By Ian Bowell, Head of Information Security – EMEA
Information security attacks continue to impact organizations around the world and there is no sign that the frequency, variety or scope of breach events will decrease any time soon. To meet the challenge of changing risks, a well-known standard in cybersecurity compliance has been recently updated, as anticipated for some time.
The ISO 27001 is the international standard for Information Security management from the International Organization for Standardization. Currently utilizing definitions from 2013 documents with updates in 2014 and 2015, it is the central framework for implementation requirements in an ISMS (Information Security Management System). Organizations can certify to ISO 27001 leveraging the management standard to achieve compliance. The new third edition of the ISO 27002 released in 2021 introduces a code of practice for security controls which compliments the requirements of ISO 27001.
The implementation, certification and compliance with ISO 27001 and 27702 present new opportunities for revenue growth. By aligning your data security with ISO standards, your organization stands out as operating according to international best practices. Investors, stakeholders as well as new and existing clientele can rest assured your organization’s data is secure using ISO standards.
To be clear, the ISO 27001 is the standard against which organizations are certified. ISO 27002 provides the supplementary detail for the selection, implementation and management of information security controls.
The differences indicate the new and updated ways in which an organization must address and manage information security in order to become ISO 27001 certified in the near future. Organizations must recertify every three years, with annual surveillance audits, allowing for a conversion period when a new standard is released. If the ISO 27002 results in a new recertification process in 2021 or 2022, organizations will have the option to recertify to the old 2013 standard allowing time to update the associated processes according to the new ISO 27002 controls. By 2024 or 2025 all organizations will be using the new standard, but those keen to update will do so much sooner.
The ISO works to ensure consistency across all their standards in different areas of business such as manufacturing, supply chain and financial services. If your organization has other ISO certifications such as risk management, financial management, etc., it is likely that those standards will update to condense older processes or add new requirements. The key to managing ISO certification is to address multiple standards with an interrelated consistent process to minimize repetitive or conflicting processes between updates.
As information security is one of the key business practices these days, and of great concern to modern businesses and their executive boards, it is not surprising that ISO 27002 leads the way to revision.
But enough of the context, and on to the controls themselves – what has changed?
Information Security controls are now in 4 categories:
Section 5. Organizational controls
Section 6. People controls
Section 7. Physical controls
Section 8. Technological controls
This significantly reduces the current 14 categories, and as noted above, provides more consistency and commonality with other ISO standards.
The total number of controls in ISO 27002 has reduced overall from 114 to 93 and sixteen legacy controls have been removed.
Reflecting the ever-changing cybersecurity landscape, twelve new controls have been introduced as follows:
- Threat intelligence
- Information security for use of cloud services
- Data leakage prevention
- Information deletion and data obfuscation, or masking, for privacy
- Business continuity readiness
- Identity management
- Physical security monitoring
- Endpoint security for user devices
- Configuration management
- Web filtering
- Secure coding
In a further development of the often-quoted CIA security properties of Confidentiality, Integrity and Availability, the new ISO 27001 details new attributes to ease classification and management. Controls are assigned a type such as Preventive, Detective, Corrective, with Information Security properties CIA as before.
Identify, Protect, Detect, Respond and Recover are used as key concepts for information security, and operational capabilities have been assigned as continuity, physical security, Information security event management.
At Thrive, we provide a defense in depth approach, with various products and layers of cybersecurity to address upcoming changes from the ISO. With many of these controls in place already, we look forward to matching our processes and controls to the newest standard.
There are many more details and the full document can be purchased from the ISO here https://www.iso.org/obp/ui/#iso:std:iso-iec:27002:dis:ed-3:v1:en
We look forward to doing so ourselves to further digest and apply the standard when we recertify. Whether the new standard will be available when we recertify ourselves in 2022 remains to be seen.
And thanks to Rushabh Mehta for the analysis of the new ISO 27002.
Get to Know Microsoft’s New Office Mobile AppThe new app delivers a more streamlined Office 365 mobile experience.
By Christian Wilmot, Client Technical Manager – EMEA
This month we are looking at the Microsoft Office mobile app. A silent but colossal game changer when working with Office 365 on iOS and Android devices.
With the expansion of cloud services, the demand for on-the-go secure access to corporate data has grown. And the Office mobile apps have been at the forefront, providing on the go access to Outlook, Word, Excel, PowerPoint, OneDrive and other apps across a plethora of devices.
However, document hand-offs between the Office mobile apps have been a challenging experience at best and, at times, excruciating. For example, the regular app switching, or when tapping to edit a document in OneDrive, being sent to the Word app only to find the document has not opened and having to switch back to OneDrive. Argh!
Access to the individual Office apps on mobile devices is excellent for alternative investment organizations that want to supply access only to specific applications via Intune. And when combined with conditional access security policies, Office 365 administrators have granular control but can sometimes result in a bloated company portal and complex user experience.

The Future of Mobile Office…
But now, another Microsoft mobile app has emerged. A Microsoft app forged in the deepest depths of Redmond (USA) with the sole purpose of transforming Office 365 mobile working forever. One app to replace them all… well, most of them anyway.
