Generative AI is revolutionizing industries. From its ability to generate text, images, code, and insights at scale, AI promises significant business value. But there’s a critical dependency that often goes underappreciated: data.
The quality, quantity, and diversity of an organization’s data directly determine how effective generative AI models can be. Without reliable data, organizations may experience inaccuracies, biases, and operational risk, potentially compromising the very benefits AI promises.
Why Data Matters for Generative AI
Generative AI models learn patterns, relationships, and context from vast datasets. The better the data, the more accurate and relevant the outputs. Data limitations, on the other hand, can lead to:
- Inaccurate Outputs: Models trained on incomplete or outdated data may produce results that mislead decision-makers.
- Bias and Ethical Concerns: Skewed datasets can reinforce stereotypes or produce unfair results, damaging brand trust.
- Reduced Reliability: Poor data quality leads to outputs that are inconsistent or unpredictable.
- Operational Risks: Inaccurate AI results can affect automated workflows, decision-making, and customer interactions.
Generative AI cannot outperform the quality of the data it learns from, meaning businesses must take measures to ensure they have high-quality data before implementing AI throughout their organization.
Key Data Challenges for Generative AI
- Data Quality: Even large datasets are useless if the information is inaccurate, incomplete, or inconsistent. Quality issues may include missing values, outdated information, duplicate records, or formatting errors.
- Data Diversity: AI models are only as inclusive as the data they see. Limited or homogeneous datasets result in outputs that fail to account for different customer segments, markets, or languages.
- Data Privacy and Compliance: Sensitive data may be restricted under standards like GDPR, HIPAA, or PCI DSS. These limitations can reduce the amount of usable training data and require careful governance.
- Data Accessibility: Data siloed across departments or legacy systems is difficult to consolidate for AI training. Generative AI relies on integrated, well-structured data pipelines to maximize effectiveness.
How Organizations Can Address Data Limitations
- Invest in Data Quality: Clean, validate, and standardize datasets to ensure reliability and accuracy.
- Expand Data Sources: Aggregate structured and unstructured data from multiple systems to increase volume and diversity.
- Implement Governance: Define policies for secure, compliant, and ethical use of sensitive data.
- Monitor AI Outputs: Track performance and bias to catch issues stemming from poor data.
- Break Down Silos: Integrate data across departments to create comprehensive datasets for AI training.
Organizations that proactively address these challenges improve model accuracy, reduce risk, and unlock the full potential of generative AI.
The Business Implication
For business leaders, understanding the limits imposed by data is critical. Generative AI offers enormous potential, but without high-quality, diverse, and accessible data, AI outputs can mislead decisions, perpetuate bias, or create operational inefficiencies. Addressing these data constraints is not just a technical issue; it’s a strategic business priority.
Generative AI is only as powerful as the data behind it. By investing in data quality, diversity, accessibility, and governance, organizations can overcome these limitations, unlock new insights, and drive real business value. Businesses that fail to address these constraints risk wasted AI investment, operational inefficiencies, and reputational harm. Contact Thrive today to learn more about how we can help you implement AI effectively and efficiently.
Thrive and HPE’s Guide to Cloud StrategyDownload Thrive and HPE’s Guide to Cloud Strategy to help you navigate what’s next. Whether you plan to stay on VMware, shift to a hybrid model, or explore alternative cloud strategies, this guide will help you determine the smartest path for your applications and your business.
With expert insights from Thrive’s managed services specialists and HPE’s cloud technology leaders, this guide gives you the clarity and recommended actions you need to take control of your future, before VMware changes take control of it for you.
Download the guide today!

Avoiding the frightful mistakes that can derail your AI journey
Every October, the world fills with ghosts, ghouls, and jump scares, but nothing chills an organization faster than a failed AI initiative. Bad AI planning can haunt your business long after the project ends, draining budgets, wasting time, and leaving teams wary of innovating again.
Artificial intelligence holds incredible promise, but like any tool, it requires the right foundation, strategy, and governance. Without them, organizations can stumble into costly traps that lead to poor outcomes or even cybersecurity nightmares.
