NextGen IT Solutions for US Government Agencies
How Thrive Helps State and Local US Government Agencies
Public sector organizations searching for managed cybersecurity, Cloud, and IT services and consulting for local and state governments choose Thrive. With headquarters in Boston, Massachusetts, and over 20 office locations across the United States, many clients are also the communities that we call home.
Thrive is invested in our clients’ cybersecurity, resiliency, and prosperity, and bring over 30 years of state and local government and education (SLED) public sector knowledge to support your daily needs and long-term IT planning and development.
Modern and secure SOC 2 Type II and PCI DSS-compliant data center facilities across the United States provide government sector clients with flexibility, performance, and continuous availability and uptime for critical data and systems. Managed Cloud backups and disaster recovery services are designed to align with government sector standards and compliance needs.
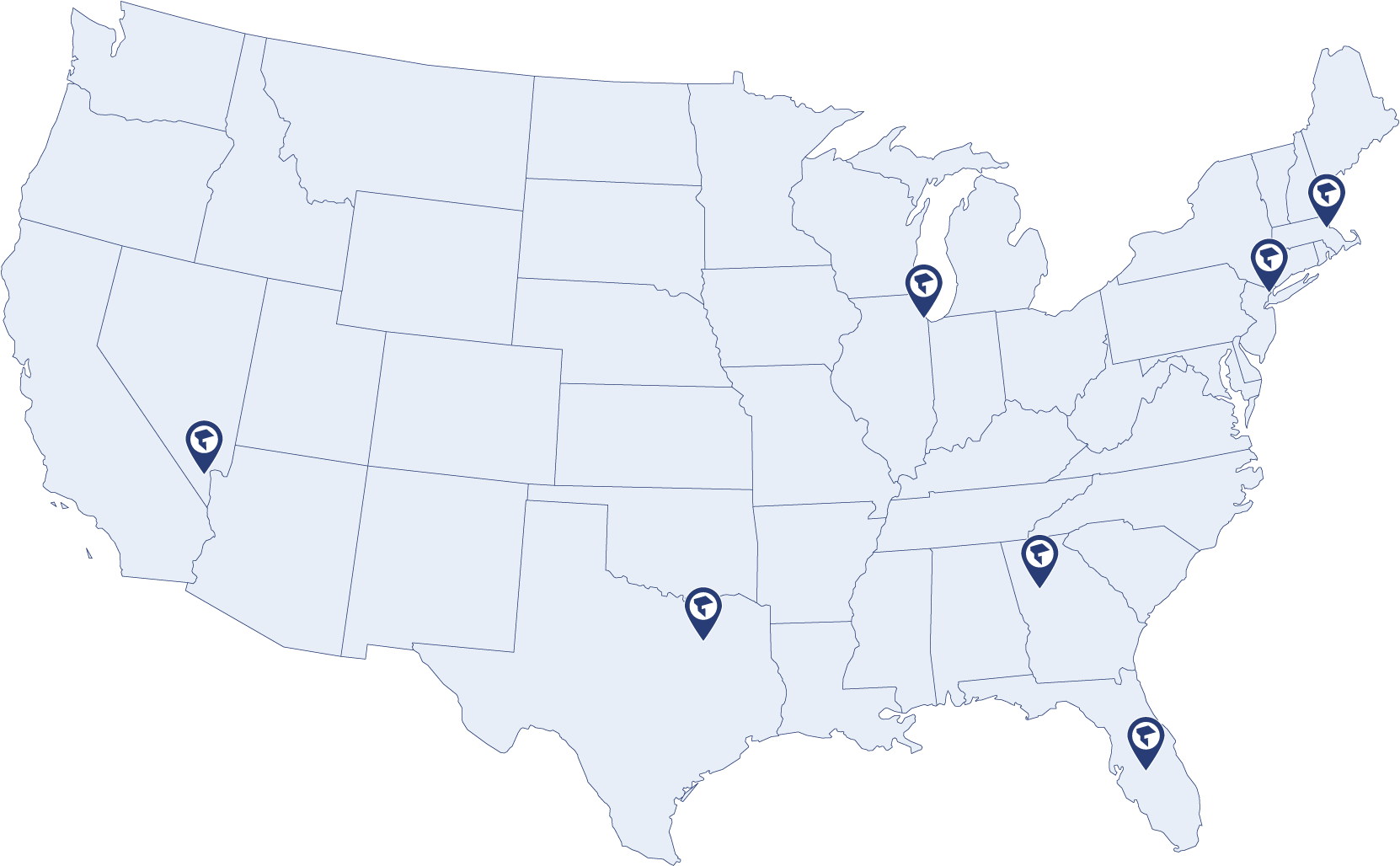
US Data Center Locations
With 7 locations to choose from and growing, clients can find a local managed Private or Public Cloud solution in:
- Florida
- Georgia
- Illinois
- Massachusetts
- Nevada
- New Jersey
- Texas
IT Solutions for US Government Agencies
Thrive is proud to offer managed IT services for government organizations like:
- Cities, Towns, Counties, and Municipalities
- State Government Departments
- County Clerk of Courts
- Judicial Circuits and Counsel
- Law Enforcement Agencies
- Corrections Services
- Emergency Services (Fire/Rescue)
- Hospitals and Healthcare Providers
- Public and Private Education
- Tax Collectors and agencies
- Utilities Service Providers
- Airports and Transportation Terminals
- GovCon suppliers and businesses