It is a mobile app that has snuck into the iOS and Android app stores with extraordinarily little fanfare. An app that reminds me of the late Steve Jobs’ words when describing iTunes on Windows. This, for me, perfectly sums up the new Office mobile app when working with the many and at times clunky Office 365 apps on mobile devices. ‘It’s like giving a glass of ice water to somebody in hell’. And the mobile app, which I believe is an absolute game-changer in the Office 365 mobile working field, is called… wait for it… Office.
https://www.microsoft.com/en-gb/microsoft-365/mobile

So, how does the Office mobile app differ from the other independent apps that make up the Office suite?
Well, for starters, the app aggregates the functionality of Word, Excel, PowerPoint, OneDrive, SharePoint and Forms into a single streamlined app. And if that isn’t enough, it also provides an array of practical features, particularly for alternative investment managers who need access around the clock.

Read more: Dive deep into Microsoft Planner.
OneDrive Look & Feel
When you first open the Office mobile app, you will notice the OneDrive centric feel. Thumbnails of frequently accessed documents are along the top with recently accessed files in a clear and scrollable list below. There is also a helpful folder tab in the top right-hand corner, which navigates to OneDrive and SharePoint, allowing navigation through your entire folder structures. So, there is no need to switch to the OneDrive or SharePoint Online mobile apps off the bat. Great!
Word Processing Made Easy
The Office app also provides editing functionality. For example, opening a Word document and tapping a sentence brings up the keyboard. And the microphone button, which offers transcription, works remarkable well. One of the best features is Read Aloud, which is baked right into the Office app. Tap the menu button, select Read Aloud, and the audio controls will appear, turning a lengthy word document into a personalized audiobook to listen to on the commute home. Asset managers who already use the independent Word app might think, ‘this is nothing new; all these features exist in the Word app.’ And you would be correct, but word processing in the Office app is a far richer experience and a lot more stable and convenient.
Image 5 768×617 1
Tap, Tap, Create!
When tapping the plus button at the bottom of the home screen, you will notice the ability to create new documents and forms, which save directly into OneDrive or SharePoint. Again, some might think, big deal, but the simplicity and lack of app switching is excellent, which saves alternative investment managers time while also ensuring secure environments.
Image 6
Who needs Apple Notes when you’ve got Sticky Notes?
For those that are familiar with Apple Notes, I would recommend trying the Microsoft sticky notes feature. This simple plain text editor is built into the Office app for ease of access and can be organized in OneNote.
https://www.onenote.com/stickynotes
Office Lens, the perfect photoshoot for your paperwork…
For the Office 365 veterans, Office Lens has been around for years. And when it was integrated into the OneDrive mobile app many moons ago, it was a feature I extensively used. For those who have not used it, in short, it allows you to take a picture of a document and, via software imaging, flattens the image, converts it to PDF and saves it to OneDrive. A fantastic tool for asset managers to easily track expenses, receipts, and invoices. And built into the Office mobile app for ease of use and access!
Actions
Office Actions are fantastic, and this tab I can only see expanding in functionality over the coming years. I will not go into each in detail and instead provide an overview.
Share Files – For those familiar with AirDrop on Apple devices, this feature provides similar functionality and allows you to pair the Office app and mobile device via Bluetooth to a laptop and send and receive documents up to 30MB. Perfect for moving a large image or video between devices.
Do More with PDFs – This collection of features, though it is in the initial stages, are excellent. From here, alternative investment managers can sign PDFs by scribbling a signature on the screen, streamlining approval processes. Of course, it does not provide the in-depth audit trails of products like DocuSign, but the functionality is great. It also allows the conversion of PDF documents to Word, a brilliant feature that works surprisingly well.
Simple and Secure
For organizations that use Intune for centralized Mobile Device Management, the Office mobile app can slip right into the company portal. It supports conditional access security policies, ensuring a consistent user experience across Office 365 and app protection policies, allowing the app to function in a containerized environment on mobile devices to secure corporate data. These security features are particularly relevant for alternative investment firms that are facing increased cybersecurity threats.
Conclusion
The Office mobile app is an excellent addition to the Microsoft mobile app offering. It provides a feature-rich environment, cutting down on application switching. It is the perfect tool for alternative investment firms that want to equip their workforce with a more streamlined Office 365 mobile experience. Since installing the Office mobile app, I’ve found myself working from my iPad and iPhone more, editing documents I would typically wait until I was in front of my laptop to work on.
So if you have not tried it yet, download the app today!
The Value of Modern Digital Transformation as a Fractional ServiceCompanies of all sizes can benefit from applying digital transformation concepts to their organization. But too often these modern services are delivered via an outdated delivery model that doesn’t fit the realities of the business.
Not long ago, consultants would design a large-scale solution for a defined problem or need. The organization would be left with a hefty bill and heavily built solution that hopefully provided some value. If even marginal improvements were seen, everyone declared victory and went on to the next big project.
This was not always a path small- and medium-sized businesses could – or should – take. Often, these businesses would purchase off-the-shelf software and services, and hope for the best. Both larger and smaller organizations incurred technical “debt” in the form of maintenance, aging software, updates, migrations, and service packs. Ultimately, their state-of-the-art solution became an aging, unviable one faster than expected.
However, the world has changed, particularly when it comes to accessing technology. Opportunities exist for organizations to gain value through digital transformation as a fractional service.