The Curse of the Undefined Use Case
What happens: Organizations rush to “do AI” without clearly defining what they want it to accomplish. They implement tools or automation features without aligning them to business outcomes.
The result: Disconnected initiatives, wasted investments, and frustrated teams.
How to break the curse: Start with business value, not technology. Identify where AI can make a measurable impact for your organization, whether improving efficiency, reducing risk, or enhancing customer experience. Thrive helps clients pinpoint high-value use cases through discovery workshops and data assessments, ensuring every project starts with purpose and clarity.
The Zombie Data Problem
What happens: AI models are only as good as the data they’re trained on. In many organizations, that data is outdated, incomplete, or siloed, essentially “undead” data that won’t produce real results.
The result: Inaccurate predictions, unreliable outputs, and eroded trust in AI systems.
How to survive: Build a modern data architecture that ensures data is accurate, secure, and accessible. Thrive helps businesses modernize their data environments and implement governance frameworks so AI models are powered by living, high-quality data, not data zombies.
The Web of Shadow AI
What happens: Teams start experimenting with generative AI tools and automation platforms without IT or security oversight.
The result: Sensitive data leaks, compliance violations, and an expanding attack surface.
How to get untangled: Implement clear AI usage policies and monitoring tools to manage access and mitigate risks. Thrive’s Managed AI Services provide support to ensure all AI use, from automation bots to generative assistants, aligns with your organization’s IT policy and security standards.
The Budget Vampire
What happens: AI projects begin small but quickly spiral into resource-intensive efforts without measurable ROI.
The result: Overspent budgets, hidden infrastructure costs, and leadership losing faith in the technology.
How to drive a stake through it: Establish clear KPIs and milestones before launch. Thrive helps organizations align technology investments with business outcomes, ensuring AI initiatives deliver ongoing value, not ongoing costs.
The Path to AI Success
Good AI planning doesn’t happen by chance – it’s the result of strategic alignment, strong governance, and the right partners.
Thrive helps take the fear out of AI adoption. From defining use cases and securing your data to implementing compliant, outcome-driven solutions, Thrive helps organizations harness AI responsibly and effectively. Don’t let bad AI planning come back to haunt your business. Contact Thrive today to get started on building a smarter, safer, and more strategic AI initiative.
Thrive’s 4 Phase Approach to AIWhile the potential of AI is vast, successful organizational adoption doesn’t happen overnight. Businesses need a clear, structured approach to maximize the value of AI while minimizing risk.
At Thrive, we guide organizations through a 4 Phase Approach to AI that helps align technology with strategy, ensuring security, scalability, and measurable business impact.
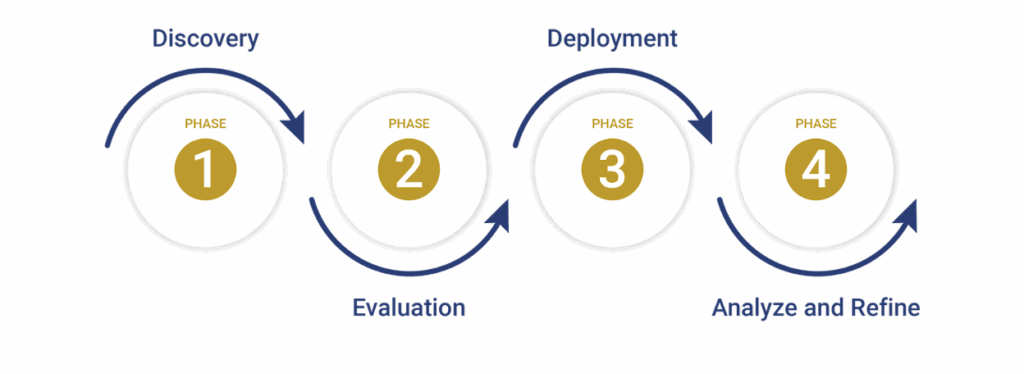
Phase 1: Awareness and Assessment
The first step is understanding what AI can do for your business. This involves:
- Who Owns AI Business Strategy: Establishing clear accountability for AI initiatives. Ownership typically sits at the executive level, but cross-functional involvement from IT, compliance, and business leaders is critical to ensure alignment with overall strategy.
