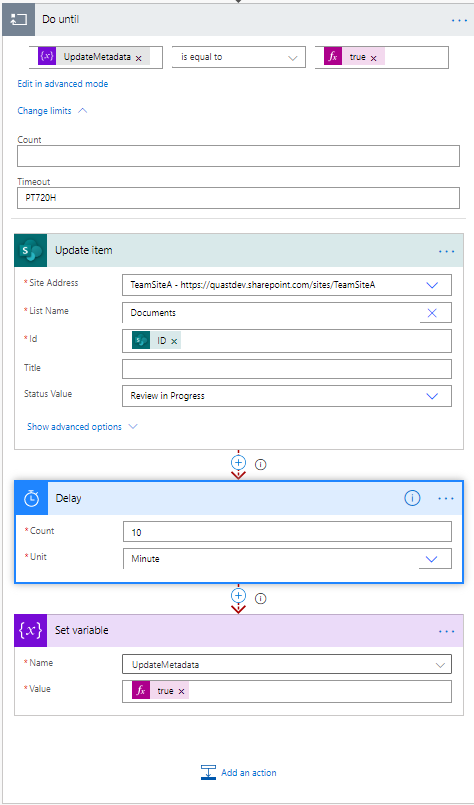
2. Create a Do Until loop to run until the variable ‘UpdateMetadata’ = True.
The Change limits configuration controls how long the Do Until loop runs, or how many times it tries before moving onto next workflow actions. I set timeout to PT720H, which is 30 days using the ISO-8601 duration notation, and leave count empty so it retries unlimited times.
Place your “Update item” or other action susceptible blockage within the Do Until. After the Update item, add a Delay action to configure how long you wish to wait between retries.
After the Delay, add a Set variable to flip the marker variable to True, indicating the update was successful and the loop can stop.
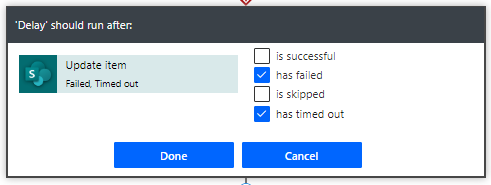
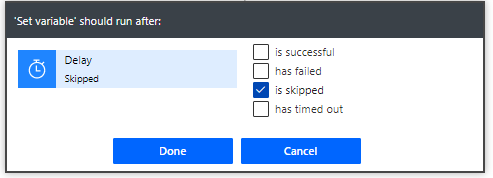
3. Configure run settings on ‘Delay’ and ‘Set Variable’.
If the Update is successful, the “has failed” and “has timed out” options will instruct the workflow to skip the Delay action and move onto the Set Variable.
Setting “is skipped” on Set Variable means it will only run if Delay didn’t, which would indicate a successful update.
Conclusion
In a shared environment, there is a good chance you will try to update a file while it is in use by others. When it’s a human being performing the update, the consequences are usually minimal — we just wait a few minutes and try again. When a workflow is blocked, it can cause downstream issues and leave data and files in an unexpected state. By adding some protection and retry logic around the updates, we can help ensure they are completed successfully before moving on to other tasks.
SEC Sweep Exam Priorities – Business ContinuityWatch the Full Webinar Presentation!
Marc Capobianco, EVP of FinTech at Thrive, John Stiles, Founder & CEO of C/Bridge Strategic Advisors and Michael Dale, CFO at Eastward Capital Partners discuss how financial firms need to review and update their business continuity plans to comply with regulators expectations.
Discussion Topics:
- Does the firm have policies, procedures, guidance or other information tailored to address the continuity of business operations during a pandemic?
- Has your firm activated its BCP in response to COVID-19?
- Does your firm’s BCP address the resiliency practices of third-party vendors, service providers and partners?
- How has your firm addressed cybersecurity policies and procedures regarding employee remote access?
- Does your firm have any specific limitations in its ability to operate critical systems and operations during the pandemic?
Fill out the form to get instant access to our on-demand webinar.
Trusted Advisors – Beyond Service Understanding and into Deal PositioningAs 2019 ended and 2020 began, the nationwide Channel continued its tremendous growth. Partners are more established than ever in their roles as trusted advisors and are increasingly adept at uncovering cyber security, Cloud, and a variety of other Managed IT opportunities. A greater overall focus on partner education has been a key contributor to this success with Master Agencies at the forefront — coming up with increasingly engaging and effective ways to prepare partners to win deals. However, as a supplier, it is important to note that the education cannot end there.