A Manageable Way to Achieve Digital Transformation
Access to “billion dollar” software was unheard for SMBs of just a decade or so ago. Today, a mid-sized company can sign up for Microsoft Office 365 with a credit card. For a relatively low monthly cost per user, state-of-the-art email, document management, workflow platforms, data visualization tools, and top collaboration tools are available. Setting up and configuring SharePoint was once a lengthy IT project in and of itself. Now it’s accessible with a few clicks.
At Thrive, we strive to help businesses solve problems and inefficiencies, replace paper-based solutions, and achieve digital reporting, visualization, and collaboration transformation. With lessons learned from the days of big projects, we view digital transformation as an ongoing process — one that will continue as long as the technology, people, and businesses change. The best way to address change is to align with it. We believe strongly that the ideal approach is to align the rate of change an organization can absorb with organizational needs, and adapt resources and plans accordingly.
For example, a typical digital transformation journey may involve one day each month of strategic planning and guidance, two days of training, three days of workflow development, a day of architecture and design for the upcoming efforts, and three days of reactive support and changes to existing solutions. This adds up to about 10 days a month, or one-third of what would normally be a single, full-time employee. Some months may require more development, and others more reactive support. It’s important to engage with a service delivery model that accommodates the needed flexibility.
Several factors make digital transformation as a fractional service significantly more effective:
- Adoption: A mid-sized business can only make, accept, absorb, and respond to a certain number of changes. Understanding that and building a cadence is key.
- Cost: A full-time consultant or employee can be expensive. If utilizing a full-time resource is difficult to fit into the budget, it may not be the best use of resources.
- Expertise: Assigning one person to a project can lead to a knowledge bottleneck. No matter how smart that person may be, they likely don’t have the breadth of experience that a whole team can deliver. Multiple people should be evaluating problems and collaborating on a solution.
- Single Point of Failure: People come and go from organizations, but operational needs will continue. A one-person team leaving for a new job can completely derail entire projects, especially at smaller companies.
The most important takeaway is to get educated on the modern capabilities digital transformation platforms provide, and start working on a model to make use of them.
Larger organizations with sprawling IT departments have had the advantage of awareness and education, with access to higher quality resources for many years. Now that smaller organizations enjoy access to the same technical resources, they have an advantage in digital transformation through their agility and flexibility, but need the right partner to get the most of these resources. The message is clear, though – organizations of all sizes can modernize IT infrastructure through fractional digital transformation, and Thrive can assist with yours.
Maximizing Your Microsoft InvestmentDigital transformation is not a one-time project, and does not occur overnight. It’s a continuous process that changes as technology evolves and organizational needs develop.
Thrive offers tailored solutions, with a focus on bringing end users into the equation, to drive long-term success for organizations. Our Office 365 Center of Excellence (CoE) is a managed services solution that understands moving targets and changing goals. When utilized properly, clients discover Office 365 improves productivity and maximizes their investment.
Leveraging the Digital Tools at Your Fingertips
A business assessment is the first step to understanding how to best leverage the power of Office 365. Is a basic business license enough, or should a more advanced license be used? How many employees use the products, and are they in the office or remote? Everything should be taken into consideration during the assessment workshop, as we gather key stakeholders and show opportunities for improvement on the road to digital transformation.
When devising a governance plan, guidelines, policies, and processes should always align with the vision and business roadmap. However, this roadmap alignment is not always carved into stone, and changes will occur. Opportunities arise to revisit the roadmap, implement feedback from end users, and make feature additions or software changes as new technology is released or business needs evolve. Your governance plan should account for this evolution.
A defined strategy and governance plan sets the stage for a proper architecture to be put in place. This architecture includes which Office 365 tools will be in use, aligning the necessary applications with strategy and governance, and ensuring the proper design and delivery with customization and configuration.
At Thrive, we seek to create a long-term, consultative partnership with clients, working in a manner that allows for roadmap revisions and reorganization when needed, while delivering value at every stage.
Best-in-Class End User Support Training
Targeted training prepares end users and gives them the ability to fully utilize Office 365 products. While generic training videos may explain general ideas and concepts, they don’t always meet the end user where they currently are. Thrive assembles training on common threads of how tools work based on governance policies, with custom materials designed around specific needs.
Thrive also supports multiple ways to complete the training. In the past, in-person training was a popular option (which will hopefully return in the future), along with Microsoft 365 learning pathways, a customizable training experience with step-by-step learning modules. If governance policies require revisions to the solution, training can be adjusted as needed, helping end users understand the full scope of new offerings.
Over the years, we have seen the bloat that comes with adopting new tools and programs from various providers, requiring administrators and IT staff to be experts on several platforms. This can, of course, also mean extra licensing fees and require further coordination among all users to achieve a desired end result. Thankfully, Office 365 centralizes many offerings for the user and the IT staff. For instance, OneDrive’s interface is similar to SharePoint, enabling users to become accustomed to a platform more rapidly, and to share documents and information more easily.
The Office 365 platform will continue to develop and evolve as time goes on. We will assist with integrating enhancements and new platform features as they become available, keeping your organization on a trajectory that ensures your digital transformation has ongoing impact. For more information about maximizing your Microsoft investment, get in touch with the Thrive team today!
How Thrive Ensures Client SuccessA managed services provider should be both an innovator and an advisor, helping to set the stage for its clients’ business growth and success. Thrive’s best practices and proven engagement model ensure our clients’ IT infrastructure is well-managed, secure, and highly performant. By consistently delivering the best possible customer service experience, the Thrive team has become trusted partners for our emerging, mid-market, and enterprise clients.