- Identifying Opportunities: Pinpointing processes that could benefit from automation, data analysis, or predictive insights.
- Assessing Readiness: Reviewing existing IT infrastructure, data quality, governance, and security posture.
- Setting Goals: Defining the business outcomes you want AI to achieve, such as efficiency, cost savings, risk reduction, or competitive differentiation.
This discovery phase ensures organizations match AI use cases to real business challenges.
Phase 2: Pilot and Experimentation
Once opportunities are identified, organizations can move into controlled pilots:
- Proof of Concept (PoC): Testing AI solutions on a small scale to measure performance and business impact.
- Stakeholder Buy-In: Getting feedback from executive leadership, IT, and end-users to refine use cases.
- Risk and Compliance Check: Ensuring AI solutions align with industry regulations and corporate governance.
Pilots let organizations experiment without overcommitting resources, while building internal confidence in AI.
Phase 3: Integration and Scaling
With proven pilots in hand, the next step is expanding AI across the enterprise:
- Technology Integration: Embedding AI into existing workflows, applications, and platforms.
- Change Management: Training teams to adopt AI-driven processes and fostering a culture of digital innovation.
- Operational Resilience: Strengthening security, monitoring, and governance frameworks to scale safely.
After integration, AI can shift from being an experiment to a core driver of efficiency, decision-making, and innovation.
Phase 4: Optimization and Evolution
Implementing AI is not a one-and-done measure. The final phase focuses on continuous improvement:
- Performance Monitoring: Tracking KPIs and ROI to ensure AI investments deliver sustained value.
- Feedback Loops: Using real-world results to refine models, retrain algorithms, and improve accuracy.
- Future-Readiness: Staying ahead of AI advancements and adapting solutions to new market and compliance demands.
This final phase ensures your AI investment continues to evolve alongside your business and the technology landscape.
How Thrive Can Help
AI adoption requires more than tools; it demands expertise, governance, and security. Thrive’s managed AI services leverage both our dedicated AI team members and our expertise in managing IT infrastructure, compliance frameworks, and cyber resilience to deliver enterprise-grade AI solutions to small and medium-sized businesses. With Thrive’s support, your business can pursue its AI initiatives with confidence.
Contact Thrive today so we can assess, pilot, and scale AI solutions tailored to your business goals.
What is an AI Policy (and Top Considerations)Artificial intelligence (AI) is transforming how businesses operate from automating tasks to enhancing customer experiences and improving decision-making. This push comes with new risks: data misuse, compliance violations, algorithmic bias, and even reputational damage.
That’s where an AI policy comes in.
An AI policy is a formal framework that defines how your organization adopts, manages, and governs AI. It sets the rules of the road, ensuring AI initiatives align with business goals, comply with regulations, and operate responsibly. For mid-market organizations, developing an AI policy isn’t optional, it’s an essential step to unlocking AI’s potential without exposing the business to unnecessary risk.
Why Your Business Needs an AI Policy
AI adoption is growing rapidly, but many companies are moving faster than their policies. Without usage guardrails in place, AI projects can:
- Introduce hidden bias into decisions
- Create compliance or legal liabilities
- Expose sensitive data
- Reduce trust with customers, employees, and partners
An AI policy establishes clarity and confidence, so leadership teams can innovate without fear of unintended consequences.
Top Considerations When Developing an AI Policy
1. Align AI Use with Business Objectives
Your AI policy should connect directly to strategic priorities. Whether your focus is operational efficiency, customer experience, or risk management, the policy should define acceptable use cases and ensure they support measurable business outcomes.