While partners receive enhanced educational benefits from an industry and general service perspective, one thing I have noticed is the push for suppliers to not only educate partners on their assorted services and products, but to go a step beyond. Yes, understanding the product suite is vital, but the true value is in understanding HOW to sell these services to your existing account base once you learn them. This is not a one size fits all approach and must be addressed uniquely. Thrive is making a push to provide more education to our partners beyond what we offer and how we differentiate in the marketplace. We aim to dive deeper into how to take this knowledge and position it through the right line of conversation with the goal being to find direct opportunity alignment.
A big piece of this additional education is helping our partners identify key market trends and build business cases around them, specifically as they relate to Thrive and our strengths. For example, organizations with a new IT Director or C-Level executive have proven to be the perfect candidates for a Network Health Assessment; a commissionable engagement run by our consulting team that helps businesses drive value by understanding where they need to invest from an IT perspective. In a broader example, we have seen more and more first time SIEM adopters. With our partners asking the right questions, a need was identified for smaller SIEM/SOC deals with under 100 devices that had previously not been a focus of ours. Partners now know to leverage Thrive on these opportunities as we have a strong SIEM offering.
While this is already about a paragraph too long, I think it’s important to emphasize the main takeaway here. Partners are becoming more educated and bringing better opportunities to the table. There needs to be a push to go beyond the ABCs of our services as suppliers and continue to build the deal positioning aspect. This requires a tailored approach that focuses directly on what we do best and helping partners leverage that.
We don’t expect to be picked for every given opportunity, but want to make sure that when we are, everyone wins.
For more information on Thrive’s Channel Program, CONTACT US TODAY!
Phish Out of Water — Remote Workers Email SecurityThe last few weeks have been a big change for everyone. Many people are working from home, and some of those people have children at home with them. Right now, my kids are wandering the house looking for breakfast and prepping for Zoom meetings with their teachers. While I have seen many acts of kindness and compassion during this time, I have also seen attackers take advantage of distracted workers who are trying to balance home and work life.
We have seen an increase in phishing emails that are shockingly good. They are playing on the fears of people working from home. For example, a receptionist who gets an email from the CEO asking to buy gift cards for everyone as a morale booster, might think this sounds great. In the past they would walk down to the CEO’s office and probably ask a question or two. But in today’s climate, without the easy access to the CEO, they might just buy the gift cards and send the information back via email, never realizing this was a phishing scam.
In this time of change, communication via Teams, Slack, etc. is essential to keep the ability to “pop” into someone’s office to ask a question. It is also imperative to implement or continue security awareness training — provide people the tools to be able to spot malicious emails and routinely phish your employees. If someone fails, that is a good thing. You can help that person before a hacker gets them to click on a link. Make it mandatory that they make time to take the trainings. Phishing and training together can really improve your security.
People are the weakest link in the security chain. Thrive’s Anti-Phishing and Security Awareness Training ensures your employees understand the mechanisms of spam, phishing, spear phishing, malware, ransomware and social engineering.
For more information, CONTACT US today!
Thrive Partner Testimonial – Blue Front Technology GroupThis video features Thrive’s Channel Partner — Dan Passacantilli, Founder of Blue Front Technology Group. Blue Front Technology Group has been a channel partner of Thrive’s for 15 years.
Agents and Technology Consultants partner with Thrive to leverage our technical expertise coupled with our NextGen managed services. Thrive is considered a trusted advisor that partners rely on to offer their clients NextGen Technology Services.
For more information on how to partner with Thrive, CONTACT US today.
Still not using 2FA/MFA? No time like the present to make the change!Has your remote work policy changed in the last month or two? Are more of your employees working from home or at locations that are “untrusted”? The answer is almost certainly a resounding YES! Now more than ever you need to ensure that Two Factor Authentication (2FA) or Multi-Factor Authentication is being used throughout your organization in as many places as possible. Many people are becoming more comfortable with this concept as they are having to perform these same steps to access their personal accounts (banking, Gmail, etc.).
Whether it is accessing your corporate VPN or cloud-based applications such as Office 365, Salesforce, NetSuite, Workday or many others you need to make sure users are required to supply two forms of authentication to access company resources and data. Something they know (username and password) and something they have (a text message with a unique code or an app on their phone that must be clicked to accept the request to connect) are no longer optional in the workplace.
Microsoft has a Multi-Factor Authentication product called Azure Multi-Factor Authentication that can be configured to deliver Two-Factor Authentication four different ways. The Azure Multi-Factor Authentication service can send you a text message with a code that you must provide, call you on a preset phone number and provide you with the number, provide a rotating code on the Microsoft Authenticator smart phone application, or push a pop up message to your smart phone for your approval. Azure Multi Factor Authentication is available as a standalone product and is also included in Azure Active Directory Premium, Enterprise Mobility Suite, and Microsoft 365.