To ensure client success, Thrive brings together the people, processes, and platforms that businesses need to succeed, making us valuable partners for our clients up and down the East Coast.
Our Customer Account Management Model
Our Customer Account Management, or “pod” model, includes virtual CIOs, Principal Consultants (PCs), Client Engagement Managers (CEMs), and Account Executives (AEs). When clients call, they speak to a well-versed team member assigned specifically to the account. There’s no need to wait around for a response, as we provide managed services coverage 24 hours a day, 7 days a week.
Industry-Specific Knowledge
We’re proud to assist organizations across the business spectrum, to strategically implement IT infrastructure that meets industry-specific demands.
We serve leaders in several sectors, including:
- Financial services
- Life sciences
- Healthcare
- Education
- Retail
- Legal
Most importantly, we track the latest government, security, and related regulations to ensure clients have comprehensive protection and a tailored cyber security plan.
The Thrive Platform
Powered by ServiceNow, the Thrive Platform is a comprehensive IT service management resource. Not only does this platform automate previously manual tasks, but it also informs decisions and educates an entire workforce. When logging in to the platform, clients can see the latest system news and status reports, access product sheets, and learn about the latest trends in IT through our blog posts.
The platform also includes a full training library, which helps align an entire organization’s IT and cybersecurity operations, limiting end user downtime and business disruption.
NextGen and Traditional IT Services
Thrive’s NextGen managed services accelerate any IT program, optimizing business performance and future-proofing digital infrastructure in the process. Managed Cloud, cyber security, and disaster recovery offerings bring clients into the 21st century and help them prepare for future growth.
Of course, our traditional IT services, which include hardware and software, server infrastructure, and office firewalls, also provide a level of customization for clients. With each service, we leverage the latest technology to deliver the most beneficial solution for each client’s needs.
Our Mission – Serving Clients Every Day
Over the years, we’ve built a corporate culture around client success, which drives us every day. We are constantly evaluating, building, and delivering the best IT solutions to our clients, and staying up to date with the latest trends in the marketplace.
The dedicated engineers and team members on our staff are committed to serving the needs of Thrive’s clients and have a passion for knowledge that informs their decision-making.
We strive to deliver an engaging and welcoming client experience every day. Get in touch with us to learn more about our services and see how we can transform your IT infrastructure.
Game Changer: Why CISSP Cybersecurity Certification Is Strategic for Organizations and IT ProfessionalsBy Ian Bowell, Head of Information Security – EMEA
According to PwC’s 2021 Global CEO Survey, 47% of CEOs identified cybersecurity as the top threat to their organizations’ growth prospects—up from 33% in 2020. This concern reflects the escalating frequency, complexity, and financial impact of cyber attacks and also the critical shortage of cybersecurity talent needed to meet those challenges.
IT decision-makers face the daunting task of finding security professionals with the right mix of skills and experience to protect their organizations. In response, many are turning to cybersecurity certifications—particularly CISSP (Certified Information Systems Security Professional)—to identify high-impact security talent.
CISSP can also be a boon to security professionals, helping them deliver improved job performance while creating opportunities for career advancement and higher compensation.
CISSP — The World’s Premier Cybersecurity Certification
CISSP is a certification offered by the International Information System Security Certification Consortium—(ISC)2. With almost 148,000 members worldwide, CISSP-holders are globally recognized as having the skills and experience to design, implement, and manage high-performance cybersecurity programs.
CISSP takes a comprehensive approach to certification. Applicants must possess the equivalent of four years of cybersecurity experience, receive an endorsement from an existing (ISC)² credential holder, and complete an ongoing 120 credit education program over three years to retain their certification.
Assurances for the C-Suite
With the average cost of a cybersecurity breach in the financial sector pegged at $5.1 million, C-level executives are prioritizing security programs and infrastructure to reduce their risk. But talent is a problem; demand is high for experienced, certified security experts, with an estimated 3.5 million unfilled cybersecurity positions in 2021.
While organizations must compete hard for security talent, executives need assurances that potential hires have the experience, skills, and ‘growth mindset’ to meet the challenges of a rapidly-evolving cybersecurity landscape.
CISSP certification helps provide those assurances. Forbes found that 96% of IT leaders surveyed believed team members with cybersecurity certifications add value to their organizations. And according to Brad Puckett, Global Product Director for Cybersecurity at Global Knowledge, “Any organization with sensitive critical infrastructure and assets will look to the CISSP as a staple when screening prospective candidates for open cybersecurity leadership positions.”
An Important Differentiator for Security Pros
Certifications like CISSP are also critical for cybersecurity professionals to accelerate their career development. According to the Global Knowledge 2020 IT Skills and Salary Report, more than half of survey respondents had at least one cybersecurity certification. As well, those certifications were associated with the highest IT salaries globally. “The top-tier cybersecurity certifications validate professionals for jobs in cybersecurity senior leadership positions, which are among the highest in-demand,” says Global Knowledge’s Puckett.
CISSP—Meeting the Demands of the Changing Security Landscape
The CISSP program is broken down into eight knowledge domains that continually evolve. Each update, issued every three years or so, brings changes that address technology advancements, escalating security threats, and new compliance requirements.