2. Define Governance and Accountability
AI isn’t a “set and forget” solution. Assign ownership across IT, compliance, and business units for overseeing your organization’s AI systems. Policies should define:
- Who is accountable for AI decision-making
- How performance is monitored and validated
- Escalation processes if issues arise
3. Prioritize Data Protection and Security
AI depends on data, and mishandling that data is one of the biggest risks. Your AI policy should align with existing data governance frameworks and cover:
- Data collection, storage, and retention practices
- Access controls and usage permissions
- Compliance with industry regulations (GDPR, HIPAA, GLBA, etc.)
4. Address Ethics and Bias
Fairness and transparency are critical to building trust. Your AI policy should outline standards for testing algorithms, monitoring for potential bias, and providing explanations for automated outcomes when possible.
5. Support Training and Adoption
Employees will likely interact with AI day to day. Include guidance on training, awareness, and expectations to ensure AI is used consistently and responsibly across the organization.
6. Plan for Continuous Review
AI technologies change quickly. Policies must be dynamic, with regular review cycles to update guidelines as new tools, risks, and regulations are released.
Lay the Groundwork for Responsible AI
An AI policy is more than a compliance checklist. It’s a foundation for responsible innovation. By defining governance, security, ethical standards, and alignment with business goals, organizations can leverage AI with confidence.
At Thrive, we help businesses build AI strategies and policies that balance innovation with governance, so you can achieve growth while minimizing risk. Contact Thrive today if your organization is ready to take its first step in AI governance, our team can guide you through it.
Is Your Business Ready for AI?Artificial Intelligence (AI) has quickly become a core component of modern IT strategy, helping to drive operational efficiency, enable smarter decision-making, and transform how organizations deliver value. But before diving into adoption, organizations must take a step back and evaluate whether their infrastructure, processes, and teams are truly ready for AI.
Thrive’s AI Readiness Playbook was designed to help organizations navigate that journey by breaking down the essential components needed to implement AI responsibly and effectively.
Here are some of the key highlights from the guide:
1. Start with Strategy, Not Technology
AI should never be a solution in search of a problem. We emphasize beginning with business goals, such as identifying where automation, analytics, or generative tools can drive measurable outcomes. Whether that’s improving customer engagement, enhancing cybersecurity, or optimizing workflows, every AI initiative should be mapped directly to strategic objectives.
2. Strengthen Your Data Foundation
AI is only as strong as the data it’s built on. A reliable, clean, and secure data infrastructure is the cornerstone of AI readiness. Thrive helps organizations assess data quality, implement governance frameworks, and ensure compliance with evolving privacy and security regulations. Investing in this foundation early prevents inaccuracies and bias from undermining AI performance.
3. Ensure Infrastructure Resilience and Scalability
AI workloads demand flexibility and computing power. The Playbook highlights the need for a hybrid and cloud-ready infrastructure capable of scaling with demand. Thrive’s modern IT architecture ensures businesses can securely manage high-performance workloads, from real-time analytics to AI-powered automation, without compromising performance or cost efficiency.
4. Address Security and Compliance from the Start
As AI models handle sensitive data and automate critical processes, cybersecurity can’t be an afterthought. AI systems have the same foundational security needs as traditional infrastructure, so you have to start with security by design, from implementing access controls and encryption to monitoring for adversarial attacks. Thrive’s comprehensive managed security services ensure organizations stay protected while remaining compliant with regulatory frameworks.
5. Empower Your Workforce with Skills and Governance
Successful AI adoption depends on people as much as technology. Thrive recommends establishing clear governance and training programs to help teams understand how to safely and effectively use AI. From executive leadership to IT operations, everyone plays a role in ensuring responsible AI usage and mitigating risks.
6. Partner with Experts to Accelerate Readiness
AI readiness isn’t a one-time checklist; it’s an ongoing evolution. Partnering with a trusted managed security services provider (MSSP) like Thrive gives businesses access to the right tools, expertise, and guidance to deploy, secure, and scale AI initiatives responsibly.
Get Started with Thrive
AI offers incredible potential, but only for organizations with the right foundation. Thrive’s AI Readiness Playbook can help your business identify opportunities, address gaps, and design a secure, scalable AI roadmap that supports innovation without adding risk.
