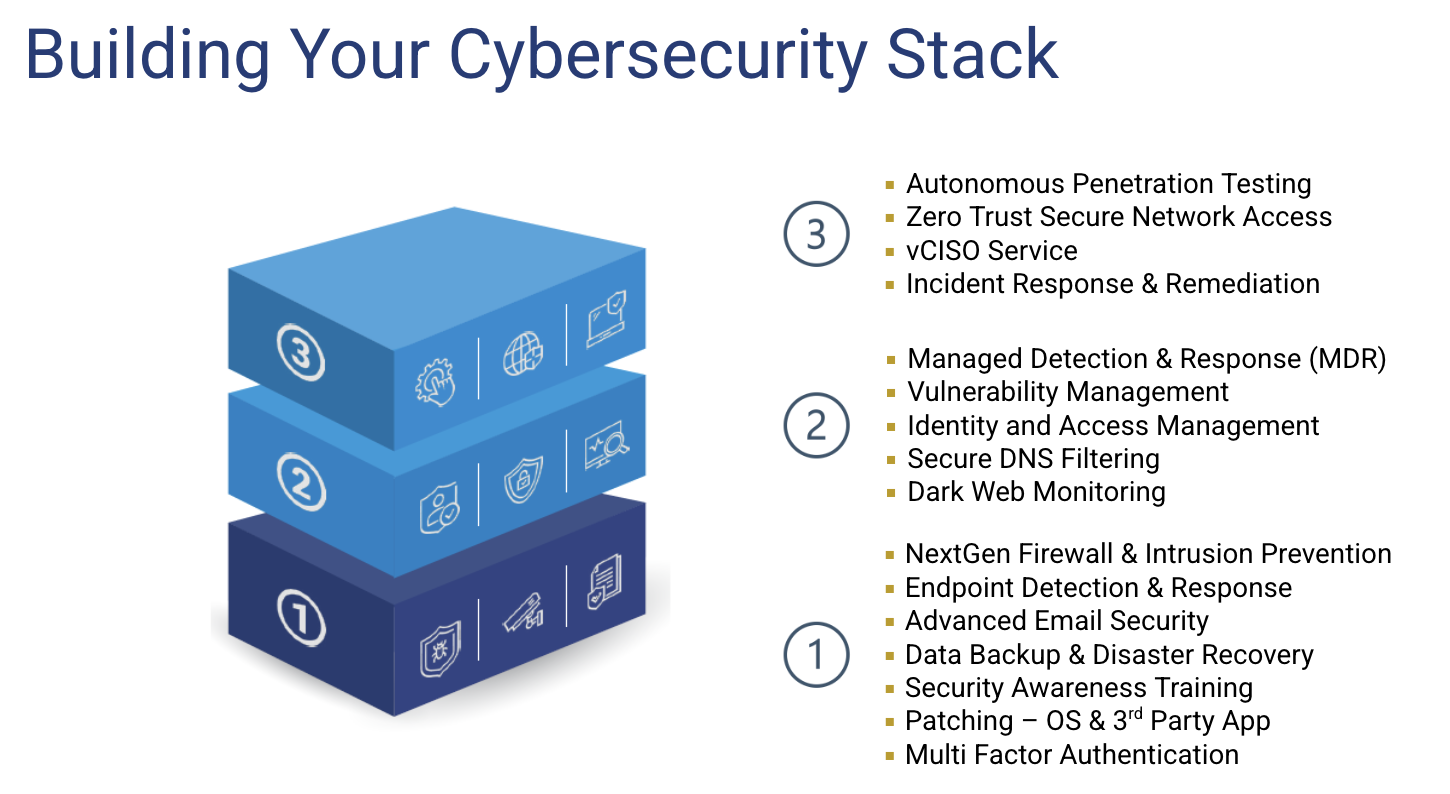
Network Detection and Response
Modern Threats Don’t Stand Still
Thrive’s network detection and response solution adds another, dynamic layer to your infrastructure security by looking at communication patterns for all your assets.
What Is NDR
Modern infrastructure is sprawling, complex, and usually encompasses multiple physical and virtual environments. Security approaches try to address potential threats by looking at different attack points – such as endpoint devices like laptops or system hardware like firewalls – and track the status of those assets.
Technology like SIEM analyzes audit logs and tries to identify atypical or problematic events; endpoint detection and response (EDR) uses agents on workstations and servers to track packages, processes, services, and other telemetry. However, these focus on specific locations within the infrastructure. What about the things that are communicating to (or through) those assets?
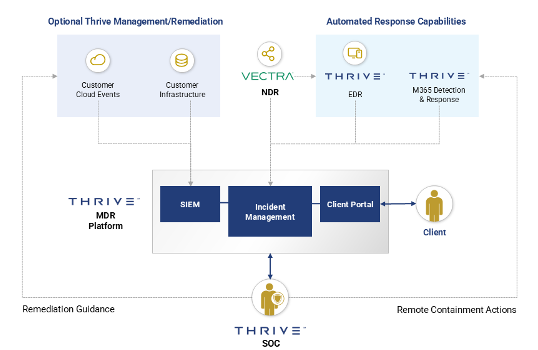
The Role of Network Communication
The IT network is, simply, the connection and communication between different interfaces. These can be elements within the local network or it can be elements outside the local network that connect to those assets. Internal communication is called east-west, while external communication is called north-south.
While network communication may leave some trace in access logs, in general, these connections are transient and leave little evidence behind. However, while they are occurring, network traffic can offer clear insight into malicious attackers lurking in your infrastructure or attacks in progress.
Using AI Analytics to Cut Through Network Chatter
Insight doesn’t come from data. Insight comes from analysis and pattern recognition. There are hundreds of thousands of network connections in and out of your infrastructure every day. The critical aspect of NDR is how it cuts through all of the noise to identify seemingly benign yet atypical behaviors, a single needle in a haystack of requests.
Thrive’s NDR solutions use specially trained AI to analyze all of your network connections and requests in real time. This sophisticated approach to data analysis does three things:
- Recognize attacks in progress
- Identify compromised accounts
- Triage flagged requests to prevent false positives

What Our Customers Are Saying
One of the main benefits for me and my relationship working with Thrive is the trust that I have in the company as a whole. I know if I need assistance with something that may seem small to others but is a huge deal to me that they will be there to assist me with it. Trust to me is a major factor in any relationship.
Bernadette Flaherty
IT Manager, Erland
Why a Layered Security Approach Matters
While the attack time is long, the amount of time it takes for you to be at risk is very, very short. The most common attack vector is through compromised credentials. On user tests, when someone receives a phishing email, it usually takes about 30 seconds for them to click a link and another 20 or so to enter their credentials, meaning on average it takes less than a minute for your infrastructure to be vulnerable to attack.
This is why security has to be a layered approach. Covering only part of your infrastructure or relying on a single tool isn’t enough. Security as a practice has to encompass user training and awareness, routine testing, and combined processes and technologies at ever level of your tech stack.
This is the Thrive difference: crafting tailored solutions that account for your people, workflows, and resources.
Contact Us
Ready to take the next step to protect your organization’s security. Talk to an expert today.