Asset Security
This domain details the physical requirements of information security.
The most significant change in this domain reflects the evolution of the General Data Protection Regulation (GDPR) standard since the privacy legislation was improved. CISSP certification now extends beyond data and system ownership into a complete set of GDPR terms for data processor, custodian, user, and the all-important privacy-protected data subject.
This section also acknowledges the rising significance of digital rights management covering ownership of data. This topic is now even more important with the rise of non-fungible tokens (NFTs) in the blockchain world and other digital assets of value, like the first tweet by Twitter’s founder, recently auctioned for charity.
Security Architecture and Engineering
Addresses several important information security concepts, including secure engineering design, mitigating system security vulnerabilities, and designing and implementing physical security.
The updated CISSP certification reflects advances in standard procedures (also raised by regulatory bodies) for Zero Trust, Least Privilege, Separation of Duties, and Two-Person Control. It also covers the Defense-in-Depth concept extensively utilized by Thrive TG to ensure that no one security layer is a single point of failure. If a failure or breach does occur, then another layer, vendor, or source of authority will pick up the attempt and prevent it with appropriate logging and analysis. Defense-in-Depth also includes the concept of Fail Securely, whereby if one layer fails, then systems fail to a secure state.
This section of the certification now also contains nearly twice the material covering various forms of cryptographic attack and their definitions, as well as quantum computing’s potential capacity to defeat current encryption.
Communications and Network Security
Focuses on the design and protection of an organization’s networks.
This section includes expanded coverage to reflect the increased relevance of wireless and cellular systems in communication and network security. CISSP now covers Wi-Fi Protected Access 3 (WPA3) in Wi-Fi networks and further deprecating WPA, along with the previously-addressed Wired Equivalent Privacy (WEP). Also highlighted is how WPA3 uses a Simultaneous Authentication of Equals (SAE) with Advanced Encryption Standard (AES) cryptography.
Other communication networks now included are:
- Zigbee for IoT, hinting at the rising security concerns for industrial complex OT (Operational Technology security considerations)
- 5G together with existing 4G
- Satellite communications, although Starlink internet as developed by SpaceX is not yet explicitly mentioned
Also covered is the rising use of Content Delivery Networks (CDN), essential for responsive proximity and static content distribution (images, videos, podcasts, and more) on the internet and social media.
Surprisingly, the list of standard ports has not changed to accommodate the increase and standardization of SFTP (SSH File Transfer Protocol) on port 22 and elsewhere across financial institutions, counter-parties, and others.
Identity and Access Management
This domain helps security professionals understand how to control the way users access data.
This section’s changes reflect a marked increase and open standardization on Security Assertion Markup Language (SAML), OpenId, and OAuth. These protocols are used for cross-entity federated authentication that simplifies single sign-on for corporate credentials and Google accounts while addressing some of the past credential leakage issues. New access control definitions also expand to include rule and risk-based access control, joining role-based access control (RBAC) with attribute-based access control (ABAC).
Security Assessment and Testing
Addresses the design, performance, and analysis of security testing.
This section has updated coverage of SSAE16 to SSAE18, and SOC audits for regulatory considerations, but no other notable changes.
Security Operations
This domain details the way security plans are implemented and optimized.
The Security Operations section remains little-changed compared to the other domains. Future changes should include more detailed coverage of newer forensics or cloud-influenced processes in this area, particularly in light of Security Orchestration, Automation & Response (SOAR), and evolving ransomware attacks with robust responses.
Security and Risk Management
CISSP’s largest domain, Security and Risk Management, provides a comprehensive overview of security and information systems management.
There are no significant changes of note in this section. Thrive TG’s CISSP experts are monitoring the certification requirements for any upcoming developments.
Software Development Security
Helps professionals to understand, apply and enforce software security.
While this large section could be considered a discreet career path, it incorporates minimal changes at this time. Other available certifications have a greater focus on privacy or security-by-design, as mandated by GDPR or other considerations.
ISO 27001 and related certifications will continue to evolve, as a renewed ISO 27001 standard was expected in 2020. We also anticipate a new version of the Information Technology Infrastructure Library (ITIL), ITIL 4.
Security and the Human Factor
Deloitte calls the ‘human factor’ a critical element in “reducing the widening cyber risk gap and enabling organizations to capture the full promise of new technologies.”
Eager to close that gap, many C-level executives are leveraging CISSP as a strategic resource to identify the talent they need to protect their organizations’ systems, data, and infrastructure.
________________________________________
The insights into the additions and improvements to the CISSP program domains are provided by Ian Bowell, EMEA Information Security Manager at Thrive Technology. These perspectives reflect the overall change in focus and priority by CISSP. Please note that CISSP will be launching updated material in May 2021
Contact us for more information about Thrive Technology’s cybersecurity offerings, or to learn more about cybersecurity best practices.
Meet FinTech Compliance Mandates with Thrive’s Tailored IT PlatformFinancial services firms have an abundance of responsibility and challenges when it comes to information technology. Thrive’s FinTech Platform helps organizations manage and solve those IT challenges while also maintaining industry compliance mandates.
Through decades of experience and knowledge of the industry, Thrive utilizes SEC, FINRA, and SIPC guidances, risk alerts, and observations when developing an actionable IT and cyber security plan. Furthermore, Thrive is the ideal partner to assist alternative investment firms to evolve beyond on-premise architectures and capitalize on the compliance-friendly Cloud.