3 Reasons PE Firms Bring in ThrivePrivate equity firms move fast, and their portfolio company IT strategy needs to keep up. Whether executing a platform acquisition or optimizing an add-on, PE firms face high pressure to increase operational efficiency, reduce risk, and drive value creation in their PortCos within tight timeframes. That’s why many bring Thrive into their acquisitions as their trusted MSSP.
Here are three key reasons why:
1. Thrive Accelerates IT Maturity Post-Acquisition
After the deal closes, Thrive helps PE-backed firms scale their IT infrastructure quickly and effectively. Many acquired companies operate with outdated systems, unmonitored networks, or insufficient cybersecurity controls. Thrive assesses their current IT environment, identifies gaps, and deploys best-in-class solutions tailored to their needs.
From modernizing email and collaboration tools to securing endpoints and implementing compliant backup solutions, Thrive delivers rapid transformation that supports long-term scalability and productivity. Thrive’s onboarding process is structured to minimize disruption and deliver immediate value.
2. Thrive Reduces Risk, Fast
Cybersecurity risk can jeopardize the success of an investment. Thrive’s approach gives firms and their portfolio companies the protection needed to meet today’s cyber insurance requirements, industry regulations, and board expectations.
Thrive begins with a comprehensive risk assessment and then implements critical safeguards such as endpoint protection, DNS filtering, and 24x7x365 monitoring through its security operations center (SOC). Thrive also provides services like vulnerability scanning, patch management, and autonomous penetration testing to uncover and resolve issues before they cause damage.
3. Thrive Scales with the Portfolio
As PortCos grow through their own acquisitions, they need an IT partner that can scale up to meet their evolving needs. Thrive delivers tailored and flexible solutions and deep industry expertise to support each stage of the investment lifecycle.
Thrive brings M&A experience, repeatable integration processes, and a centralized support model that simplifies IT operations across multiple companies. Thrive’s team includes specialists in compliance, cloud migration, data protection, and more, allowing PE firms to focus on strategic growth while we manage the technology.
PE firms need IT to be an enabler, not an obstacle, for their portfolio companies. That’s why they bring in Thrive to modernize infrastructure, reduce risk, and build a strong foundation for growth, without delay. Contact Thrive today to learn more about how we help private equity teams enable their PortCos to execute with confidence and deliver measurable results.
The Connection Between Data Quality and AI ResultsArtificial intelligence (AI) is rapidly becoming a cornerstone of mid-market organizations’ IT strategy as they look to set their AI ambition. But executives who are having trouble seeing value from their investments are quickly realizing what data scientists and machine learning engineers have already learned: the success of any AI initiative is only as strong as the quality of the underlying data that feeds it. AI models are not inherently “intelligent;” they are systems designed to detect patterns, make predictions, and automate decisions based on available data. Poorly governed or low-quality data directly undermines the reliability of those outcomes.
Why AI Depends on Data Quality
AI platforms require structured, reliable, and accessible organizational data. Without them, even the most advanced models risk becoming a liability rather than an asset. Consider:
- Security analytics: If logs are incomplete or lack normalization across sources, AI-driven detection tools may miss lateral movement or create false positives, which will overwhelm the SOC.
- Forecasting models: Inconsistent data schemas across ERP, CRM, and supply chain systems can distort predictions, eroding confidence in decision-making.
- Automation initiatives: Duplicate or misclassified customer records can create friction and errors in automated workflows.
In each case, AI outcomes reflect not the sophistication of the model, but the hygiene of the data feeding it.
Characteristics of High-Quality Data
For an AI program to be a foundation for business growth, it must be accurate, scalable, and secure. Organizations should assess data based on these characteristics:
- Accuracy & Integrity: Validation checks and referential integrity controls ensure models train on factually correct information.
- Completeness & Coverage: Gaps in transaction logs or customer records reduce the model’s ability to generalize effectively.
- Timeliness & Latency: Streaming pipelines, real-time ingestion, and batch refresh schedules aligned with business needs maintain relevancy.
- Accessibility & Governance: Metadata management, cataloging, and API-based access allow AI workloads to securely query the right data at the right time.
