Blog
Learn how Thrive’s Proactive Cybersecurity Response Team Prevents Ransomware Attack

Ransomware has become a constant threat in today’s world of emerging technologies. Threat actors are increasingly using this attack method to cripple corporate infrastructures, extract large sums of money as payment, and damage their reputation.
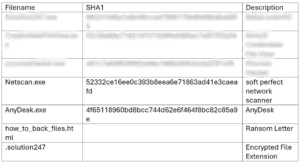
Thrive’s Cybersecurity Incident Response Team (CIRT) recently prevented a threat actor from accomplishing those goals. A client who had not invested in Endpoint Detection and Response (EDR) solutions, was attacked. Despite the lack of endpoint tooling and customer documentation, Thrive’ s CIRT quickly responded to the developing incident, gathered crucial forensic artifacts, and launched an in-depth investigation. Thanks to CIRT’s methodical investigation it was determined a threat actor had encrypted numerous files, appending the extension .solution247 to each file.
Additionally, every file directory contained a file named how_to_back_files.html, which included an extortion message from the attackers, detailing their ransom demands and instructions for potentially recovering the encrypted data.
Further analysis revealed that Remote Desktop Protocol (RDP) connections to the impacted server came from VPN during the period of compromise. A review of the firewall logs indicated that the user account used to authenticate to the VPN was compromised through a distributed brute-force attack.
Using the low privilege VPN credentials, the adversaries were able to gain access to a domain controller and file server. Once they obtained access to these systems, they quickly installed AnyDesk, a commercially available remote access tool, likely used to establish persistent access. Shortly after, they executed tools such as CredentialFileView, SoftPerfect Network Scanner, and Process Hacker.
The SoftPerfect Network Scanner was found to have accessed a file at the following location: C:\Users\Redacted\Documents\anetscan (6)\anetscan (5)\anetscan (4)\automim\!logs\Passwords.txt. This file was part of an automated process for scanning and attempting authentication on other network resources. Evidence of access attempts to the NTDS.dit, a “crown jewel” asset for an attacker, was also discovered during this period. Subsequently, the threat actors successfully gained access to several administrator accounts
A file named Solution247.exe was downloaded to C:\Users\Redacted\Documents\. Solution247.exe—was identified as the BabyLockerKZ ransomware variant—was extracted. Prior to the file encryption, there was evidence of exfiltration from the compromised server to an IP address associated with the internet service provider 59telecom.ru over port 21 (FTP). Upon execution, Solution247.exe added itself to the current user’s Run key to maintain persistence with the following command:
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v sm /t REG_SZ /d “C:\Windows\System32\ Solution247.exe” /f
The ransomware then forcefully terminated critical processes essential for system operation and security, including SQL Server, Windows Defender, user login processes, and print services:
cmd.exe /c taskkill /F /IM sqlservr.exe /T
taskkill /F /IM msmpeng.exe /T
taskkill /F /IM winlogon.exe /T
taskkill /F /IM spoolsv.exe /T
Next, Solution247.exe disabled key services using net stop commands, disrupting crucial system operations, including antivirus and backup systems:
net stop “Windows Defender Antivirus”
net stop “SQL Server (MSSQLSERVER)”
net stop “Windows Backup”
After disabling these defenses, Solution247.exe began encrypting files across multiple drives using cipher.exe commands:
cipher /e /s:C:\
cipher /e /s:D:\
To further hinder recovery efforts, it deleted volume shadow copies with.
vssadmin delete shadows /all /quiet
Despite the threat actors’ efforts to hinder recovery, the client had invested in Thrive’s Veeam backup solution. After receiving a detailed timeline of the intrusion, they were able to confidently restore their data and ensure the integrity of the impacted servers.
Indicators of compromise:
Would you like to learn more about the indicators of compromise we found? Reach out today and we will provide the full list to you.
Today’s complex cyber threats require a multi-solution approach combined with advanced skill sets and real-time, 24/7 monitoring. Thrive’s leading security platform integrates best in breed technologies, analyzing attack data with AI and certified security analysts to prevent the impacts from threats allowing you to focus on critical business outcomes.
Our security team combines the power of automation for rapid response and remediation with the expertise of our staff to address complex issues intelligently. We are ready to help.