The On-Premise Model Shifts
Historically, emerging Cloud architecture has given organizations pause. However, the on-premise model is becoming unsustainable and COVID-19 is exponentially accelerating that process. During the last year, I’ve talked to financial services organizations with a server cabinet in the office who had to spend support time on physical infrastructure and server issues. Others have required upgrades to VPN licenses or requested more bandwidth to ensure efficient remote access. That time and money would have been better spent developing a future-proof Cloud architecture.
Rather than investing in aging infrastructure, it makes much more business sense to leverage Thrive’s Hybrid Cloud Director to pivot workloads to a Cloud environment. For instance, an organization may have training applications or a portfolio system that need to be in the private Cloud, whether for cyber security reasons or performance reasons. However, there may be other applications housed with a Cloud Service Provider (CSP). The all-or-nothing approach does not apply to modern Cloud computing where everything must be in a public Cloud such as AWS or in a private Cloud. Thrive has built the FinTech Platform to move workloads between a public Cloud and Thrive’s private Cloud infrastructure, and it’s all done seamlessly in a frictionless, compliance-friendly manner.
Compliance Solutions Through the Thrive FinTech Platform
When new SEC and FINRA regulations are announced, Thrive’s Account Management team is in contact with clients to confirm they understand any compliance changes which are relevant to their business. Thrive’s Service Delivery Engineers specialize in financial services applications and are well aware of their critical impact to your business. Senior Principal Consultants, meanwhile, provide advisory services and consult clients on a regular basis to discuss potential risks while developing infrastructure recommendations.
With a steadfast commitment to maintaining customers’ compliance and cyber security postures, Thrive understands the need for ongoing communication and partnership. As such, we create an annual roadmap to inform customers of the following:
- The state of their IT infrastructure
- What peers in the industry are doing
- Recommended investments in their IT infrastructure.
Thrive’s FinTech Platform manages the full investment lifecycle, while our private Cloud platform delivers enterprise-grade service from multiple SSAE 16 SOC 2 data centers. Learn more about our FinTech Platform and what we offer to alternative investment management and hedge fund communities.
Deep Dive into Microsoft PlannerHow the Newest Task and Project Management Offering from Microsoft Office 365 Can Simplify Your Business
So, what exactly is Microsoft Planner?
Microsoft Planner can enable your firm to organize projects, centrally assign tasks to individuals, set priorities and deadlines, and provide teams with instant progress updates via dashboards. To make life easier there is an iOS and Android app for mobile and tablet devices alongside integration with Microsoft Teams.
Accessibility and Benefits
Third-party project and task management tools come with a price tag requiring integration and an increased cloud footprint. For organizations already taking advantage of Office 365, Microsoft Planner is ready to use with no additional costs or integrations dependent on subscriptions. As part of a subscription, Planner data can be automatically secured inside the Office 365 tenant and protected by an organization’s existing in-place security controls.
Advanced Task Management
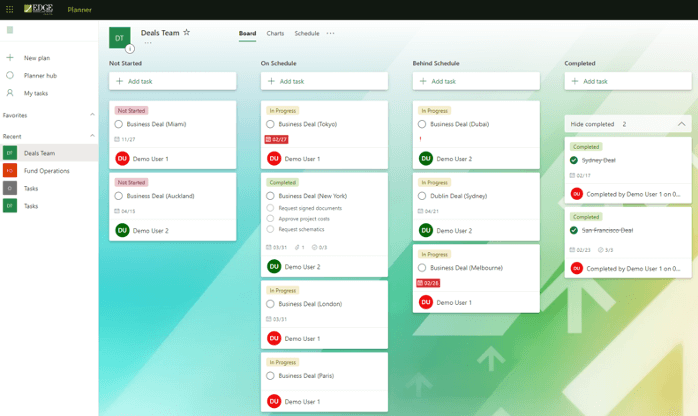
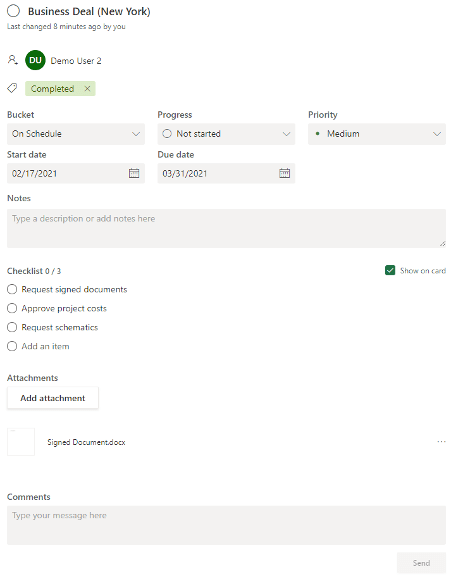
Planner understands a completed task is much more than just a tick in a box by offering a simple but enhanced visual approach to teamwork logistics.
Upon creating a task, owners and allocated team members have access to Kanban style boards with buckets and swim lanes allowing employees to set priorities, check project status and achieve deadlines. Checklists and note fields can be created within a task to ensure all steps are completed start to finish including time tracking to better understand and analyze project duration. Dashboards and notifications can be accessed from any devices ensuring your team is up to the minute.