The Risks of Poor Data Management in AI
Businesses that accelerate AI adoption without first addressing data quality expose themselves to significant risk. Operational inefficiencies often emerge as models trained on biased inputs drift quickly, requiring constant retraining that undermines ROI.
From a compliance perspective, frameworks such as GDPR, HIPAA, and DORA demand transparent data lineage and governance; incomplete or undocumented datasets may fail third-party audits and lead to costly penalties. Unreliable AI outputs can also misguide leadership, eroding organizational trust in both IT and the AI program itself. If organizations build an AI agent specifically for cybersecurity purposes, a lack of data visibility to the training data can create gaps that will cause cybersecurity attacks to go unflagged
Building a Data-First AI Strategy
AI strategy should not begin with vendor selection or model design, but with a data readiness assessment. Organizations should establish:
- Data Architecture Reviews: Evaluate whether current data pipelines, warehouses, and lakes are optimized for AI workloads.
- Data Governance Frameworks: Implement stewardship roles, lineage tracking, and retention policies to align with compliance mandates.
- Security by Design: Protect sensitive data with encryption, access controls, and zero-trust principles while enabling AI processing.
- Continuous Data Quality Monitoring: Deploy tools for automated profiling, cleansing, and anomaly detection to prevent degradation over time.
AI Success Starts with Data Discipline
The path to AI value creation runs directly through data governance and quality. Organizations that enforce discipline in architecture, governance, and ongoing monitoring will see models that deliver trustworthy insights, regulatory compliance, and tangible business impact. Contact Thrive today to ensure that your AI initiatives scale securely and effectively.
First Steps for Planning AI StrategyExecutives across industries are under pressure to determine how AI fits into their growth strategies, competitive positioning, and long-term value creation. Yet, for many mid-market organizations, the challenge isn’t why AI matters, it’s how to start planning effectively.
At Thrive, we see too many businesses rushing into AI without a clear strategy, only to waste resources or introduce risk. Instead, the first steps toward AI adoption should be deliberate and business-driven; research has shown that 95% of AI projects fail to hit any cost savings or revenue generation.
1. Start with Strategic Objectives
AI is a means to an end, not the end itself. Before considering tools or platforms, identify the outcomes that matter most to your business, such as:
- Improving profitability by reducing operational inefficiencies.
- Enhancing customer retention through personalized experiences.
- Strengthening resilience by predicting and mitigating risks.
Framing AI use in terms of measurable business objectives can make sure that every initiative contributes to growth or stability, not just experimentation.
2. Evaluate Organizational Readiness
AI success isn’t just about data or algorithms, it’s about whether your business is prepared to integrate new capabilities. Key business-focused questions to ask:
- Do you have leadership buy-in for AI initiatives?
- Who will lead this AI initiative?
- Are your teams aligned on where AI can deliver value?
- Do you have a plan for risk management, governance, and compliance?
An AI readiness assessment prevents wasted effort and helps prioritize realistic organizational initiatives.
3. Identify High-Value, Low-Risk Use Cases
The best AI strategies begin with targeted wins. Instead of trying to transform your organization overnight, focus on initiatives that are impactful yet manageable. For example:
- Streamlining back-office operations to reduce costs
- Enhancing customer support with AI-driven insights
- Leveraging predictive analytics to improve decision-making
These focused, smaller projects prove value, generate momentum, and help build internal trust and executive buy-in for AI.
4. Establish Guardrails Early
AI introduces new risks for organizations, such as bias, misinformation, compliance gaps, and security vulnerabilities. Leaders should define governance policies before scaling adoption. This means setting clear standards for:
- Responsible data usage
- Alignment with regulatory requirements
- Transparency and accountability in automated decision-making
By putting governance first, businesses avoid reputational risk and maintain stakeholder confidence.
5. Invest in People and Change Management
AI won’t succeed in isolation. Leaders of organizations must equip their teams with the knowledge, training, and confidence to use AI effectively. More importantly, they need to foster a culture where AI is seen as a tool to enhance decision-making and efficiency, not replace jobs. Successful AI strategies balance technological investment with organizational alignment.