US IT Compliance Support for Government Agencies and Contractors
Thrive has dedicated CJIS specialists and CJIS-compliant services for Florida and Alabama-based agencies, as well as CMMC Registered Practitioners (RP and RPA) ready to assist Federal government contractors and suppliers with regulatory compliance needs. Expertise in serving clients with the HIPAA Security Rule, GLBA, and other IT compliance requirements make Thrive the logical choice for US public sector agencies searching for a managed IT provider that understands your challenges, and helps you unlock new opportunities.
Why US Government Agencies and Contractors Partner with Thrive
- Modernize IT Infrastructure
- Auditing and Reporting
- Data Privacy and Security
- Operational and Expenditure Efficiencies
- IT Consulting and Assessments
- Regulatory Compliance:


Driving Better IT Outcomes for SLED Organizations
“Thrive’s professional guidance and real-life examples have been critical in helping us make informed decisions about our cybersecurity.”
Chris Craft
St. Lucie County
Florida Tax Collector
NextGen Technology Outsourcing for the US Government Sector
- Security Operations Center (SOC)
- Managed Detection & Response (MDR)
- Endpoint Detection & Response (EDR)
- Incident Response & Remediation
- Autonomous Penetration Testing
- End User & Workstation Security
- Disaster Recovery as a Service
- Private and Public Cloud
- Microsoft Azure Cloud
- Productivity / M365
- Copilot Planning & Readiness
- Security for M365 and Azure
- Email Security
- Dark Web Monitoring
- Advanced DNS Security
- Zero Trust Secure Access
- Identity & Access Management
- Global Network Management
- Server and Workstation Patching
- Managed IT Support
- 24×7 Performance Monitoring
- IT Operations Assessment
- Cyber Risk Assessment
- vCIO & vCISO Advisory Services
Government Purchasing Vehicles Awarded to Thrive
Thrive has been recognized as a preferred or awarded vendor by these Government purchasing vehicles:

Municipal and Local Government Agencies
Thrive’s teams of Cloud, cybersecurity, and IT support professionals live and work in many of the American communities that we are honored to call long-time clients.
Cities, towns and municipalities, and related agencies work with Thrive to modernize aging IT infrastructure, shore up defences against cyber threats and downtime risks, and expand their pool of resources and expertise that would otherwise be out of reach for most public sector IT budgets.
Advisory and IT consulting services, including on-demand vCIO and vCISO team members, are available to help assess current realities and build a practical roadmap. Supporting audits and reporting, alongside savvy mentoring and preparation, equip our clients’ IT leaders with the confidence and compelling evidence to win over stakeholders and funding commitments.
State Government Agencies and Federal Requirements
State Government Departments, Divisions, and Judicial Circuits with State Attorney and Public Defender offices all partner with Thrive for Next-generation outsourced managed IT, Cloud, and cybersecurity. Thrive’s advisory and IT consulting services are customized for each client and provide reliable assessments and cyber resiliency planning.
Clients appreciate the guidance and support they receive from Thrive’s multi-disciplinary teams dedicated to helping agencies and GovCon businesses with regulatory and compliance matters.
Statutes and frameworks are often mandated at the state or federal level and can overwhelm even seasoned clients with their complexities and gravity.
Thrive has developed an exceptional bench of CJIS, CMMC, SEC, and other compliance-focused IT professionals that are ready to assist you on your IT compliance journey from start to finish.

International Government Regulations and Considerations
Many international regulations have impacts on American businesses already operating in or looking to expand into other markets. Thrive is a global company, with offices, experts, and clients located in the USA, Canada, the United Kingdom, and the APAC region.
Share where you’re doing business today or where you’re planning to expand, and we’ll connect you with the right resources.
Key Regulations in The United States Government Sector
Our American-based compliance teams are trained to help your agency or government contracting business to meet and maintain compliance with policy areas from regulations such as:
CMMC
CMMC is a framework established by the U.S. Department of Defense (DoD) to ensure contractors and subcontractors protect sensitive federal contract information (FCI) and controlled unclassified information (CUI). It applies to all businesses within the DoD supply chain, requiring certification at one of five levels based on the sensitivity of the information handled.
CJIS
The CJIS Security Policy sets standards for protecting Criminal Justice Information (CJI) within American law enforcement and public safety sectors. It applies to Government agencies, contractors, and vendors that access, process, or store CJI.
HIPAA
The HIPAA Security Rule establishes standards to safeguard electronic protected health information (ePHI) data in the U.S. healthcare industry. Entities covered by the Security Rule include healthcare providers, insurers, and clearinghouses.
GLBA
The Gramm-Leach-Bliley Act (GLBA), also known as the Financial Services Modernization Act of 1999, is a federal United States law that requires companies that offer consumers financial products or services to explain their information-sharing practices and safeguard confidential and sensitive data. Banks, insurance companies, mortgage brokers, and other businesses offering financial products or services are subject to GLBA. These regulations work in tandem with State Financial Privacy Laws and State Data Breach Notification Laws.
Resources
Support your organization’s need for long-term flexibility and reliability with managed NextGen IT solutions from Thrive.
Contact Thrive Today
No matter where your agency is its digital transformation journey, Thrive can help.