Teams Integrations
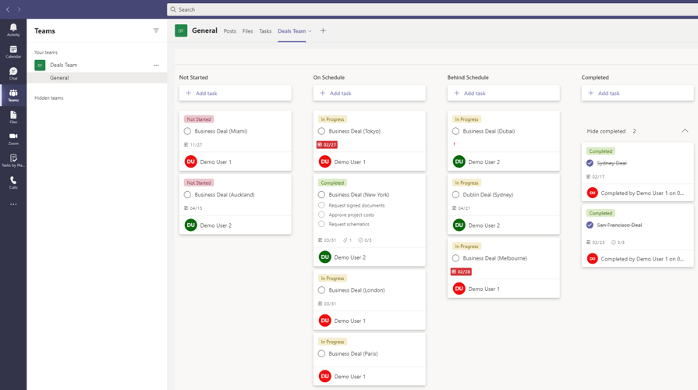
Teams is at the forefront of Microsoft collaboration and provides integration across the Office 365 technology stack.
Integrating Planner with Teams is quick and offers the same browser-like experience so your team does not have to break focus by application switching. Planner can be accessed alongside Teams channels and Office 365 group resources including OneNotes providing quick access for setup and use.
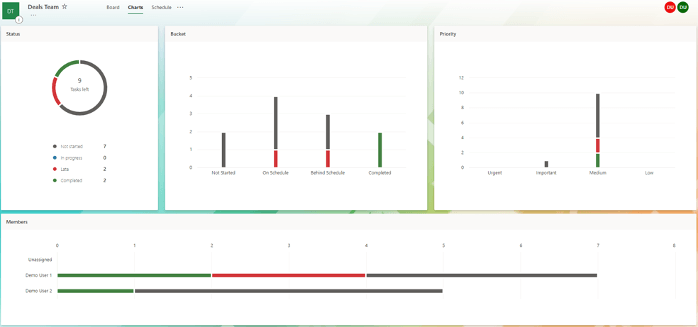
Dashboards
Project managers often need a quick snapshot of a project status to report back to senior management and dashboards are the answer. Easy access to real-time data will inevitably give way to increased efficiency from team members. Planner provides preconfigured dashboards out of the box, ensuring team members are always on the same page… or dashboard.
Conclusion
Microsoft Planner is a great tool for any organization with an existing Office 365 subscription looking for a quick and efficient way to manage projects. For now, the task and project management market leaders are still the likes of Asana, Trello, and Microsoft Project. Microsoft Planner is an upcoming and worthy contender in the collaboration and task/project management space.
Why not have a look at Planner today?
Microsoft Exchange Server Attack: How Thrive Is Responding
The recent attack on Microsoft Exchange Server by Chinese hacking group, Hafnium, has affected thousands of organizations across the country in a brief period of time. Microsoft announced news of the attack on March 2nd, and immediately released urgent patches in an effort to defend against further attacks.
Microsoft detected zero-day exploits used to attack on-premise versions of Microsoft Exchange Server. These vulnerabilities allowed threat actors to access email accounts and install malware to gain long-term access to these environments.
Thrive has responded quickly to assist clients affected by this attack, and will continue to support them in the coming weeks and months ahead.
What Happened with the Hafnium Attack?
Chinese hackers, known as Hafnium, began exploiting Microsoft Exchange servers in early January. These hackers stayed in stealth mode until early March, when Microsoft urged Microsoft Exchange Server users to patch Exchange systems as quickly as possible.
After the announcement by Microsoft, Hafnium switched from stealth mode to a more aggressive scanning of servers across the globe, looking for vulnerabilities. Soon after, additional hacking groups (now believed to be upwards of 10) began exploiting vulnerabilities on servers in over 100 countries.
By accessing servers, hackers were able to:
- Access other systems within an environment
- Exfiltrate data
- Install malware
- View sensitive and proprietary information, including intellectual property (IP) and personal identifiable information (PII)
How Thrive Has Responded
Thrive has worked diligently to assist companies impacted by this recent attack, proactively deploying Thrive’s Endpoint Detection and Response into these environments. As a precaution, Thrive also used advanced endpoint detection to allow our teams to better analyze, diagnose, and prevent future malicious activity.
Meanwhile, our engineering team has worked around the clock to initiate recommended Microsoft and cyber security best practices. Engineers applied the latest patches and scripts to client environments, following Microsoft’s guidance.
Finally, Thrive has also hired a consulting firm to validate that all steps were taken to implement patches properly. We did so in a proactive manner to ensure all processes and precautions were followed.
Next Steps to Take
We highly recommend migrating off of dated legacy platforms and implementing Thrive’s End-User Cyber Security Bundle, which provides several layers of protection for your end users.
This bundle should include:
Endpoint Security & Response
- Thrive’s Endpoint Security and Response service provides Next Generation malware detection & protection for servers and workstations.
- With the advent of sophisticated malware such as file-less attacks and zero-day executables, a feature-rich signature-less endpoint solution is needed in many organizations.
- Our solution offers all of the necessary features to combat advanced endpoint attacks while meeting multiple compliance guidelines that typically require traditional antivirus protection.