An AI strategy is not a technology roadmap, but a business roadmap powered by technology. By starting with strategic objectives, aligning your organization, selecting the right use cases, embedding governance, and supporting your people, you can create a foundation for sustainable, value-driven AI adoption.
Thrive helps mid-market businesses take their first steps with AI the right way: focused on outcomes, compliance, and long-term growth. Check out our ebook on AI strategy or contact Thrive today to learn more about how AI fits into your business strategy, from planning to execution.
Enhance Email Security and Deliverability with DMARCEmail has always been a key tool for businesses to communicate internally and with customers. However, as reliance on email continues, cybersecurity risks have become more frequent and sophisticated. Phishing, spoofing, and other email-based attacks have continued to evolve, posing a significant threat to organizations. Thrive’s DMARC (Domain-based Message Authentication, Reporting, and Conformance) solution addresses these challenges, offering a powerful tool to enhance email security and deliverability while meeting regulatory compliance requirements across industries.
What Is DMARC?
DMARC is an email authentication protocol designed to protect domain owners from unauthorized use of their domains, such as spoofing or phishing attacks. It ensures that legitimate emails reach their intended recipients while blocking potentially harmful emails from landing in employee and customer inboxes. DMARC builds upon the email validation systems SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) which help identify illegitimate emails. DMARC delivers policy-based directives on what email systems should do with flagged messages so that they are quarantined, rejected or delivered in real-time. By using DMARC, businesses can improve email deliverability and reinforce trust in their communications.
Thrive’s DMARC Solution: Simplified Management and Unmatched Value
Thrive’s DMARC solution is more than just a security enhancement—it’s a streamlined, cost-effective service that integrates seamlessly into Thrive’s broader platform. Here’s why it stands out:
1. Platform-Agnostic and Independent
Thrive’s DMARC solution works across all email platforms—whether you use Microsoft 365, Google Workspace, or another hosting service. It is also independent of your existing email security system. No matter if your organization is using Proofpoint, Mimecast, Avanan, Microsoft Defender, or any other system, the Thrive DMARC solution is compatible.
2. Centralized Reporting for Better Analysis
The solution collects the DMARC reports sent back by your email recipients, and centralizes the data in one place for analysis. Easy-to-read reports will highlight undelivered email with recommendations for how to correct any potential misconfigurations. Once security controls are tuned, the service will provide guidance for implementing stricter settings to prevent email spoofing.
3. Regulatory Compliance Made Simple
With growing regulatory requirements, such as PCI DSS, and policy changes by email providers like Google and Yahoo, implementing DMARC has become essential for businesses. Thrive’s solution helps businesses stay ahead of these requirements, ensuring compliance and maintaining a competitive edge.
Who Benefits from Thrive’s DMARC Solution?
This service is tailored for organizations at any stage of DMARC implementation:
- No Setup: Businesses that haven’t implemented DMARC and need expert guidance.
- Incorrect Setup: Those who attempted setup but left gaps that compromise effectiveness.
- Monitor Mode: Organizations that set DMARC in monitoring mode but haven’t moved to full enforcement.
- Fully Set Up: Companies with DMARC fully deployed who need ongoing management and reporting.
Why Act Now?
Failing to implement or properly manage DMARC can significantly impair your business’s ability to communicate effectively internally and externally. Emails not reaching their destinations can lead to missed opportunities, diminished customer trust, and potentially harm your organization’s reputation. By deploying Thrive’s DMARC solution, you:
- Enhance email security
- Achieve better email deliverability
- Ensure compliance with evolving standards
- Gain peace of mind with expert management
Thrive’s Role in Your Email Security Strategy
Thrive’s DMARC solution is not just about protecting your domain from misuse—it’s about empowering your business. With centralized management and expert support, Thrive ensures that your DMARC setup is optimized, compliant, and continuously monitored.
Start safeguarding your email communications today. Contact Thrive to learn more about how our DMARC solution can secure your domain, improve deliverability, and keep your business running smoothly.