Fortinet also has Two-Factor Authentication capabilities built directly into the FortiGate firewalls. A physical token or a smart phone application can be used to get a rotating code that can be used as the One Time Password when connected to a FortiGate SSL VPN.
In addition to 2FA, geography-based access to your corporate resources should be something that you consider implementing. Allowing someone to connect from any location in the world may not be necessary, when your users should only be coming from certain geographies. If you only operate business in the United States, why not block any connection attempt from international locations? Sure, you may have users that travel internationally from time to time and exceptions can be made as they arise. Reducing your attack surface in as many ways possible is the best course of action to protect your business now and into the future.
If you are interested in learning more about how Two-Factor Authentication or geography based restrictions could better protect your business, CONTACT THRIVE TODAY!
The Single Cause Behind Most Vulnerabilities and How to Solve ItHaving been involved in hundreds of vulnerability assessments I can confidently say that most issues have a single underlying source. The discovered vulnerability could be an increased risk of ransomware exposure, buffer overflows, elevation of privileges, denial of service, weak encryption, etc. Regardless of the diversity of the vulnerabilities, there is commonly a single deficiency within the organization that led to the risk. It is a crucial component of any solid cyber security framework, yet it remains one of the least appreciated and maintained areas of Information Technology. By now, you may have guessed, that I’m referring to patch management.
Inevitably, a vulnerability assessment will overturn workstations, servers, switches, firewalls, routers, wireless access points, hypervisors and countless other devices which all need to be patched. Consequently, the IT department is consumed with months of maintenance windows to get everything updated. After many late nights, every piece of infrastructure is finally fully patched. The IT department can finally get a good night’s sleep! Unfortunately, it won’t last long because while all of those patches were getting installed more vulnerabilities were discovered which will require more patching. This is the never-ending struggle of patch management.
It’s true that most IT departments have a pretty good handle on patching workstations and servers by leveraging automated patching solutions. However, that addresses only a small piece of the typical IT infrastructure. What’s a sleep deprived IT department to do to keep up with the tidal wave of patches? It’s simple, embrace Thrive’s NextGen services.
- Offload all server and hypervisor patching responsibility by transferring workloads to one of Thrive’s many cloud solutions.
- Deploy ThriveCloud managed firewalls, switches and wireless access points to allow for automated patch and firmware deployments during scheduled maintenance windows.
- Leverage Thrive’s 3rd party patching solution to update often overlooked and highly vulnerable software like Java, Acrobat and Zoom.
For more information on Thrive’s NextGen managed services, CONTACT US TODAY!
Remote IT & Security. Is your business and corporate data at risk?Overnight, the COVID-19 pandemic has permanently changed our approach to remote IT and security. We went from offices full of collaboration and activity to at home offices now exposing businesses and corporate data to increased risk. At Thrive, we hold a daily management meeting to review and discuss the implications of a remote workforce during this experience. Many organizations are following a similar protocol as well, and although it has taken some getting used to, it has shined a light on how well we are able to collaborate remotely.
Our president, Marc Pantoni, mentioned the other day on one of these calls that the focus at the beginning of the Work From Home period was stability but as it matures, many organizations will start to focus on risk management as they were during prior to this unplanned event.
Over the years, we’ve seen disaster recovery tests become quite commonplace but now we’ll start to see pandemic tests or WFH tests become much more prevalent. This isn’t fear mongering, it’s prudent risk management. I surmise that like many of you, my work from home plan was my laptop sitting on a home office desk or perhaps a kitchen table. My home office did not have all the trappings of my branch office. Over the last couple of weeks, I’ve gotten quite efficient at WFH and for many end users that environment is here to stay even once we all return to the office semi-full time.
Securing that location will now become a higher priority. For many senior leaders and high-tech workers, we will look to high value yet low effort solutions to protect the household. For years network security companies have added a feature to their devices that is not very widely used that can provide “clean” network connections. This function, usually called transparent mode, introduces unified threat management appliances into home networks without changing the overall topology of the environment. This means that we can add intrusion prevention and malware protection at the network level without the needing to swap out the consumer wifi solutions, which are very popular. Fact is, having malware on a home network is as big of a problem as it is on an office network regardless of where it resides.
To understand this concept a little easier, here’s a simple network diagram:

These solutions are extremely straightforward to setup and maintain as opposed to creating a branch office inside a home office. It allows for added protection of all devices on the network without the headache of redesigning the entire home network.
If you have questions or concerns about remote IT and security, Thrive is here to help. CONTACT US TODAY!