Advanced Email Threat Security
- Email Gateway, Advanced Security, and Data Leak Prevention
- Virus and spam protection
- DNS authentication and advanced reputation checks
- Multi-layered malware protection against known and zero-day threats
- URL re-writing with on-click scans to block malicious URLs in email and attachments
- Sophisticated protection against social engineering, homoglyph/homograph deception, and impersonation attacks
- Analysis of internal and outbound URLs, attachments, and DLP checks
- Continuous rechecking of files for malware
- Threat dashboard showing cyberthreats relevant to your business
- Remediation of malicious or undesirable mail controls
- Signatures, disclaimers, watermarking, metadata scrubbing
- Content Examination and Data Leak Prevention (DLP) for inbound and outbound mail
- Easily detect sensitive and confidential information in emails
- Mailbox Continuity and Data Recovery
- Uninterrupted access to live and historic email
- 365-day email retention period
- 100% SLA on email availability
- Comprehensive continuity event management through service monitors and alerts
- Rapid recovery and restoration of mail, folder, calendar, and contact data
Secure Internet Gateway
- Thrive’s Secure Internet Gateway (SIG) service is a Cloud-delivered security service that brings together essential functions that you can adopt incrementally, including:
- Secure web gateway
- DNS-layer security
- Cloud-delivered firewall
- Cloud access security broker functionality, and
- Threat intelligence.
- Deep inspection and control ensure compliance with acceptable-use web policies and protects against internet threats
- Accelerated threat detection/response and centralized management makes it ideal for decentralized networks
Security & Awareness Training
- Thrive Security Awareness Training (SAT) ensures your employees understand the mechanisms of spam, phishing, spear-phishing, malware, ransomware and social engineering using training materials and targeted user campaigns aimed at improving awareness of and response to security threats.
- Integrates with Active Directory
- Branded Phishing messages
- Leverage a library of Standard and/or ‘build-your-own’ Custom email templates
- Customize intervals and groupings of campaigns and target employees
- Curriculum Builder
Lastly, strengthening the cyber security posture of Cloud and on-premises is crucial. Thrive can provide forward-thinking solutions to protect your important information, including intellectual property and other sensitive data that amount to your crown jewels.
The Push to Evolve: Why Law Firms Need Cloud Computing to CompeteLaw firms have often had to bridge a digital divide in handling clients, cases, documents, employees, and more. Now, challenging IT issues like remote work, cyber security, application management, privacy regulations, and data governance have only made it more difficult to remain technologically sound. Yet there is a tremendous opportunity for firms to transform their operations by taking advantage of all that the Cloud has to offer.
At Thrive, we leverage advanced technology to help bring law firms into the 21st century, moving critical applications to the Cloud Workspace and modernizing their IT infrastructure without complicated employee retraining or upscaling. The Cloud also gives law firms the agility and flexibility to not only easily modernize technology, but gain a competitive advantage, because they can seamlessly transition to new practice management software or add cutting-edge collaboration tools that boost efficiency and improve service.
For law firms, the time is now to go all-in on Cloud computing.
Leveraging Thrive’s Robust Cloud Platform
In our experience, most law firms are operating with an IT infrastructure that requires better redundancy, higher levels of security, and remote access. On-premise servers, which require maintenance, a proactive approach, and backups, can lead to IT headaches.
On-premise servers also limit employee productivity to a single desktop or laptop. Without Cloud-enabled virtual desktops, firms can’t empower their teams to succeed in the fast-paced legal world, which largely requires courthouse trips, off-premise meetings, and on-the-go communication.
Deploying a Cloud environment also means debunking some myths perpetuated about access and security.
Myth #1: If I’m in court and the internet is lagging, I can’t get to data.
Reality: Access to applications is available 24/7 from compatible devices. Anyone can work from anywhere.
Myth #2: I don’t trust the cloud.
Reality: The Cloud is highly reputable. Thrive Cloud, our private Cloud service, is hosted in a SOC 2 Type II-certified data center. Building a Cloud platform from the ground up protects valuable client information, going well beyond the entry-level office firewall and providing the ability to encrypt data in transit or at rest.
Reducing Complexities While Gaining Workplace Flexibility
For firms with just one office or a small team, an on-premise server, while outdated, may get the job done. However, an on-premise server is not compatible when satellite offices or remote computing are introduced into the equation. Perhaps a firm has two locations and each has its own server – suddenly, the IT team must manage a disjointed environment, which acts as two separate firms. A clunky, legacy VPN only adds to the frustration.
With remote workforces increasing in prevalence, security is another critical topic of conversation. Recently, a client learned their insurance provider would not renew their cyber policy unless they upgraded endpoint detection and response solutions on each of the firm’s computers. Thrive’s Endpoint Detection and Response protects firms by offering real-time, automated security across all devices – in the office, at home, and on the move.
Thrive’s Cloud Desktop as a Service (DaaS) platform optimizes performance and cost, while providing access to multiple Hybrid Cloud platforms, all managed by our experienced team of engineers. Moving both SaaS-based and legacy applications to the Cloud keeps everything aligned, even when legacy applications aren’t yet ready for that next level of performance. When legacy applications do evolve or become SaaS-based, they can be removed, making way for the newest SaaS-based option.
Law firms can control costs while improving security and resiliency with a Cloud solution, and gain peace of mind knowing important legal applications will be available when they need them most. The knowledgeable team at Thrive is here to help your firm make the move to the Cloud.
